See our complete list of top database security vendors
Bottom Line
IBM Guardium Data Protection for Databases is a comprehensive data security platform that offers a full range of functions across different environments, from file systems to databases and big data platforms. It probably best fits those enterprises committed to IBM and are familiar with its software and systems, as well as those wishing to add security analytics along with compliance, database protection and encryption within a single product.
Product Description
IBM Guardium offers:
- Discovery, classification, vulnerability assessment and entitlement reporting
- Encryption, data redaction and dynamic masking, combined with real-time alerting and automated blocking for protection of sensitive data
- Activity monitoring and security analytics based on machine learning
- Centralized audit repository for enterprise-wide compliance reporting, performance optimization, investigations and forensics
- Automated data compliance and audit capabilities with Compliance Accelerators for regulations like PCI, HIPAA, SOX or GDPR
Database Security Features Rated
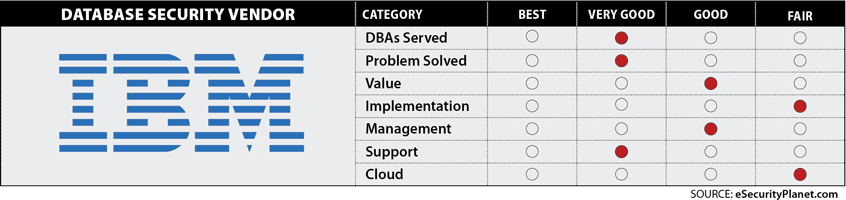
Databases served: Very good
IBM Guardium Data Protection for Databases offers support for all major databases.
Problem solved: Very good
Native-logging approaches to support security and compliance can be operationally complex, and they don’t ensure data confidentiality. Because data is constantly changing, moving, and being accessed by new users, it can be difficult to understand what data you have, how it is being used, and if either of these things puts you at risk from a security or compliance perspective. Insider threats and external attacks also pose dangers to data, but traditional approaches can’t enforce separation of duties, recognize suspicious activity in real time, or help you act.
IBM Guardium Data Protection for Databases provides a data security platform for structured data in databases and data warehouses on major operating systems. It automatically discovers critical data and uncovers risk, providing visibility into all transactions and protocols across platforms and users. It enables protection for sensitive data via real-time capabilities, including monitoring, alerting, blocking and quarantining, along with compliance automation to streamline operations and reduce risk of audit failure. It protects against unauthorized data access by learning regular user access patterns and can provide real-time alerts on suspicious activities. It can dynamically block access or quarantine user IDs to protect against internal and external threats and also helps streamline and automate compliance workflows.
“IBM Guardium is the best way to monitor Database Activity in real time. Reporting, Dashboard, features, integration with SIEM, all these make Guardium the leading security product,” said a consultant in the services industry.
Value: Good
Those already using IBM security products may find high value in terms of packaged pricing for existing IBM customers and ease of integration with IBM software. However, non-IBM users may find it more cost-prohibitive.
Implementation: Fair
Setup for Guardium may be complicated and time-consuming for some users. KuppingerCole also noted some issues with version upgrades.
“Guardium is a very complex [product] and requires time and expertise to be fully utilized,” said an IT security specialist in the finance industry.
Management: Good
KuppingerCole gave Guardium high marks for usability.
Support: Very Good
Cloud Features: Fair
A separate product is needed for the cloud, which protects databases in public and hybrid clouds.
Delivery
IBM’s Guardium solution can be configured for a single database or thousands of heterogeneous databases located across the enterprise. It is available as preconfigured appliances shipped by IBM or as software appliances installed on your platform. Optional features can be added after installation.
Agents
Yes
Pricing
Pricing is based on the number of processor cores, with no publicly released pricing.






