Linux malware is skyrocketing and now surpasses both macOS and Android, according to a new report, suggesting that cybercriminals are increasingly targeting the open source operating system.
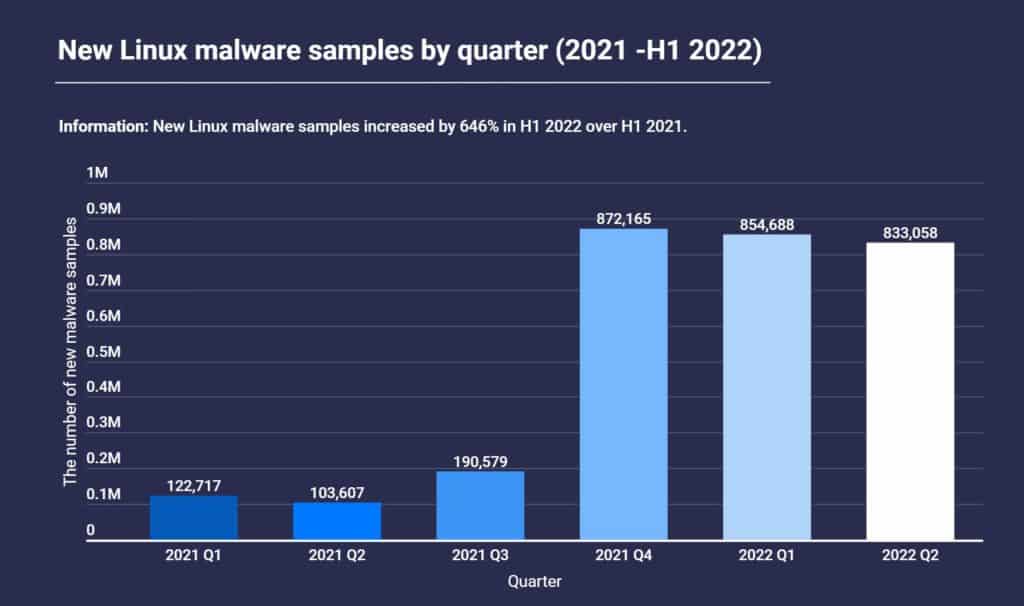
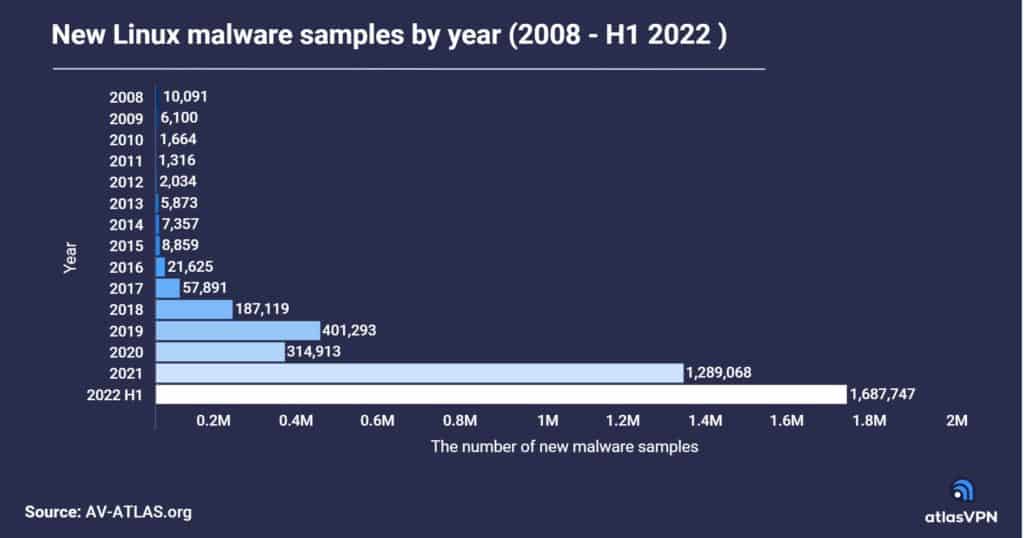
The Atlas VPN report said the number of new Linux malware samples collected soared by 646% from the first half of 2021 to the first half of 2022, from 226,334 samples to nearly 1.7 million.
While the growth has stabilized since hitting a record in the fourth quarter of 2021, the first six months of 2022 have already seen more new Linux malware than all of 2021.
