Several major companies identified and addressed significant security and vulnerability problems in last week’s vulnerability news. SonicWall dealt with a serious access control vulnerability that affected its firewall systems. Traccar fixed severe path traversal flaws in its GPS tracking software. Versa Networks responded to an unrestricted file upload flaw, and Apache resolved an incorrect authorization vulnerability in OFBiz ERP.
Microsoft addressed an ASCII smuggling issue in 365 Copilot, and Google and Fortra issued critical security patches for actively exploited vulnerabilities in Chrome and FileCatalyst Workflow, respectively. To reduce the potential risks, update all impacted software to the most recent version and evaluate your system processes for potential modifications and security enhancements.
August 26, 2024
SonicWall Identifies Access Control Vulnerability
Type of vulnerability: Improper access control.
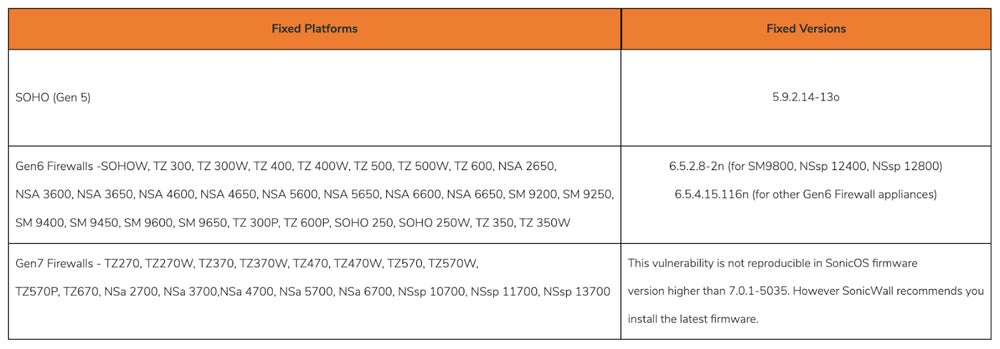
The problem: CVE-2024-40766, a critical access control vulnerability with a 9.3 severity level, was discovered in SonicOS on SonicWall systems. This flaw has the potential to bring down the firewall or grant unauthorized access to resources. Devices running SonicWall Firewall Gen5, Gen6, and Gen 7 are vulnerable to network-based threats that require no user interaction or authentication.
The fix: Upgrade to SonicWall’s firmware updates for Gen 5 (to version 5.9.2.14-13o), Gen 6 (to version 6.5.4.15.116n), and Gen 7 (to any version above 7.0.1-5035). Disable WAN management access or limit firewall management access to reliable sources if instant updates aren’t possible.
Traccar Fixes Path Traversal Vulnerabilities
Type of vulnerability: Path traversal.
The problem: Two major vulnerabilities, CVE-2024-24809 (CVSS score: 8.5) and CVE-2024-31214 (CVSS score: 9.7), were discovered in the Traccar GPS tracking system and affect versions 5.1 to 5.12. These path traversal weaknesses may allow unauthenticated attackers to drop malicious files. This can result in remote code execution under particular conditions, especially when you’ve permitted guest registration.
The fix: Traccar resolved these vulnerabilities in version 6, released in April 2024. It blocks self-registration by default, reducing the attack surface. Users should upgrade to Traccar 6 or higher to reduce the hazards. If you can’t update immediately, disable guest registration and unnecessary write access to prevent exploitation.
Versa Networks Patches File Upload Vulnerability
Type of vulnerability: Unrestricted file upload.
The problem: Versa Networks recently fixed a zero-day vulnerability, CVE-2024-39717, in Versa Director, a platform for controlling SD-WAN. This vulnerability, which existed in the “Change Favicon” feature, enabled threat actors with administrative capabilities to deliver malicious files disguised as PNG images. An APT attacker exploited this vulnerability which affected clients who failed to comply with system hardening and firewall standards.
The fix: This zero-day has been added to CISA’s Catalog of Known Exploited Vulnerabilities. Versa Networks advises clients to update their Versa Director installations to the most recent version to mitigate CVE-2024-39717. Furthermore, users should evaluate and follow the suggested system hardening and firewall rules. To check for exploitation, look for suspicious files in the /var/versa/vnms/web/custom_logo/ folder.
Explore how to prepare for zero-day threats. See how it works and the best practices for organizations to mitigate these attacks.
August 27, 2024
Apache Encounters Incorrect Authorization Vulnerability in OFBiz ERP
Type of vulnerability: Incorrect authorization.
The problem: Apache OFBiz, an open-source enterprise resource planning (ERP) system, contains a critical security weakness (CVE-2024-38856) with a CVSS score of 9.8, which allows unauthenticated attackers to execute remote code via a Groovy payload. This vulnerability, now actively exploited in the wild, affects systems used by big corporations worldwide, possibly compromising their sensitive operations.
The fix: To mitigate CVE-2024-38856, update Apache OFBiz to version 18.12.15. Federal agencies must roll out the revisions by September 17, 2024.
