This week, some recently patched vulnerabilities got attention because they’re still being exploited, including Apache OfBiz and VMware eSXI hypervisors. The lesson? Even if patches are available, many vulnerabilities are still alive and well within the applications and systems where they originated. That’s a warning to every security team to patch flaws as soon as you learn about a fix because threat actors often exploit them long after being patched.
July 31, 2024
Mirai Botnet Targets Apache OfBiz
Type of vulnerability: Path traversal.
The problem: Apache OfBiz, a Java-based framework for developing enterprise resource planning (ERP) apps, had a path traversal vulnerability in May of this year. The update released for the flaw, which affected OFBiz versions before 18.12.13, fixed the issue. Recently, researcher Johannes Ulrich has seen increased activity against the vulnerability. In particular, the Mirai Botnet has been attacking it.
The flaw is tracked as CVE-2024-32113. Ulrich explained the attacker’s process when exploiting the vulnerability:
“The directory traversal is easily triggered by inserting a semicolon. All an attacker has to find is a URL they can access and append a semicolon followed by a restricted URL. The exploit URL we currently see is:
/webtools/control/forgotPassword;/ProgramExport
“forgotPassword” does not require any authentication and is public. “ProgramExport” is interesting because it allows arbitrary code execution.”
The threat actor would have to use a POST request to exploit the flaw sufficiently, Ulrich said, but they don’t automatically need a request body.
The fix: Upgrade your instance of Apache OfBiz to version 18.12.13.
Android Weakness Exploited by Malware for Over Two Years
Type of vulnerability: Read permission given to malicious applications on Android devices.
The problem: Researchers at mobile security firm Zimperium discovered a malware campaign against Android devices in 2022 and have continued to track the malware since then. The campaign is SMS stealing, targeted at one-time passwords sent through text, so threat actors can use them to access accounts that they aren’t authorized to access.
The zLabs team has identified more than 107,000 malware samples throughout its research of over two years. They found that typically, a victim is fooled into sideloading an application onto the phone through a falsified app store or a similar tactic, and the application requests read permission for SMS messages on the device, which Android allows. Once the malware is on the Android device, it hides in wait and monitors SMS messages, looking for OTPs in particular.
The fix: There is currently no clear patch or redirect from the vendor. Zimperium mentions the importance of increasing enterprise mobile security measures. If you have an Android device, I recommend using an email address to receive one-time passwords instead of a phone number whenever possible.
Apple Fixes Multiple Vulnerabilities in Siri
Type of vulnerability: Access to sensitive information via voice prompts.
The problem: The mobile security issues continue, this time with Apple. The vendor recently patched vulnerabilities in Apple Watch, iPadOS, and iOS that could allow a threat actor to take sensitive data from a locked mobile device. Four of the vulnerabilities were related to Siri, Apple’s voice assistant. Malwarebytes released a security notice emphasizing the dangers of Siri’s ability to respond to voice commands from a locked device screen.
“Apple has restricted these options to stop an attacker with physical access from being able to access contacts from the lock screen and access other sensitive user data,” Malwarebytes said.
The fix: Update to iOS 17.6 or iPadOS 17.6 if you haven’t already.
August 1, 2024
Rockwell Automation Flaw Has Been Fixed
Type of vulnerability: Security bypass.
The problem: Security research firm Claroty found a vulnerability in Rockwell Automation ControlLogix 1756 devices that allowed an attacker to bypass Rockwell’s trusted slot feature. This capability is designed to enforce security on the devices and block communications on the local chassis if they happen on untrusted paths.
Claroty wrote in its report, “The vulnerability we found, before it was fixed, allowed an attacker to jump between local backplane slots within a 1756 chassis using CIP routing, traversing the security boundary meant to protect the CPU from untrusted cards.”
The threat actor needs network access to exploit the vulnerability in the devices. If successfully exploited, the threat actor could bypass the controls and send commands to the PLC CPU, Claroty said. The vulnerability affects ControlLogix, GuardLogix, and 1756 ControlLogix I/O modules.
Claroty disclosed the vulnerability to Rockwell, which then fixed the flaw.
The fix: Rockwell Automation provided the following table with the fixed firmware versions for each affected product.
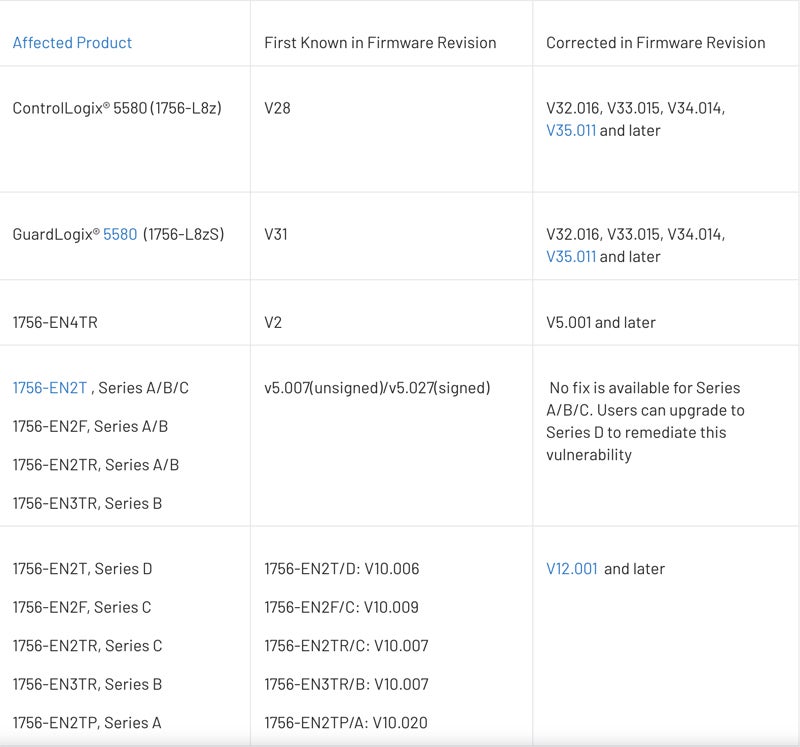
If your team needs more consistent vulnerability information in a faster timeframe, check out our picks for the best vulnerability scanners, which can help you more quickly identify what to patch and protect.
VMware eSXI Vulnerability Still Being Exploited
Type of vulnerability: Authentication bypass.
The problem: A vulnerability affecting VMware eSXI hypervisors was patched recently but has seen multiple ransomware exploits. If a threat actor has sufficient Active Directory permissions, they could get full access to the eSXI host if it had previously been configured to use Active Directory to manage users. According to NIST’s National Vulnerability Database, the threat actor would recreate the eSXI Admin group on AD after it was deleted.
Microsoft researchers discovered the vulnerability and announced it in a research report last week. They disclosed the vulnerability to VMware through a coordinated vulnerability disclosure (CVD).
eSXI hypervisors sometimes host virtual machines, which may support critical workloads and servers. Microsoft said, “In a ransomware attack, having full administrative permission on an ESXi hypervisor can mean that the threat actor can encrypt the file system, which may affect the ability of the hosted servers to run and function. It also allows the threat actor to access hosted VMs and possibly to exfiltrate data or move laterally within the network.”
The vulnerability is tracked as CVE-2024-37085. It has a CVSS score of 7.2 from NIST and a base score of 6.8 from VMware.
The fix: Make sure you’ve patched any eSXI hypervisors, and also use two-factor authentication to make it harder for threat actors to gain unauthorized access.
August 5, 2024
Windows Security Features Have Multiple Flaws
Type of vulnerability: Security bypass.
The problem: Microsoft Windows’ Smart Screen and Smart App Control features have a number of security issues, which Elastic Security Labs reported earlier today. These flaws can lead to “initial access with no security warnings and minimal user interaction,” according to the researchers. No security popups or warnings will alert users that the attacker has gotten access, either, making this challenging to detect.
Smart Screen examines web pages for potential security issues and sends a warning notice to users if it finds one. Smart App Control predicts whether an application is safe to run on the computer system where it’s installed and blocks it if not.
The fix: Elastic Security Labs recommends that teams carefully study downloads happening on their computer system and avoid relying only on OS security features.
Read next:
- Vulnerability Recap 7/29/24 — Multiple Old Security Flaws Reappear
- Best Vulnerability Management Software & Systems in 2024
Featured PartnersFeatured Partners: Vulnerability Management Software
eSecurity Planet may receive a commission from merchants for referrals from this website