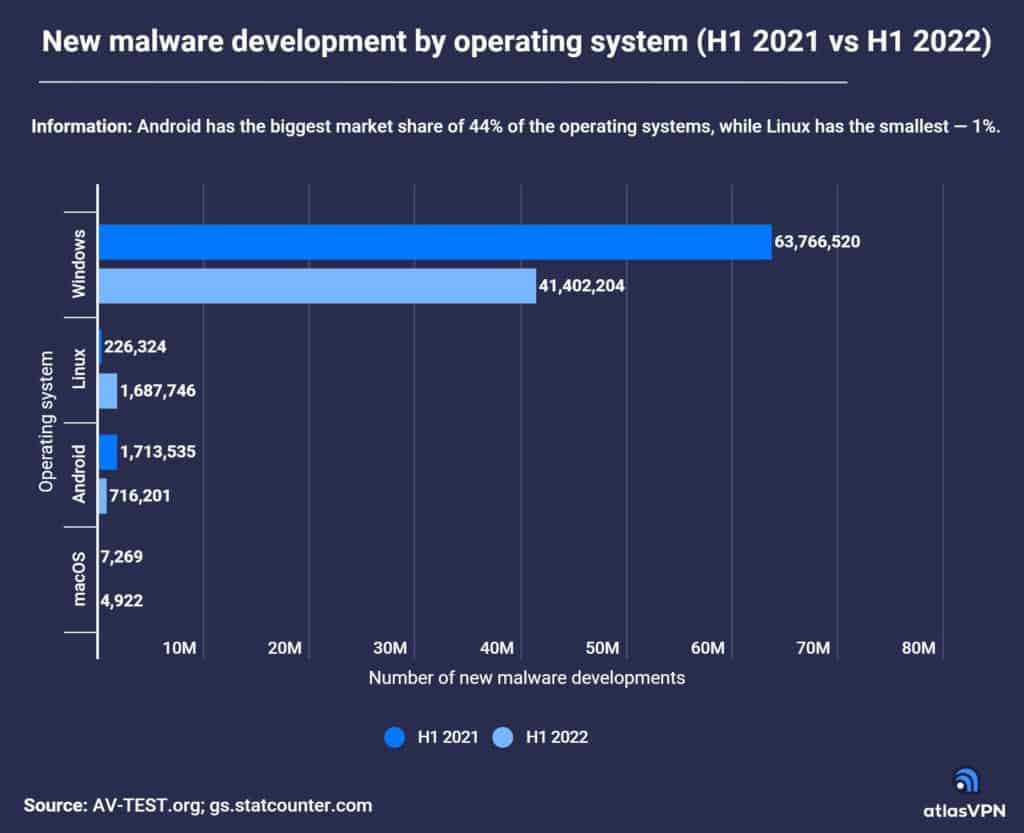
The Linux malware growth has occurred even as Windows, Android and macOS have all seen a decline in new malware samples. Windows still leads overall due to its commanding market share, accounting for 41.4 million malware samples in the first half of 2022.
Citing Statcounter Global Stats, Atlas VPN said Android has a 44% share of the overall operating systems market, while Windows and OS X have 29% and 6%, respectively.
Linux has just 1% of the OS market, but Atlas VPN noted, “while Linux is not as popular among computer users as other operating systems, it runs the back-end systems of many networks, making attacks on Linux highly lucrative. As Linux adoption rises, so will attacks against it.”
Linux powers many cloud-based architectures, and most IoT devices run very minimalist Linux distributions that consist of a Linux kernel and a few core functions, making them attractive for botnets and other similar campaigns.
Considering the value in enterprise targets, hackers are also developing more sophisticated Linux malware (see New Highly-Evasive Linux Malware Infects All Running Processes).
The Atlas VPN team used AV-ATLAS, a threat intelligence platform from AV-TEST Gmb, for its report.
See the Best Open Source Security Tools
How to Protect Against Linux Malware
Some Linux malware, such as Symbiote or more recently OrBit, are particularly evasive and thus pretty hard to detect and remove. Hackers master Linux internals and the current trend is stealth.
More than ever, monitoring all endpoints, including Linux-based systems, is essential. Users and administrators must also update their devices or, at least, apply all security patches, even if it gets harder to keep pace.
Attackers may use Linux malware to harvest credentials or exfiltrate information. Companies should not neglect such post-exploitation tactics, as ransomware groups not only encrypt the victim’s files these days but also use exfiltrated data as a means of extortion.
In that perspective, additional layers of protection like data-in-use encryption might help prevent such events.
Read next: Exfiltration Can Be Stopped With Data-in-Use Encryption, Company Says




