Cyberthreats against software supply chains moved to the forefront of cybersecurity concerns a year ago when revelations of the attack on software maker SolarWinds emerged.
Now one security researcher – Moshe Zioni, vice president of security research for application risk management startup Apiiro – is predicting that supply chain attacks will likely peak in 2022 as organizations leverage new products that will help them better detect these attacks.
Vendors like Apiiro have been working to protect enterprises against supply chain attacks that have been on the upswing for several years, with bad actors lured by the success of these campaigns and the money that could be made, Zioni told eSecurity Planet.

Now more products are coming to market that make it easier for enterprises to detect such attacks and protect themselves against them, Zioni said.
“Our ways of data mining and positioning the data security lifecycle against supply chain attacks have gained some ground over the past couple of years, more than before,” he said. “Supply chain attacks are something that have been on the rise for a few years now. This is more than a cat-and-mouse game. It’s been a detection game for us for the better part of 10 years-plus for the application security realm.”
Supply Chain Attacks an Ongoing Threat
Going into 2022, threat groups will continue to target the supply chains of enterprises, which give them new avenues into greater numbers of potential victims. However, improved defenses are beginning to shift the advantage to end customers.
“At some point we’re going to see a peak,” Zioni said. “Then through some detections and preventions [offerings from vendors] like a Apiiro, you will see much more detection and we will bring the upper hand back to the developers and enterprises.”
That would be good news for enterprises, which have been on edge since details of the SolarWinds attack, perpetrated by the Russia-linked cyberthreat group Nobelium, broke late in 2020. The hackers inserted malicious code into updates of SolarWinds’ Orion IT monitoring software, putting at risk thousands of customers that had downloaded the updates (though the actual number of businesses hacked through the Sunburst malware was fewer than 100).
Also read: Best Backup Solutions for Ransomware Protection
2021 a Tough Year in the Supply Chain
Throughout 2021, there were myriad other supply chain attacks, including one in which another Russia-based threat group, REvil, leveraged a vulnerability in software company Kaseya’s remote monitoring and management (RMM) software to launch a ransomware attack that impacted thousands of its customers.
Both incidents were part of a larger global push by cybercriminals targeting weaknesses in supply chains. Cybersecurity company BlueVoyant found in a report released in October that 97 percent of respondents to a survey said their companies had been negatively impacted by a cybersecurity breach in their supply chains and 93 percent said they had been affected by a direct cybersecurity breach due to weaknesses in their supply chain.
In addition, 91 percent said that their budgets for third-party cyber-risk management would increase in 2021. In a statement, Adam Bixler, global head of third-party cyber risk management at BlueVoyant, said that “even though we are seeing rising awareness around the issue, breaches and the resulting negative impact are still staggeringly high, while the prevalence of continuous monitoring remains concerningly low.”
Third-party cyber-risk must become a priority at companies, Bixler said.
With more tools coming to market that add security layers to DevOps and application environments, organizations will have the tools to make it a priority, Zioni said. That will be important given the rapid changes happening in those areas that are helping to fuel the increase in supply chain-based attacks, he said.
Further reading: Best Third-Party Risk Management (TPRM) Tools for 2022
Agile Development, Standards Help Fuel Attacks
Factors adding to supply chain risk include the increasingly agile mindset of developers and the expanding use of cloud-native applications. A major focus of DevOps is on speed – think of continuous integration/continuous deployment (CI/CD) – and enterprises are wary of putting in place security measures that slow down the process. The agile process also means being more reliant on third parties, Zioni said. However, that doesn’t mean that everything is inherently less secure.
“Because of this distributed way of trusting and to use third parties, you actually have a much more robustness in terms of data protection, in terms of compliance and in terms of what kinds of capabilities those kinds of options offer for DevSecOps and for developers and application security managers,” he said. “But on the other hand, it also means that this is a new complexity that security practitioners have been dealing with for the past few years. Those are the things that actually made the shift in terms of how enterprises can protect the lifecycle.”
