Security researchers are continuing to see state-supported hacking groups developing tools to leverage the high-profile Log4j vulnerability that exploded onto the scene last month even as the White House and other parts of the federal government look for ways to get ahead of the threat.
Check Point Software’s researchers said this week that the Iran-backed advanced persistent threat group APT35 is looking to leverage the critical Apache Log4j flaw to distribute a new modular PowerShell-based framework designed for persistence, gathering information, communicating with a command-and-control (C&C) server and executing commands.
APT35 – also known as TA453, Phosphorus and Charming Kitten – was among a number of nation-state supported attack groups that were observed by threat intelligence units with Check Point, Microsoft and other vendors investigating ways to exploit the vulnerability just days after it became public Dec. 9.
“With the emergence of the Log4j security vulnerability, we’ve already seen multiple threat actors, mostly financially motivated, immediately add it to their exploitation arsenal,” the Check Point researchers wrote in a blog post this week. “It comes as no surprise that some nation-sponsored actors also saw this new vulnerability as an opportunity to strike before potential targets have identified and patched the affected systems.”
Log4Shell a Significant Threat
The Log4j flaw – which also is known as Log4Shell and is tracked as CVE-2021-44228 – is a significant threat due to the broad enterprise use of Log4j and the huge number of servers and cloud-based services that could be exposed to the zero-day vulnerability. Log4j, a free and widely distributed open-source tool from the Apache Software Foundation, is a logging tool and the flaw impacts version 2.0 through 2.14.1.
Security pros have said that the threat posed by Log4Shell is so high not only because of how far-reaching the tool’s use is but also because of how easily the vulnerability can be exploited. Threat actors only need to send a string that includes the malicious code, which is parsed and logged by Log4j and loaded into a server. Hackers can then gain control of the system running the software, creating a platform for launching their attacks.
A number of patches, detection tools and “vaccines” were released in the weeks after Log4Shell’s disclosure to address the problem. Cybersecurity firm Oxeye this week introduced Ox4Shell, a free open-source payload de-obfuscation tool designed to expose hidden payloads actively used by bad actors to confuse security tools and teams and avoid detection of their Log4Shell attacks. Ox4Shell, which officials said is the first in a series of planned solutions to push back against threats that exploit the Log4j flaw, is available on GitHub.
Also read: How Hackers Use Payloads to Take Over Your Machine
A Long-Term Security Problem
Despite these efforts, industry experts and government officials have said Log4Shell will continue to be a long-term problem. Jen Easterly, director of the federal Cybersecurity and Infrastructure Security Agency (CISA), reportedly said during a press conference that agency officials “expect Log4Shell to be used in intrusions well into the future.”
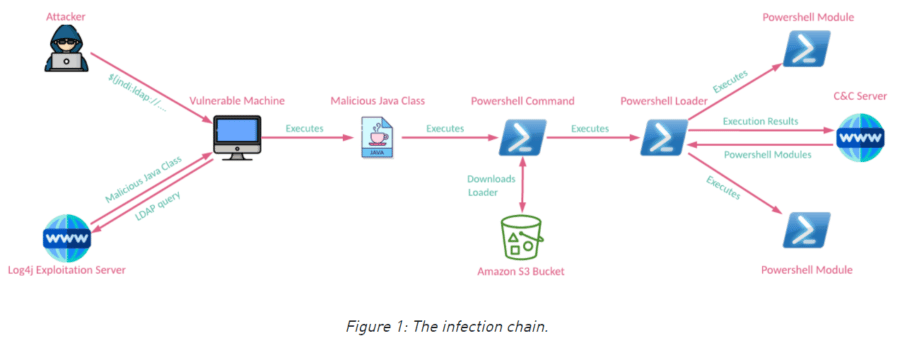
APT35’s PowerShell-based framework – dubbed CharmPower – is based on JNDI Exploit Kits, which has been removed from GitHub due to its skyrocketing popularity following the Log4Shell disclosure, according to Check Point. Attackers using the framework exploit a system by sending a crafted request to a victim’s public-facing device. Once exploited, the exploitation server creates and sends back a malicious Java class – which runs a PowerShell command – for execution on a vulnerable machine and eventually downloads a PowerShell module.
The module communicates with the C&C server and executes the commands, including validating the network connection and receiving, decrypting and executing follow-up modules, Check Point researchers said.
They wrote that “the actor’s attack setup was obviously rushed, as they used the basic open-source tool for the exploitation and based their operations on previous infrastructure, which made the attack easier to detect and attribute.”
Also read: Best Incident Response Tools and Software
Government Cybersecurity Efforts
The Biden Administration and other government entities are working to mitigate the threats from Log4Shell and to try to ensure something similar can’t happen again. The White House on Jan. 13 was meeting with a range of tech companies, including Apple, Facebook’s parent company Meta, Microsoft and IBM, as well as federal agencies like Commerce, Defense, Homeland Security and CISA to talk about security and open-source software in the wake of the Log4j vulnerability.
During her meeting with journalists, Easterly said that CISA has been monitoring threat actors for ones trying to exploit Log4Shell and that “over the past several weeks we have seen widespread exploitation of Log4Shell by criminal actors who use it to install cryptomining software on victim computers or to capture victim computers for use in botnets.”
However, she said, “at this time we have not seen the use of Log4Shell resulting in significant intrusions. This may be the case because sophisticated adversaries have already used this vulnerability to exploit targets and are just waiting to leverage their access until network defenders are on lower alert.”
APT35 Efforts Show Real Threat of Flaw
However, Chris Morgan, senior cyberthreat intelligence analyst at digital risk protection solutions vendor Digital Shadows, said Check Point’s detection of APT35’s exploitation of Log4Shell conflicts with what Easterly and other CISA officials said about no significant intrusion being tied to the Log4j flaw.
“This likely emphasizes ongoing issues with incident disclosure and transparency and the lag that can exist between threat actor activity and discovery,” Morgan told eSecurity Planet, adding that as Easterly said, “Log4Shell will undoubtedly be featured heavily in threat actor campaigns for a considerable amount of time and the full scale of impact from Log4Shell will likely not be known for several months.”
He also noted that APT35 used the publicly available JNDI exploit kit that was published on – and since removed from – GitHub, which will probably ramp up debate regarding GitHub’s policy on proof-of-concept (PoC) exploit kits and malware samples hosted on the service.
“Github changed their policy in June 2021 to permit the removal of such items in order to minimize the risk of the exploits being used in live attacks,” Morgan said. “This decision originally was related to the removal of a PoC raised by a security researcher for the ProxyLogon Microsoft Exchange vulnerabilities, which was widely criticized by many in the security community.”
APT35 is a “live example of how a public exploit can fall into the wrong hands quickly,” he said. Check Point’s “findings may prove to be a justification of why their change in policy was a correct decision.”
The researchers wrote that whenever there is a new critical vulnerability published, the InfoSec community “holds its breath until its worst fears come true: scenarios of real-world exploitation, especially by state-sponsored actors. As we showed in this article, the wait in the case of the Log4j vulnerability was only a few days. The combination of its simplicity, and the widespread number of vulnerable devices, made this a very attractive vulnerability for actors such as APT35.”
They also noted that the threat actors used the same or similar infrastructure as in many of their previous attacks, but that given their ability to take advantage of the Log4j vulnerability and “the code pieces of the CharmPower backdoor, the actors are able to change gears rapidly and actively develop different implementations for each stage of their attacks.”
Read next: Top Vulnerability Management Tools




