There are few guarantees in the IT industry, but one certainty is that as the world steps into 2022, ransomware will continue to be a primary cyberthreat.
The dangers from ransomware have risen sharply since WannaCry and NotPetya hit the scene in 2017, and this year has been no different. A pair of recent reports underscores just how big that threat is.
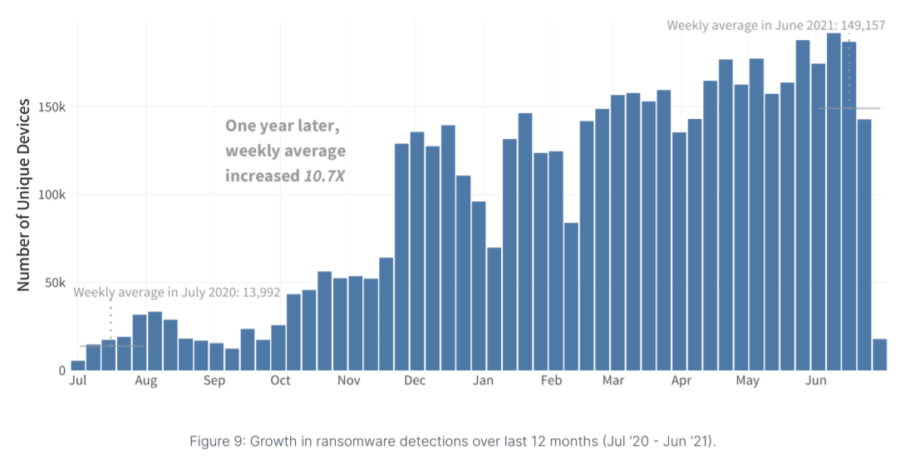
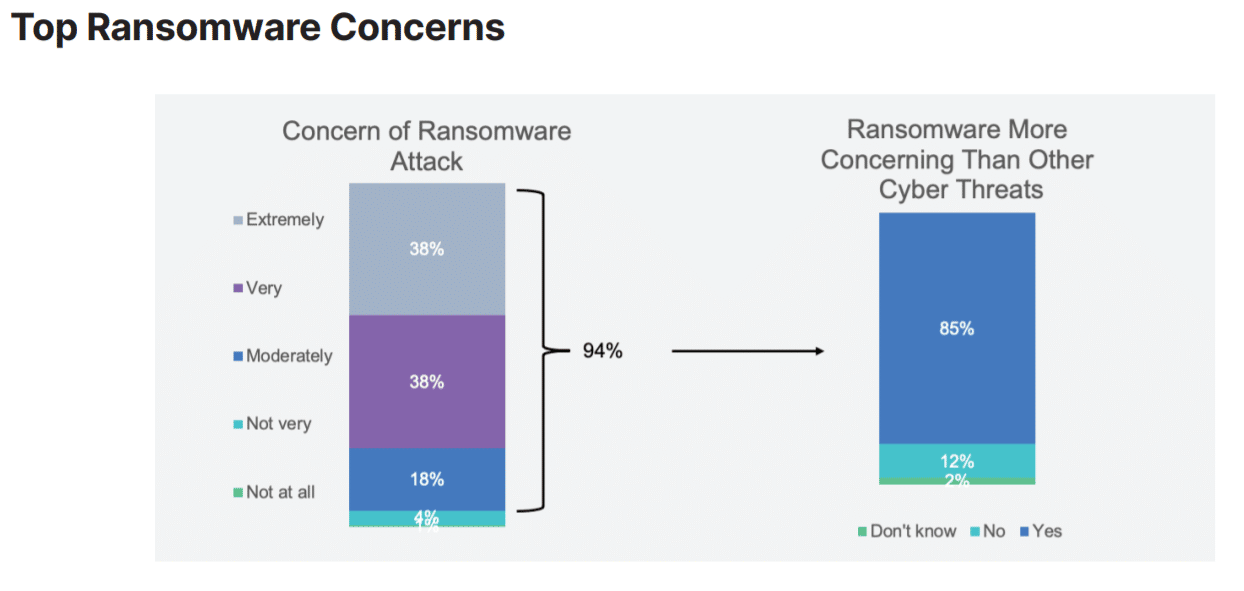
The Global Threat Landscape Report released in August by FortiGuard, the threat intelligence unit of Fortinet, found that the weekly average of ransomware incidents over the previous 12 months had jumped 10.7 times. In Fortinet’s Global State of Ransomware Report in September, two-thirds of companies surveyed had been victims of ransomware attacks and 85 percent said they were more concerned about ransomware than any other cyberthreat.
The sharp increase in ransomware attacks can be attributed to many reasons, from the low level of cyber hygiene of some enterprises to insufficient training and education of employees and patch management issues, according to Derek Manky, chief of security insights and global threat alliances for Fortinet’s FortiGuard Labs. Cybercriminals don’t have to work too hard to get into these systems. When they do, the payoff can be huge, particularly as attackers are setting their sights on larger companies.
Cryptocurrency Fuels Ransomware
One constant in all this will be cryptocurrency, the coin of the realm when it comes to ransomware. The big payoffs, the tendency of most victims to pay the ransom demand, and the money to be made by selling or leasing their malware in the growing ransomware-as-a-service (RaaS) market are all enticements when it comes to ransomware.
The engine that is driving much of this is cryptocurrencies, which have become the way ransoms are paid and are creating the financial foundation for the rapid evolution of the ransomware market, the skyrocketing increases in incidents and the growing numbers of bad actors getting into it, Manky told eSecurity Planet.
“There is no doubt a parallel rise here that we’re seeing,” he said. “It is because of the cash cow. Cryptocurrency really is fueling this in a sense. … If you were to take cryptocurrency away from that, they don’t have a convenient digital platform. They’re going to have to go back to the drawing board. It actually makes their operations more expensive because they need to try to be innovative and get more boots on the ground themselves, just like any business would if they don’t have a platform.”
Also read: The State of Blockchain Applications in Cybersecurity
Crypto Enables ‘Vicious Circle’
Compounding all this is that ransomware is a “vicious circle,” Manky said.
“Once you have that lower state of security and attackers are getting into systems, they’re forcing the hands as a means of enterprises to pay the ransom,” he said. “When they’re paying the ransom using cryptocurrency, it’s encouraging cybercriminals. It’s making their pockets deeper. They don’t have to do a heavy lift to reap profits like they’re doing today.”
The use of cryptocurrencies like Bitcoin, Ethereum and myriad others harkens back to the days of e-gold, another digital currency launched in the 1990s that included the use of online accounts. E-gold use peaked in the mid-2000s before it was suspended in 2009 for legal reasons. As cybercrime became more about monetization, cybercriminals began leveraging the currency for money laundering, fraud and other schemes, he said.
Between the demise of e-gold and the rise of cryptocurrency, bad actors used a number of different ways to move money, including gift cards. They would steal credit cards to buy gift cards and then use those to be cashed out and sold to other people, Manky said.
Also read: Best Ransomware Removal Tools
‘New Form of Crypto-jacking’
The rise of cryptocurrency has had a ripple effect throughout the cybercriminal world, Mansky said. When it first hit the scene, the primary targets of threat actors were the cryptocurrency exchanges themselves. The payouts for hackers were significant; when they hit an exchange, they had access to hundreds of cryptocurrency wallets. However, exchanges began strengthening their security, which made attacking them more expensive, so cybercriminals shifted tactics and began increasingly to target users.
“Instead of robbing a bank, they’re going to the victims themselves,” Manky said.
For the past five years, there has been cryptomining, where bad actors infect systems with malware that leverages the CPUs to mine for coins, essentially crowdsourcing stolen CPU power. More recently has been crypto-jacking, where hackers go directly into a user’s wallet and steal their coins.
