A critical vulnerability discovered in the open-source load balancer and proxy server HAProxy could enable bad actors to launch an HTTP Request Smuggling attack, which would let them bypass security controls and gain unauthorized access to sensitive data.
Researchers with JFrog Security uncovered the vulnerability, CVE-2021-40346, during their regular searches for new and previously unknown vulnerabilities in popular open-source projects. HAProxy fits into that category.
HAProxy is a widely used tool designed for high-traffic websites and used by many companies. It also ships with most mainstream Linux distributions and is often deployed by default in cloud platforms.
In a blog post, JFrog researchers Ori Hollander and Or Peles said they worked with HAProxy’s maintainers to create a verified fix.
HTTP Request Smuggling
Through the vulnerability, an attacker could “smuggle” HTTP requests to a back-end server without the proxy server being aware of it, the researchers said. Not only could this enable the cybercriminals to bypass security controls – such as any ACLs defined in HAProxy, which enables users to perform such functions as defining custom rules for blocking malicious requests, choosing backends and redirecting to HTTPS – but also access sensitive data, execute unauthorized commands, modify data, hijack user sessions and exploit a reflected XSS (cross-site scripting) vulnerability without user interaction.
The vulnerability has a severity rating of 8.6 on the CVSS scoring system.
“HTTP request smuggling is a vulnerability type that has gained widespread community attention due to numerous high-paying bug bounty reports over the last few months,” JFrog CTO Asaf Karas told eSecurity Planet. “Not only is it gaining traction, but its impact can be detrimental depending on the configuration of the servers behind the proxy. Security leaders would be wise to review how they utilize HAProxy in their environment to evaluate if they are vulnerable, especially if they use HAProxy as a reverse proxy.”
The researchers wrote that the vulnerability was fixed in versions 2.0.25, 2.2.17, 2.3.14 and 2.4.4 of HAProxy. The fixes in these versions add size checks for the name and value lengths, the researchers wrote.
In addition, organizations that can’t upgrade to any of the new versions can add the following lines to HAProxy’s configuration:
http-request deny if { req.hdr_cnt(content-length) gt 1 }
http-response deny if { res.hdr_cnt(content-length) gt 1 }
Those unsure of the version they’re running can use software composition analysis (SCA) tools like JFrog’s Xray to determine the version in use and whether artifacts are affected by the vulnerability.
Increasingly Common Web Architecture
According to web application testing and scanning vendor PortsWigger, in an increasingly common architecture, modern web apps often use chains of HTTP servers between users and the application logic. Users send requests to a front-end server – a load balancer or reverse proxy – which then forwards requests to one or more back-end servers.
“When the front-end server forwards HTTP requests to a back-end server, it typically sends several requests over the same back-end network connection, because this is much more efficient and performant,” PortWigger officials wrote in an explainer on its site. “The protocol is very simple: HTTP requests are sent one after another, and the receiving server parses the HTTP request headers to determine where one request ends and the next one begins.”
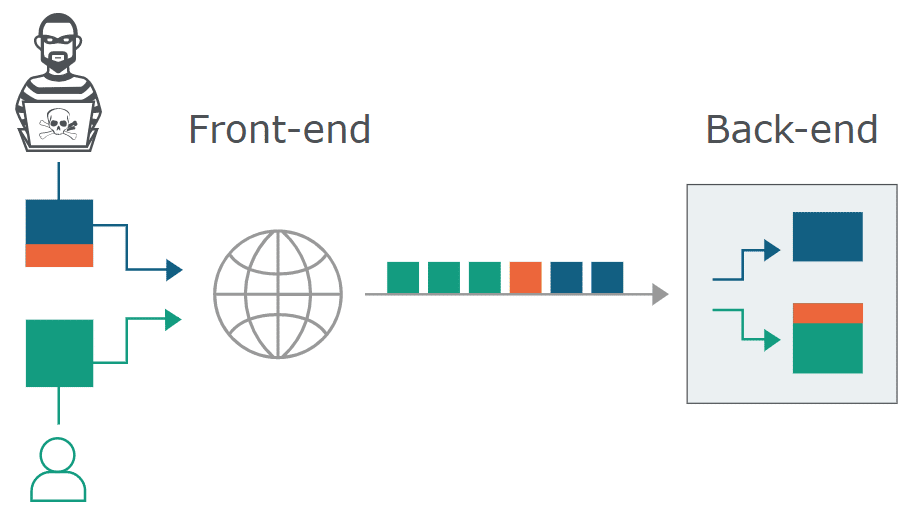
The HAProxy load balancer’s key job is proxying HTTP requests coming in from a user to a back-end server, the JFrog researchers wrote. The HTTP request handling logic can be viewed in two phases: the initial parsing and further processing, which is simplified and focused on the Content-Length header.
New Use for Old Attack Technique
HTTP Request Smuggling is an attack technique that came to light in 2005 and is designed to interfere with the processing of HTTP requests between the front-end server – in this case, HAProxy – and the back-end server, according to JFrog. Cybercriminals typically use the technique to send a specially crafted request that includes an additional request in the body of the request. The inner request is smuggled through the front-end server – which the researchers said considers the inner request as simply the body of the entire request – and taken as a normal request by the back-end server.
“In most cases, the smuggling technique is done by supplying both the Content-Length and Transfer-Encoding headers with contradicting lengths in the same request and aiming for parsing inconsistencies between the frontend and backend servers,” Hollander and Peles wrote. “In our case, however, the attack was made possible by utilizing an integer overflow vulnerability that allowed reaching an unexpected state in HAProxy while parsing an HTTP request – specifically – in the logic that deals with Content-Length headers.”
What makes this kind of attack possible is that “when the frontend server forwards HTTP requests to the backend, it uses the same established TCP connection instead of wasting time on opening and closing sockets,” they wrote. “The requests are sent back-to-back and it is up to the backend server to decide where a request ends and the next one begins.”
Shachar Menashe, senior research director at JFrog, said it’s important for organizations to “make sure administrative web endpoints and sensitive materials are guarded behind robust authentication mechanisms, instead of simple ACL rules in an external proxy or firewall. Additionally, logged HTTP traffic should always be available to administrative users only – regardless which part of the HTTP request is logged— in order to avoid exposing unintended parts of an HTTP request to potential attackers.”
Further reading: Open Source Security: A Big Problem