In his expert commentary regarding the issue, Greg Fitzgerald, co-founder of Sevco Security, warns that “even when patches are applied, a more insidious threat exists if companies have lost track of vulnerable instances.” Fitzgerald emphasizes an accurate IT asset inventory, citing that many assets remain uncovered by enterprise patch management and vulnerability management systems.
Microsoft Resolves ASCII Smuggling Vulnerability in 365 Copilot
Type of vulnerability: ASCII smuggling.
The problem: A recently patched vulnerability in Microsoft 365 Copilot allowed attackers to obtain sensitive user information via ASCII smuggling. Attackers could employ invisible Unicode characters to conceal harmful material in hyperlinks and exfiltrate data such as MFA codes. The exploit chain featured prompt injection and automatic tool invocation to find sensitive documents.
The fix: Microsoft rectified the vulnerability after disclosure in January 2024. Enterprises should activate data loss prevention and other security controls to limit hazards in AI technologies such as Copilot. Assess your risk tolerance to avoid data breaches from Copilots and safeguard bots with authentication measures.
Google Reveals Actively Exploited Chrome Flaw in V8 Engine
Type of vulnerability: Inappropriate implementation bug.
The problem: Google addressed an actively exploited security flaw in its Chrome browser, known as CVE-2024-7965. The vulnerability occurs from an incorrect implementation error in the V8 JavaScript and WebAssembly engines, which allows remote attackers to exploit heap corruption using crafted HTML pages.
The bug was found by a security researcher named TheDog. Google hasn’t provided precise data about the assaults, but it has confirmed that the vulnerability is being actively exploited in the wild.
The fix: Google recommends updating Chrome to versions 128.0.6613.84/.85 for Windows and macOS, and 128.0.6613.84 for Linux. This update handles the actively exploited CVE-2024-7965 vulnerability in the V8 engine, preventing heap corruption attacks using manipulated HTML pages.
August 28, 2024
Fortra Patches Critical Access Flaw in FileCatalyst Workflow
Type of vulnerability: Credential exposure.
The problem: Fortra fixed a major vulnerability in FileCatalyst Workflow (CVE-2024-6633) with a CVSS score of 9.8. The vulnerability stems from a static password used for the HSQL database, which allows remote attackers to acquire administrative privileges. This default credential vulnerability jeopardizes program security, integrity, and availability. The issue was made public on July 2, 2024.
The fix: Fortra has published a patch for FileCatalyst Workflow 5.1.7 and later, which addresses the static password issue. Update to this version to mitigate CVE-2024-6633 and fix the high-severity SQL injection bug (CVE-2024-6632) in the setup process.
Cookie theft is another method attackers use to expose your credentials. Reduce this risk, learn how to prevent unauthorized access to your browser, and discover some ways to identify and recover from stolen credential attacks.
August 29, 2024
AVTECH IP Cameras Exploited via Old Command Injection Flaw
Type of vulnerability: Command injection.
The problem: CVE-2024-7029 (CVSS score: 8.7) is a command injection vulnerability in AVTECH IP cameras that permits remote code execution (RCE) using the brightness feature. Threat actors exploited this weakness to incorporate devices into botnets, affecting devices running firmware versions up to FullImg-1023-1007-1011-1009. It was publicly published in August 2024.
The fix: Currently, no patch is available for this issue. Users must examine their camera firmware and seek alternative or extra security steps to reduce risk.
August 30, 2024
Threat Actors Leverage Atlassian Confluence Flaw for Crypto Mining
Type of vulnerability: Remote code execution.
The problem: CVE-2023-22527, a severe RCE vulnerability in Atlassian Confluence Data Center and Server, enables unauthenticated remote code execution. Threat actors use this vulnerability to deploy XMRig miners, target SSH endpoints, and sustain persistence via cron jobs. Exploitation attempts increased significantly between June and July 2024.
The fix: To fix CVE-2023-22527, immediately update the Atlassian Confluence Data Center and Server to the newest versions. This patch addresses the major vulnerability and prevents future exploitation, protecting you against unauthorized remote code execution and illegal cryptocurrency mining.
Exploited Chrome Flaw Triggers Rootkit Deployment
Type of vulnerability: Type confusion.
The problem: CVE-2024-7971 is a high-severity type confusion vulnerability in Chrome’s V8 engine that North Korean actors exploited to execute code remotely. This resulted in the deployment of the FudModule rootkit. Victims of social engineering risked compromised systems and probable data theft.
The fix: Google addressed this flaw, eliminating the risk of remote code execution. To respond to CVE-2024-7971, update Chrome and other Chromium-based browsers to the latest version. Update Windows to solve associated vulnerabilities such as CVE-2024-38106 to avoid further exploitation and rootkit installation.
Read next:
- Vulnerability Recap 8/27/24: SolarWinds, Chrome, AWS
- Vulnerability Management: Definition, Process & Tools
Featured PartnersFeatured Partners: Vulnerability Management Software
eSecurity Planet may receive a commission from merchants for referrals from this website