This also has shifted the attack vector and opened up end users to greater threats. Attackers no longer are going after one target, he said. They may get into a system to steal digital wallets, but once a system is compromised, it’s open to other attacks.
“It’s a new form of crypto-jacking, essentially, but these are always multi-purpose in a sense, because in order to install that malware, they need what we call a ‘loader,’” he said. “They need a channel into that system. They do this through taking advantage of cyber-hygiene practices, social engineering, all those things we talk about. … But once they’ve infected these systems, they’re compromised, and oftentimes we see a lot of secondary attacks happening. It’s just more and more volume and attack angles.”
Cybercrime Rewarded
Cryptocurrency is enabling cybercriminals to enrich themselves beyond what had been possible. They not only can get paid more money for their actions, but the nature of the payments allows them to add more layers to their operations, making it more difficult to trace payments. It operates like cash in many ways. It makes hiding and laundering the payment easier.
“They can actually print their own money,” he said. “They can print cryptocurrency on a piece of paper. All it is is a big hash address, a cryptographic algorithm, and they can transfer it that way. They can transfer it on a USB stick. They can transfer it physically on a piece of paper and put it into a briefcase and give it to somebody else. Once they have that and the actual keys for it, the money’s theirs. It’s literally physically transferring a wallet to a wallet.”
And they have multiple coins to choose from. They can be paid in Bitcoin and wash the payment by shifting to Ethereum or other exchanges. It makes it difficult for investigators, who “don’t have only one coin to follow,” Manky said, adding that the bad actors “can fork that to 100 different alternate coins.”
Also read: Best Ransomware Removal and Recovery Services
More Sophisticated Cybercriminals
The profits threat actors are reaping are helping to fuel the rise of a more sophisticated and well-armed hacker that is able to build greater expertise on the backend, so they have the capability to launch larger and more complex attacks.
“We see cybercriminals now that lie between what’s typically been nation-state attacks and nation-state capability in terms of sophistication – like zero-days and these sorts of things – that’s now in the realm of cybercriminals, too,” he said.
More money begets more sophisticated operations and methods – think ransomware-as-a-service (RaaS) – and that leads to not only more sophisticated campaigns but also more attackers. With RaaS offered by highly sophisticated groups, less skilled people can leverage such services to launch attacks.
All these cryptocurrency-fueled trends – including the greater sophistication of cybercriminals driven by massive profits, the promise of payoffs and the expanding numbers of threat actors who can launch attacks – has helped fuel the growing global problem of ransomware.
Breaking the Crypto Link
U.S. lawmakers, who this year have become more involved in the problem of ransomware as critical infrastructure – including energy systems as seen in the attack on Colonial Pipeline and food supplies via the campaign as global meat processor JBS – also are seeing the link between ransomware and cryptocurrency.
In October, several senators and representatives sent a letter to the departments of Justice, State and Homeland Security urging them to address – among other things – the role of cryptocurrencies in the rise of ransomware attacks, noting the anonymity the digital currencies give attackers.
It’s important for enterprises to understand that link as well, Manky said. A key is prevention and protections – like backing up data – because once ransomware is in a system, they are forcing many companies that have few other options to pay in cryptocurrency. The exchanges put in protective measures, which drove up the cost to cybercriminals of attacking the exchanges. Given the increasingly distributed nature of IT, it’s important for enterprises to think about prevention and resiliency in a similar way.
“If we don’t do that … it’s going to be very bleak,” Manky said. “It’s going to continue to fund these cybercriminals. Their pockets are going to get deeper. Their capabilities are going to become more sophisticated. They have businesses of their own and like any business, as it grows, they add more and more people, more partners. In the ’90s, it used to be one person. Then it was a handful of people. Now we’re seeing 50, 100 people with partners, even thousands in some of these organizations. That’s a big problem.”
Further reading: Best Backup Solutions for Ransomware Protection





