The attacks on SolarWinds and Kaseya over the past year put a spotlight on how an attack on a single company can have downstream consequences on the victim’s partners and customers.
The attackers used the entry they gained into the companies to fan out into businesses and government agencies, stealing data and forcing some to have to temporarily shut down their operations, causing tens of millions of dollars in damages.
They took advantage of the weaknesses inherent in an increasingly connected world and highlighted the need for companies to not only ensure their own security but also look at the security of their vendors and put into place necessary protections.
A report issued this week by research and data science firm Cyentia Institute put the threat of such multi-party cyberattacks into stark relief. Looking at the 50 largest multi-party breaches in recent years, the organization found that the median number of organizations impacted by these security events – dubbed “tsunamis” – was 31, though as many as 800 such secondary victims were caught up in the attacks.
Collateral Damage
In addition, the median cost of these tsunamis was $90 million. By comparison, the typical cybersecurity incident runs about $200,000, highlighting the massive costs associated with large attacks that ensnare multiple organizations.
“The fact that multiple parties contribute to multiplying costs is far from shocking,” the report’s authors wrote. “But it still serves as a reminder of risk accumulation. We tend to focus on assessing ‘our’ (own) risk and don’t always consider ‘our’ (collective) risk.”
For the report, Cyentia used information from insurance provider Advisen’s Cyber Loss Data, which the authors said contains almost 100,000 cyber events collected from various publicly verifiable sources. To come up with the list of the 50 largest tsunamis, Cyentia pulled together the largest 30 multi-party cybersecurity incidents measured by total reported financial losses, the 30 largest involving the number of data records affected, and the 30 largest as measured by the number of organizations involved.
All multi-party incidents were considered for the list and the top 50 were selected based on the combined totals and the information available.
Further reading: Best Third-Party Risk Management (TPRM) Tools of 2021
Ransomware a ‘Heavyweight’
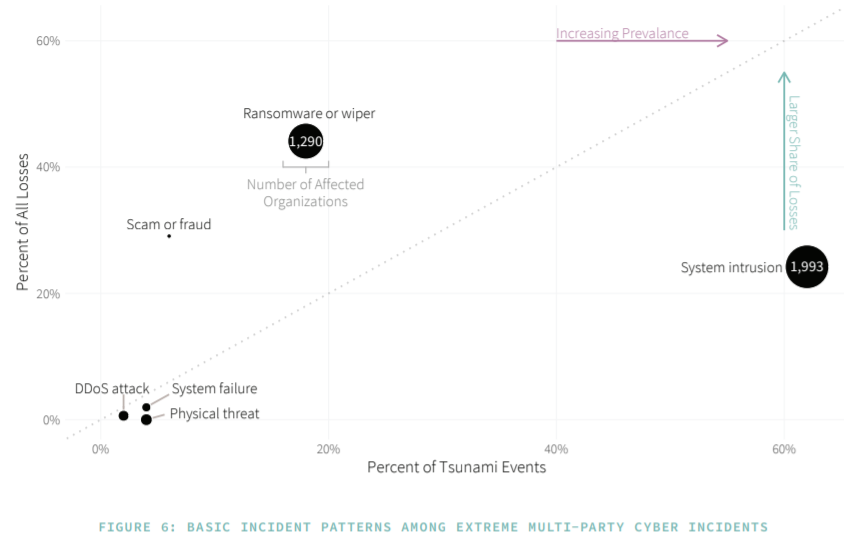
Among the information gleaned from the report was that system intrusions – attempts at compromising systems, applications or networks by such means as deploying malware, elevating privileges and subverting logical access controls – were the most common type of incident and accounted for 57 percent of the downstream organizations impacted. Ransomware was a distant second in terms of frequency but was the most financially damaging, responsible for 44 percent of the financial losses of all 50 major cybersecurity incidents.
“Add the 37% of secondary victims to that rap sheet, and it is apparent that ransomware is a heavyweight among major multi-party cyber loss events,” according to the report.
See also: Best Ransomware Removal and Recovery Services
Supply Chains are Targets
Supply chain compromises led to $7.4 billion in losses, the largest share of recorded financial losses and the largest number of secondary victims.
The report puts an emphasis on the need for organizations to ensure that they not only are protected against cyberattacks but also if their vendors are compromised. The most common situation was the compromise of multi-party data that had been aggregated by the initial victim organization.
“The systems of downstream parties are not breached in this scenario, but those organizations nevertheless suffer various consequences as owners of the disclosed data,” the authors wrote. “This is doubly unfortunate for the original data owners because they have little ability to protect the data once it has been shared. The best protection is to choose data custodians wisely and check regularly to ensure that they uphold their end of the bargain.”
Other situations include shared systems, where systems owned or used by downstream companies also are breached. In some cases, all entities share centralized applications, so a breach of one expands to include others. In others, interconnectivity and trusted access can lead to malware being propagated to other systems or organizations.
“The lesson here is that trusted systems easily become busted systems without proper 3rd party access controls,” the authors wrote.
See also: The Software Supply Chain: Where Security Starts
Multi-Party Cyber Attacks Mean Big Payoffs
Cybercriminals will continue to target victims that will yield the largest financial gains,” Stephen Banda, senior manager for security solutions at cybersecurity vendor Lookout, told eSecurity Planet.
“For this reason, targeting large complex supply chains is a sound strategy for bad actors,” Banda said. “These ecosystems of supplier relationships have many interfaces and points of collaboration that increase the attack surface. The multi-party scenario is a cyber attacker’s dream.”
When targeting supply chains, they grow the size and scale of the attack, which in turn increases the profitability of an attack, he said. The more credentials and other data that can be stolen, the better for an attacker.
Joseph Carson, chief security scientist and advisory CISO at ThycoticCentrify, told eSecurity Planet that companies need to understand that the nature of cyberattacks is changing and that they need to adapt accordingly, including how they address the security of vendors and other partners.
“Today, organizations have less control and visibility over the actual security that supply chains have put in place,” Carson said. “For the most part, this tends to only be covered in legal contracts, rather than a true security risk assessment. Organizations must prioritize privileged access security to reduce the risks exposed in their supply chain security.”
Lookout’s Banda said organizations should consider moving to the cloud to leverage the security solutions there that offer tightly integrated data protection capabilities. Collaboration is at the heart of vendor relationships and supply chains, so the security of data is key when shared externally.
“A first step is to ensure you can classify your data so that you know what is sensitive or confidential and then be able to apply protection, such as encryption or step-up authentication, in real-time,” he said. “Ultimately, organizations need to get visibility into the users, devices and data that are connecting to their network and applications. Once centralized visibility is obtained, policies can be put in place to ensure that data is protected wherever it goes.”
Don’t Forget the Basics
Banda and others also said that companies need to pay attention to the basics as well.
“Organizations need to have comprehensive security hygiene in place,” he said. “Strong passwords, multifactor authentication and a routine vulnerability and patch management practice go a long way.”
Michael Isbitski, technical evangelist at Salt Security, agreed.
“No longer can organizations delay patching critical, known vulnerabilities because of concerns over outages, the impact on production users, or the loss of oversight of a system,” Isbitski told eSecurity Planet. “Unpatched systems are leaving important elements of the IT stack vulnerable, especially APIs, which attackers are increasingly targeting these days since they route traffic directly to valuable data and services.”
He also noted that there may be cloud services – and in turn, APIs and data – that employees or their partners work with that enterprises are unaware of, opening up another avenue of multi-party risk, he said.