There also is greater standardization and regulation that must be met by enterprises, and cybersecurity vendors also need to catch up to those in order to detect and prevent supply chain attacks.
Further reading: How to Comply with GDPR, PIPL and CCPA
Bad Actors Have Early Advantage
The combination of the sophistication of attackers and the work enterprises need to do to put in the necessary controls to prevent the attacks means that the scales are tipped in the direction of the bad actors still, at least for the moment.
“Statistically speaking, attackers will have some kind of upper hand,” Zioni said. “It doesn’t mean that they will succeed every time, but this is statistically speaking. It will still be the case until the gap is bridged as soon as possible by enterprises. That means that after this peak, it will plateau and the upper hand will be back to the enterprises’ hands.”
Once this happens, there will be fewer supply chain attacks in the coming years, he said, adding that he was reluctant to say when this will happen. However, he is sure it will.
New Supply Chain Security Tools on the Way
Vendors are launching more products that offer greater capabilities to detect cyberthreats – including supply chain threats – and touch on areas like inventory and asset discovery, CI/CD security, continuous compliance and code risk assessments. All of those are part of Apiiro’s platform as well, Zioni said.
The company launched in 2019 and Zioni signed on in September after almost four years as director of threat research at Akamai Technologies. Apiiro’s Code Risk Platform is designed to offer a range of capabilities in a single place, creating less complexity and greater integration. He said the goal is to be a one-stop shop for enabling organizations to control and manage their products. There is both development and infrastructure profiling.
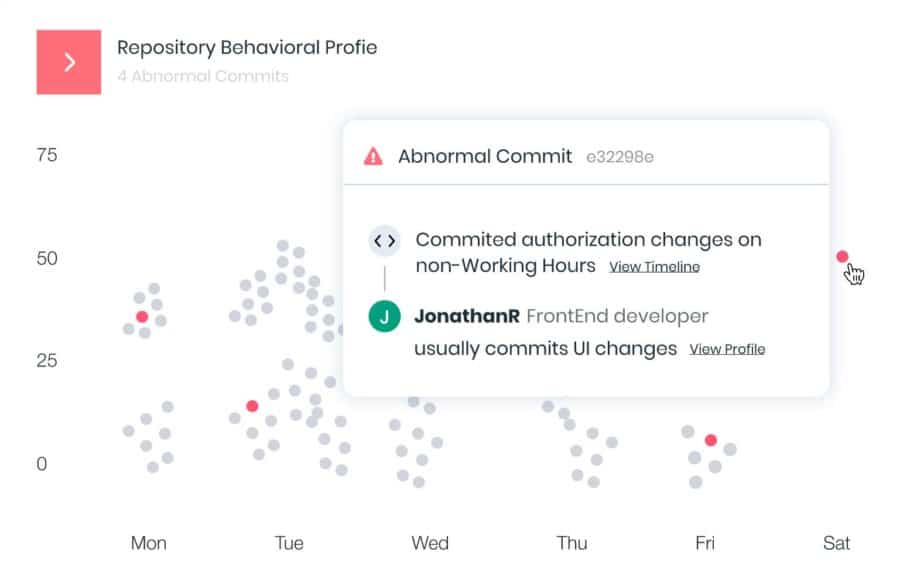
In February, in the wake of the SolarWinds attack and with $35 million in funding raised in October 2020, Apiiro unveiled two offerings designed to detect and block such attacks. One is to defend against build-time code injection, which was central to what the SolarWinds attackers did. Another product is aimed at detecting abnormal behavior in developer identities, helping organizations identify compromised accounts and insider threats.
In addition, the company in November rolled out its Dependency Combobulator, an open-source toolkit that is designed to detect and prevent dependency confusion attacks, a growing threat in supply chain attacks. With dependency confusion attacks, cybercriminals deliver malicious components into the open-source ecosystem by tricking end users, developers and automation systems into installing a malicious dependency package that has the same name of the privately-used packages they normally leverage.
Further reading: Top Code Debugging and Code Security Tools








