Microsoft this week issued an advisory about three vulnerabilities referred to collectively as ProxyShell days after security researchers at a federal government cybersecurity agency warned that cybercriminals were actively trying to exploit them.
The ProxyShell vulnerabilities that affect Microsoft Exchange servers were put on full display at this month’s Black Hat 2021 conference when Devcore researcher Orange Tsai – who originally uncovered the vulnerabilities – compromised a Microsoft Exchange server by exploiting them during a session at the event.
The three vulnerabilities are CVE-2021-34473, CVE-2021-34523 and CVE-2021-31207. They could lead to escalation of privileges and remote code execution if exploited, enabling hackers to execute arbitrary code on a vulnerable machine, according to a warning issued by the Cybersecurity and Infrastructure Security Agency (CISA).
In its own advisory, Microsoft this week urged organizations running Exchange servers to install patches issued in security updates in May and July, which protect against the vulnerabilities.
“But if you have not installed either of these security updates, then your servers and data are vulnerable,” Microsoft researchers said, adding that “several times” the company has said that “it is critical to keep your Exchange servers updated with latest available Cumulative Update (CU) and Security Update (SU).”
Further reading: Top Patch Management Tools
Microsoft Faces Criticism for Response
Microsoft is catching criticism from some cybersecurity researchers for not being forceful enough over the past several months in warning customers about the threats posed by ProxyShell and urging them to get the vulnerabilities patched.
Security researcher Kevin Beaumont in a blog post said patches issued in April and May close the vulnerabilities, but added that “Microsoft’s messaging of this has been knowingly awful. Microsoft decided to downplay the importance of the patches and treat them as a standard monthly Exchange patch, which have been going on for — obviously — decades. You may remember how much negative publicity March’s Exchange patches caused Microsoft, with headlines such as ‘Microsoft emails hacked.’”
Beaumont also noted that “Microsoft failed to allocate CVEs for these vulnerabilities until July — 4 months after the patches were issued. Given many organizations vulnerability manage via CVE, it created a situation where Microsoft’s customers were misinformed about the severity of one of the most critical enterprise security bugs of the year.”
The March Exchange patches Beaumont noted refer to similar attacks exploiting zero-day flaws folded under the umbrella of ProxyLogon.
In a difficult year for cyber attacks, Microsoft’s ubiquitous presence has placed it at the center of a number of other security incidents and vulnerabilities. At the same time, the software giant has been actively trying to improve security, even posting a string of impressive results in the difficult MITRE endpoint security testing. And this week, Microsoft was at the center of a White House initiative to improve cybersecurity, pledging $20 billion and training resources toward the effort.
Exchange Under Attack
But thanks in part to Microsoft’s half-hearted warnings earlier this year, bad actors are once again taking a look at Microsoft Exchange after the Black Hat show and security researchers are seeing the results. John Hammond, senior security researcher with Huntress Labs, wrote in a blog post that “attackers are actively scanning for vulnerable Microsoft Exchange servers and abusing the latest line of Microsoft Exchange vulnerabilities that were patched earlier this year.”
In a tweet, Huntress CEO Kyle Hansloven noted that his company by Aug. 20 had seen more than 140 webshells across more than 1,900 unpatched servers over a two-day period, with the impacted organizations including building manufacturers, seafood processors and a small residential airport.
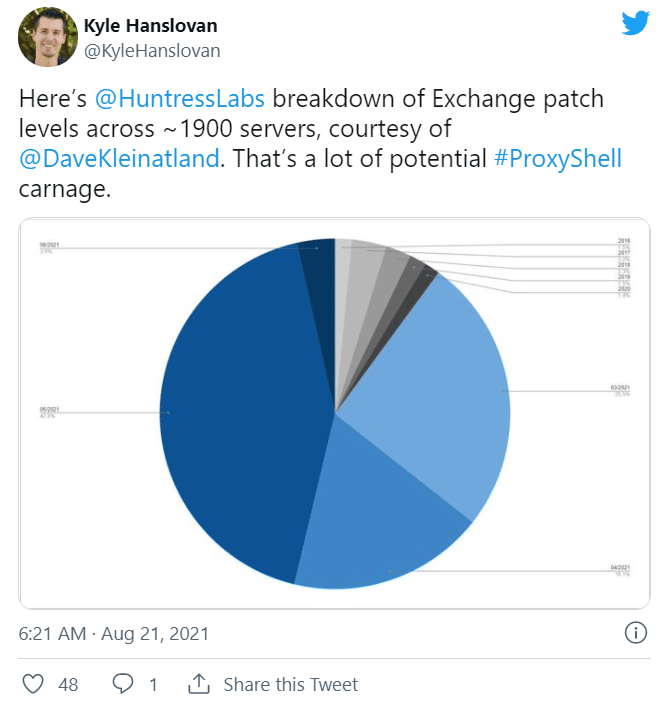
The revelation prompted Rob Joyce, director of cybersecurity at CISA, to tweet, “New surge in Microsoft Exchange server exploitation underway. You must ensure that you are patched and monitoring if you are hosting an instance.”
Beaumont wrote that “for nearly a month, I have been watching mass in the wild exploitation of ProxyShell. … These vulnerabilities are worse than ProxyLogon.”
Ransomware and ProxyShell
The Threat Hunter Team at Symantec in an updated blog post wrote that a new ransomware family called LockFile, which has been around since at least mid-July, appears to be attacking victims’ networks by exploiting the Windows PetitPotam vulnerability, gaining access to the domain controller and then expanding from there across the network.
They initially said it was unclear how the hackers were able to gain access into Microsoft Exchange Servers, but updated post to note what Beaumont had written about the ProxyShell exploits and said that could have been the way the LockFile attackers made their way in.
In his blog post, Huntress’ Hammond wrote that by working with Beaumont and security researcher Rich Warren, they had corroborated that the “webshell and LockFile ransomware incidents we’re seeing within companies may be related.”
Unpatched Exchange Servers
A scan by search engine Shodan published Aug. 11 found that 18 percent of Exchange servers remain unpatched and that almost 40 percent are exposed to one of the vulnerabilities. Beaumont said he wrote a plugin that can identify unpatched systems and then worked with Shodan to put the detection plugin into their product.
In addition, CERT in Austria also is using the scanning script to search for unpatched Exchange servers in that country.
Jake Williams, co-founder and CTO of incident response specialist BreachQuest, told eSecurity Planet that cybercriminals can attack a weakness quickly.
“The speed with which threat actors weaponized the ProxyShell vulnerabilities highlights why having good threat intelligence is critical,” Williams said. “This vulnerability was discussed openly and the consensus among researchers was that weaponization was imminent. Those orgs with that early warning were able to prioritize patching and should not be impacted.”
Assume Compromise
He noted that the CISA warning was timely but added that “by the time there’s a warning about active exploitation in the wild, any internet-facing assets have likely been compromised by threat actors. Organizations that haven’t patched yet should be proceeding under the assumption they’ve been compromised. Installing the patch now will prevent future exploitation, but any backdoors already deployed by threat actors will remain after the patch.”
In its advisory, Microsoft said the Exchange servers that are vulnerable to ProxyShell are those that don’t have at least the CU with the SU from May.
“In all of the above scenarios, you must install one of latest supported CUs and all applicable SUs to be protected,” the company wrote. “Any Exchange servers that are not on a supported CU and the latest available SU are vulnerable to ProxyShell and other attacks that leverage older vulnerabilities.”
Further reading: Top Vulnerability Management Tools




