-
How Steganography Allows Attackers to Evade Detection
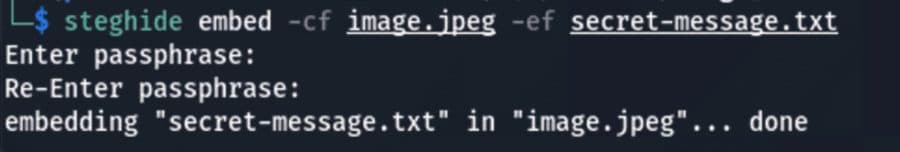
Steganography, derived from Greek words meaning “covered” and “writing,” has been used for centuries to hide secret messages inside regular documents. In cybersecurity, steganography mainly consists of hiding malicious payloads or secret information inside seemingly harmless files such as images, PDFs, audios, videos, and many other document types. While steganography is often considered something of […]
-
Feds Warn About Critical Infrastructure Ransomware Attacks, Vulnerabilities
Ransomware attacks on critical infrastructure and a surge in exploited vulnerabilities are getting the attention of U.S. cybersecurity agencies, which highlighted the threats in a pair of warnings issued in recent days. The FBI and U.S. Secret Service issued a detailed advisory on the BlackByte Ransomware as a Service (RaaS) group, which has attacked critical […]
-
AI & ML Cybersecurity: The Latest Battleground for Attackers & Defenders
Machine learning (ML) and artificial intelligence (AI) have emerged as critical tools for dealing with the ever-growing volume and complexity of cybersecurity threats. Machines can recognize patterns to detect malware and unusual activity better than humans and classic software. The technology also predicts potential attacks and automatically responds to threats by identifying specific trends and […]
-
SIEM vs. SOAR vs. XDR: What Are The Differences?
Endpoint security and firewalls are two foundational elements of enterprise security, but with remote work, IoT devices and other technologies expanding the boundaries of the network edge, centralized management and response tools increasingly have become a core security component too. These central management tools – SIEM (security information and event management), SOAR (security orchestration, automation […]
-
How Hackers Compromise the Software Supply Chain
It seems like a week doesn’t go by without a new vulnerability demonstrating the fragility of the software interdependencies that make up the software supply chain. A large part of software development leverages the benefits of open-source platforms and third-party vendors to deliver results on time. A wide range of people and organizations maintain those […]
-
Open Source Sabotage Incident Hits Software Supply Chain
An astonishing incident in recent days highlights the risks of widespread dependence on open source software – while also highlighting the free labor corporations benefit from by using open source software. Marak Squires, an open source coder and maintainer, sabotaged his repository to protest against unpaid work and his failed attempts to monetize faker.js and […]
-
How to Use MITRE ATT&CK to Understand Attacker Behavior
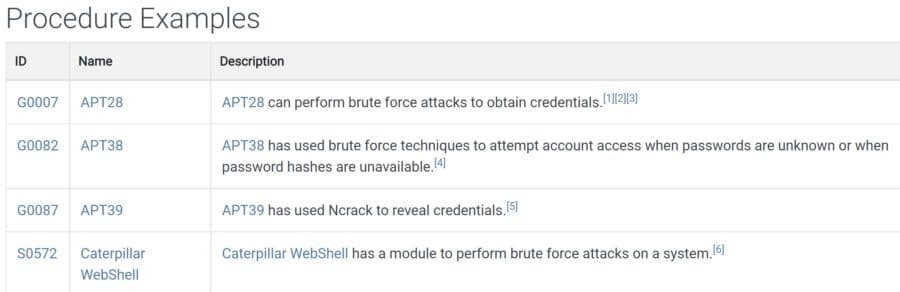
MITRE ATT&CK (“miter attack”) is an up-to-date and widely-used knowledge base that focuses on how attackers think and operate. It’s based on practical use cases, so companies can better evaluate security issues and get examples of common tactics and techniques used by threat actors. ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) documents adversary behaviors to […]
-
How Hackers Use Payloads to Take Over Your Machine
A payload is a piece of code that executes when hackers exploit a vulnerability. In other words, it’s an exploit module. It’s usually composed of a few commands that will run on the targeted operating system (e.g., key-loggers) to steal data and other malicious acts. Most operations use payloads, but there are a few payload-less […]
-
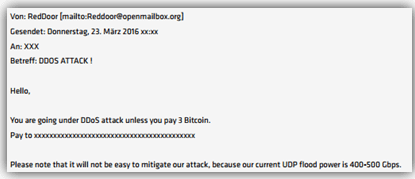
DDoS Attacks Skyrocket, Kaspersky Researchers Say
Distributed denial of service (DDoS) attacks soared in the third quarter, giving organizations yet another cyber threat to worry about. Kaspersky researchers reported that total attacks were up by about a third from the second quarter. Even the slowest days saw 500 DDoS attacks; the busiest day, Aug. 18, saw a whopping 8,825 attacks. Kaspersky […]
-
MITRE, CISA Reveal Dangerous Hardware & Software Vulnerabilities
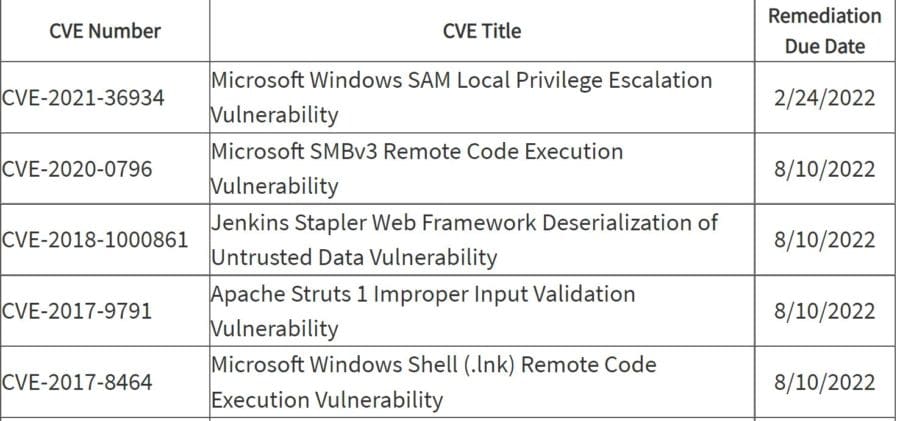
It’s been an active week for security vulnerabilities, with MITRE and the U.S. Cybersecurity & Infrastructure Agency (CISA) revealing hundreds of critical vulnerabilities. CISA ordered federal agencies to patch a list of nearly 300 vulnerabilities, and encouraged private organizations to fix them too. CISA said the list will be updated as any vulnerability meets three […]
IT Security Resources
Top Cybersecurity Companies
Top 10 Cybersecurity Companies
Get the Free Newsletter!
Subscribe to Cybersecurity Insider for top news, trends & analysis