A major Linux vulnerability dubbed “Dirty Pipe” could allow even the least privileged users to perform malicious actions.
Researcher Max Kellermann of Ionos revealed the new vulnerability earlier this week. The name is reminiscent of the “Dirty Cow” vulnerability discovered in 2016 that allowed attackers to gain root access on any Android Phone regardless of the OS version, but Dirty Pipe could be even easier to exploit than its predecessor.
Kellermann managed to exploit the Linux kernel bug, which allows any user, including the least privileged ones such as the “nobody” account, to perform malicious actions such as adding an SSH-key to the root user’s account to access the server remotely with full privileges.
Also read: Top Vulnerability Management Tools
What is the Linux Nobody Account?
Unix systems have traditionally had a dedicated user called nobody for specific operations with the NFS (Network File System).
This pseudo-user is the least privileged account; it does not have any password and literally owns no files. Indeed, the PoLP (principle of least privilege), a fundamental zero trust security principle, dictates that a user be able to access only the information and resources they need.
A vulnerability that allows the least privileged accounts to gain root privileges is a massive failure for such a prominent operating system as Linux.
How Dirty Pipe Works
The Common Vulnerabilities and Exposures (CVE) report for the vulnerability, CVE-2022-0847, explains how attackers can take advantage of the bug. The term “Pipe” refers to internal mechanisms in the Linux kernel called “pipelines.”
Kellermann found an uninitialized variable in the kernel code that could allow an attacker to overwrite any file’s content in the cache. Of course, there are some conditions, but the attacker does not need write permissions; read access is enough. The bug also affects system binaries and btrfs files.
Indeed, the kernel has permanent access (read and write) to the pages in cache. The kernel always runs with maximum privileges, so there is no verification at this level. It’s the system at its core with hardware access.
The kernel uses flags and pipes to pass data between processes. Kellermann made a proof of concept (image below) for the Linux kernel security team where he created a pipe and filled it with arbitrary data, which activated the PIPE_BUF_FLAG_CAN_MERGE flag and ultimately allowed overwriting of the cached file page.
He noticed some limits, though, as the write could not cross a page boundary, but it was possible to alter files without write permissions, and the modifications could affect all users on the system.
Dirty Pipe does not need the privileges of a legitimate process to write data in files and there’s no time constraint whatsoever.
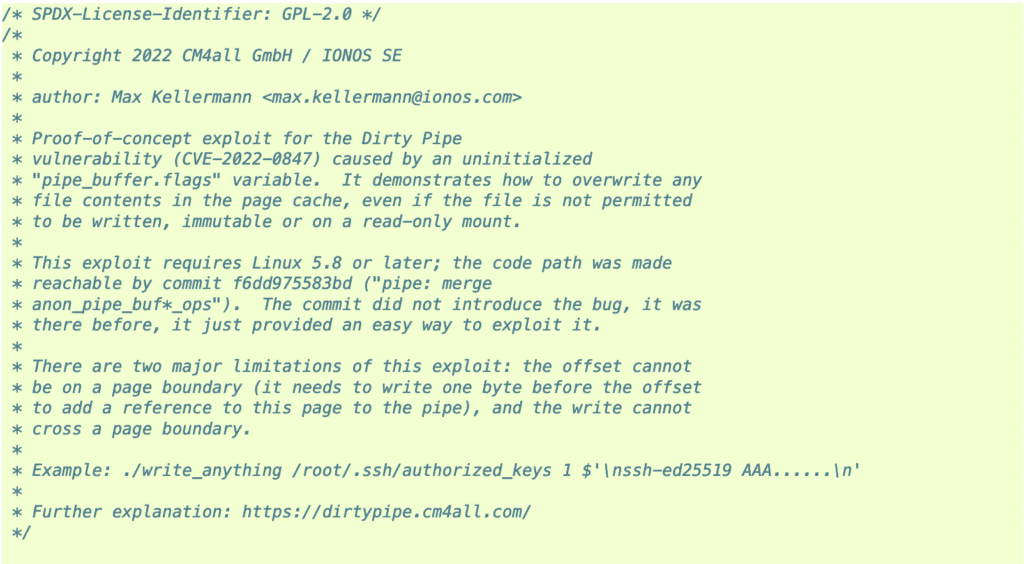
See also: 10 Top Open Source Penetration Testing Tools
What Attackers Could Do with Dirty Pipe
Because it’s easier to exploit than Dirty Cow and it allows escalating privileges to the root level, Dirty Pipe is a high-severity flaw. Hackers would likely use it to perform additional tasks such as modifying common libraries and execute arbitrary code.
The overwrite can either be temporary or permanent and the attacker can modify a system’s binaries that are supposed to be immutable. Any malicious application could elevate its capabilities to a high level without the user’s consent.
This vulnerability is a perfect candidate for lateral movement, arbitrary code execution, and virus propagation.
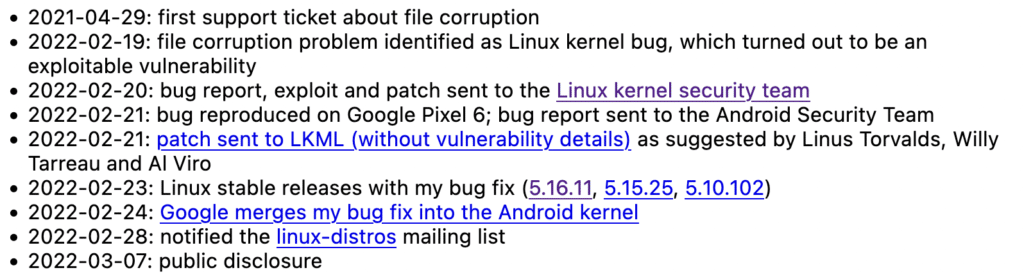
Such a low-level breach is particularly attractive for zero-click attacks. Almost a year went by between the first support ticket for a “simple” file corruption and the final public disclosure:
How to Find and Fix the Dirty Pipe Vulnerability
This critical bug has been patched in Linux. The good news is that the bug was introduced in Linux 5.8, a relatively recent version at the time of writing, so hopefully not as many production servers will be affected.
Users who run the 5.8 version must update quickly, and those who run a more recent version must be on 5.16.11 at least. There is no known mitigation for the flawed kernel code other than updating.
Google patched Android at the end of February with the new kernel code, but Android devices, including the latest Pixel (the bug has been demonstrated on a Google Pixel 6) or Samsung (like Galaxy 2022), are affected. Because the Android ecosystem is highly fragmented, with various alternative systems based on the same Linux kernel, many devices could be running with the vulnerability.
Android users are strongly encouraged to check their OS version under Settings > About phone > Android version.
Read next: Best Patch Management Software




