In December of last year, Microsoft worked with SentinelOne, Mandiant, and Sophos to respond to an issue in which drivers certified by Microsoft’s Windows Hardware Developer Program were being used to validate malware.
Unfortunately, the problem hasn’t gone away.
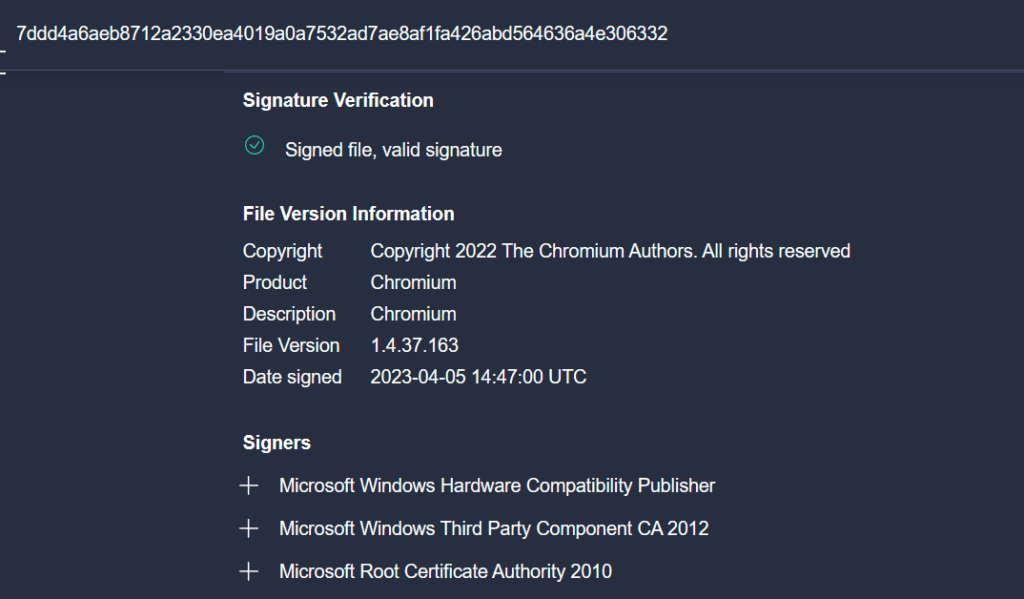
In a recent Mastodon post, security expert Kevin Beaumont observed, “Microsoft are still digitally signing malware kernel drivers, as they can’t identify malware (this comes up over and over again).”
Beaumont provided three examples of remote access trojans that had been verified by Microsoft as legitimate software, adding, “If you have Google’s VirusTotal (Microsoft do) you can run something like this to find them. signature:”Microsoft Windows Hardware Compatibility Publisher” p:5+ tag:signed name:.sys“
In response to an email inquiry from eSecurity Planet, a Microsoft spokesperson acknowledged the ongoing issue, stating, “We have suspended the partners’ seller accounts. In addition, Microsoft Defender Antivirus provides blocking detection for these files.”
The essential challenge remains – and Microsoft has only been able to suspend individual offenders.
Microsoft’s Initial Response
In guidance first published on December 13, 2022, the company stated, “Microsoft was informed that drivers certified by Microsoft’s Windows Hardware Developer Program were being used maliciously in post-exploitation activity. In these attacks, the attacker had already gained administrative privileges on compromised systems prior to use of the drivers.”
Microsoft was notified of the issue by SentinelOne, Mandiant, and Sophos in October 2022, and began an investigation. “This investigation revealed that several developer accounts for the Microsoft Partner Center were engaged in submitting malicious drivers to obtain a Microsoft signature,” the company added. “A new attempt at submitting a malicious driver for signing on September 29th, 2022, led to the suspension of the sellers’ accounts in early October.”
Matching the Microsoft spokesperson’s more recent explanation above, the company stated at the time that Windows Security Updates were released revoking the certificate for the specific files impacted, the partners’ seller accounts were suspended, and Microsoft Defender blocking detections were updated to detect the specific drivers that had been used maliciously.
See the Top 25 Cybersecurity Accounts on Twitter – and 5 on Mastodon
Code Signing Losing Effectiveness
Sophos researchers noted at the time that threat actors, who had previously used certificates signed by less reputable companies in similar attacks, “are moving up the trust pyramid, attempting to use increasingly more well-trusted cryptographic keys to digitally sign their drivers. Signatures from a large, trustworthy software publisher make it more likely the driver will load into Windows without hindrance.”
And SentinelOne researchers pointed out that this wasn’t the first time Microsoft had dealt with this issue, writing, “In June 2021, GData published a blog on a malicious Netfilter rootkit signed through the same process.”
“The receding effectiveness of code signing represents a threat to security and verification mechanisms at all OS layers,” SentinelOne added at the time. “We hope that Microsoft will take steps to consider further enhancements to bolster the security of their signing process to help maintain the implicit trust placed in Microsoft-signed drivers.”
Also read: How Hackers Evade Detection
How Organizations Should Respond
Barry Vengerik, senior principal at Mandiant, now part of Google Cloud, told eSecurity Plant by email that he expects this to be a continuing problem. “It’s unclear how much Microsoft can do barring more extensive detection of malicious files being submitted to the Windows Hardware Compatibility Publisher portal,” he said.
“We recommend organizations rely on behavioral detections to overcome the implicit trust granted to Microsoft-signed binaries and alert on suspicious or rootkit-like activities,” Vengerik added. “We’ve also outlined measures for proactive hunts in the ‘Hunting and Blocking’ section of our blog from December. Lastly, we recommend organizations review the recommended steps outlined in Microsoft’s advisory.”
Read next:




