A firewall policy is a set of rules and standards designed to control network traffic between an organization’s internal network and the internet. It aims to prevent unauthorized access, manage data movement, and guard against potential security threats. There are key components to consider, main types of firewall policies and firewall configurations to be aware of, and sample policies to review that offer valuable context in creating your own effective firewall policy.
Featured PartnersFeatured Partners: Cybersecurity Training Software
eSecurity Planet may receive a commission from merchants for referrals from this website
Free Firewall Policy Template
We’ve created a free generic firewall policy template for enterprises to download and use. This file contains the common sections of a firewall policy, so it’s possible that some sections are unnecessary for your organization while others may require further detail. The bracketed notes and footer provide further instructions and must be removed from your final copy. Download the template and tailor it to align with the particular requirements and conditions of your enterprise.

What Are the Components of Firewall Policies?
Key firewall policy components include user authentication mechanisms, access rules, logging and monitoring methods, rule base, and numerous rule objects that specify network communication conditions. When creating the firewall policy draft, these elements make up a detailed set of rules and guidelines controlling the use, management, and security configurations of a firewall inside an organization.
User Authentication
Only authorized users or systems can access the network through user authentication. This method often entails confirming user credentials before giving access. It increases security by preventing unwanted access and protecting critical resources.
Access Rules
Access rules, also known as access control lists (ACLs), manage which traffic is permitted or prohibited. They define the conditions under which network communication is authorized and serve as key building blocks of network security regulations.
Logging & Monitoring
Logging and monitoring methods record and analyze network activity. They provide a foundation for recognizing possible security issues and aiding forensic analysis. To protect the network’s security and integrity, administrators can track and analyze actions by keeping a log of network events.
Rule Base
The rule base defines the criteria for accepting or rejecting network traffic. This set of rules includes details such as source and destination IP addresses, port numbers, and protocols. It serves as the foundation of firewall regulations, specifying the basic criteria of filtering traffic and controlling the flow of data.
Rule Objects
Rule objects define access rules and incorporate components such as applications, source or destination hosts, and networks. Examples include Users, User Groups, Applications, Application Groups, Countries, IPv4/IPv6 Endpoints, Host DNS Names, and more. Rule objects improve policy administration by providing a structured mechanism to group items used in access rules.
User & Application-Based Rule Objects
User and User Group rule objects are based on Windows Active Directory users and user groups. Application rule objects employ the signature set to identify diverse software packages. The application on Custom Port detects non-standard ports. Application Groups combine various apps for unified handling. These rule objects provide detailed control over user and application-specific traffic, boosting security and resource management.
Network-Based Rule Objects
IPv4/IPv6 Endpoints, Host DNS Names, IPv4/IPv6 Address Ranges, and Networks define source/destination criteria. Country rule objects allow/block traffic based on the countries of origin and destination. For easier management, Network Group rule objects integrate several network-related rule objects. These rule objects set communication criteria, enabling or blocking traffic based on network properties.
Time-Based Rule Objects
Finite Time Period implements time interval-specific constraints. Repeated rule enforcement can be executed with Recurring Time Period and Recurring Time Period Group. Time-based rules control network access by aligning with certain timeframes and intervals.
Service & Service Group Rule Objects
Service rule objects limit traffic depending on IP protocols, ICMP codes, or TCP/UDP port numbers. Service Group rule objects combine services for consistent policy management. These rule objects establish communication parameters, ensuring control over certain services and protocols.
3 Main Types of Firewall Policies
There are three fundamental types to creating firewall policies: hierarchical, global network, and regional network, each with its own set of advantages based on organizational needs. Understanding these types enables enterprises to create firewall policies that not only achieve security objectives but also integrate smoothly with their particular business landscapes.
Hierarchical Firewall Policy
The hierarchical firewall policy takes an organized approach to rule organization by grouping rules in a hierarchical style and assigning unique rules to each security zone. This gives businesses granular control over network traffic, allowing them to fine-tune security measures based on varied requirements inside distinct zones. While this strategy provides thorough control, it needs rigorous maintenance for effective and comprehensive security posture.
Global Network Firewall Policy
A global network firewall policy, in contrast to the hierarchical model, opts for standard rules that are implemented consistently across all security zones in an organization. This offers a streamlined and uniform security environment. However, because the standards are global in design, they may lack the specificity required for businesses with varying security demands across many zones, potentially resulting in a one-size-fits-all approach.
Regional Network Firewall Policy
The regional network firewall policy, designed for enterprises with regionally distributed operations, achieves a balance between meeting the security needs of many sites while keeping a centralized approach to policy administration. This enables businesses to successfully address difficulties and ensures that security measures are optimized for the specific threats and landscapes encountered in various geographic areas.
9 Steps to Create a Firewall Policy
Deploying firewalls is a standard precaution that becomes more effective when combined with a well-defined firewall policy. Strategic steps of a strong firewall policy include stating the purpose, scope, definitions, exceptions and change guidelines, detailed policies and processes, compliance guidelines, documentation, violations and sanctions, and distribution process. We’ll provide screenshots from our template to help you visualize each section below.
1. State the Purpose
List the firewall’s intended goal, such as securing sensitive data, restricting network access, or protecting against specific threats. This clarity ensures that the firewall matches with broader security goals and serves its intended purpose. If the primary purpose is to protect sensitive customer information, for example, the policy should highlight methods to secure data exchanges and prevent unwanted access.

2. Identify the Scope
Specify the networks, systems, and data that are covered by the policy to prevent ambiguity and ensure that it covers the intended assets. Organizations can adapt their firewall rules to protect specific assets by explicitly defining the scope, making the policy more targeted and effective. If the scope encompasses both internal and cloud-based systems, the policy may need to account for distinct security issues for each environment.

3. Define Key Terms
Establish explicit definitions for terms to create a shared understanding among all stakeholders involved in policy implementation. Determining the key terms ensures that everyone interprets and manages the material consistently, lowering the chance of miscommunication and errors. Consider creating the whole policy first to identify all the key terms that may be unfamiliar to the general reader.

4. Establish Exceptions & Change Processes
Create a transparent procedure for requesting and approving changes and exceptions, including the relevant paperwork, to balance flexibility with strong security rules. This guarantees that exceptions are given based on valid business reasons and are documented and reviewed on a consistent basis. If a department needs specific ports open for a project, the exception process will define the stages for approval as well as the documentation needed.

5. Detail Policies & Procedures
Outline specific duties, rules for inbound and outbound traffic, policy infractions, and rule update procedures to ensure full policy execution. This phase provides detailed guidance to assist organizations in constantly enforcing security measures. As an example, detailing methods for modifying firewall rules, ensures that changes are carried out in a uniform manner, reducing the chance of misconfigurations.

Configure Firewall Settings
Implement firewall configurations based on stated policies — this is a hands-on stage in which enterprises create traffic-control rules. The configurations, which adhere to the principle of least privilege, limit access to just essential services and ports. Configuring the firewall to allow only necessary incoming and outgoing traffic helps prevent illegal access attempts and potential security breaches.
Implement Regular Testing
Perform routine vulnerability scanning, penetration testing, and rule reviews to maintain the firewall’s continued effectiveness. Regular testing can detect and mitigate any flaws, hence improving overall security posture. Vulnerability scanning can detect software flaws, whereas penetration testing replicates real-world attack scenarios to assess the firewall’s resilience.
6. Address Compliance Requirements
Ensure that the firewall policy complies with relevant cybersecurity and privacy requirements. This displays the organization’s dedication to legal and regulatory norms, lowering the danger of legal ramifications. For example, if the firm handles healthcare data, the firewall policy must comply with the Health Insurance Portability and Accountability Act (HIPAA) to protect patient information and ensure compliance.

7. Maintain Thorough Documentation
Keep detailed records of firewall setups, changes, exceptions, and testing results. This documentation is useful for audits, troubleshooting, and future policy updates. Create a documentation guideline to allow enterprises to monitor and easily review the updates done for firewall setups. This supports easier troubleshooting and provides insights for continual improvement.

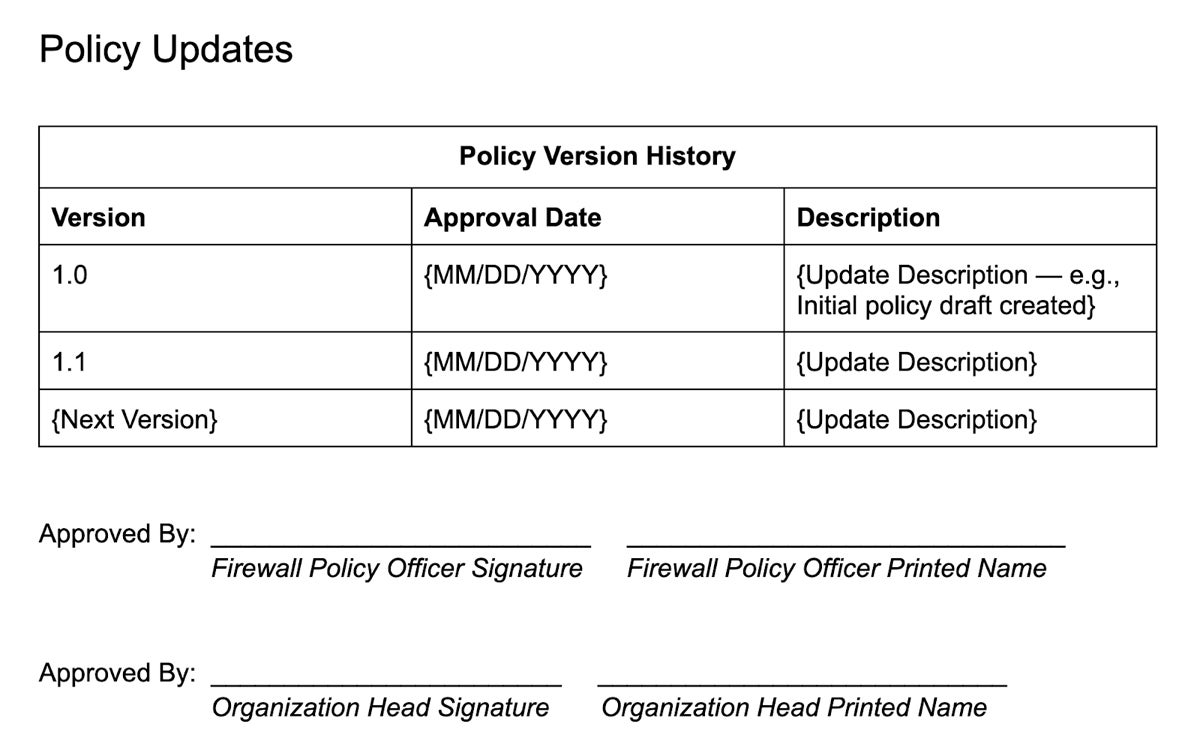
Also set the frequency of review and revision in terms of time intervals (monthly, quarterly, or annual). Specify the circumstances in which the policy must be reviewed and revised, such as adapting to an advancement in firewall technology. Also specify the strategies for continuous development based on feedback and insights.

Finally, fill out the policy version history to note any and all updates to the policy, as well as the approvers of the newest version.
8. Define Violations & Penalties
Clearly define the consequences of policy infractions, such as purposeful firewall bypassing or other prohibited conduct, to encourage a culture of accountability. For example, state that attempting to disable the firewall without authorization leads to warnings, disciplinary proceedings, or termination of employment. Encourage staff to adhere to security regulations and prevent illegal activity.

9. Plan the Policy Distribution
The Distribution section guarantees that the policy reaches all relevant individuals in charge of firewall-related responsibilities within the organization. This dissemination ensures that everyone involved is aware of the policy, confirms receipt of it, and agrees to comply with its terms.

Each employee should acknowledge receipt and compliance with the policy via their signature at the bottom of the document.

Firewall Configuration Types
Firewall configuration types are distinct setups that balance network security control with efficient implementation and maintenance. NIST highlights three configurations: explicit rules, where regulations are manually defined; settings-based configuration, which uses predefined configurations; and automatic policy creation, which uses automations for policy generation and adaptation. Knowing these types helps specify the procedures in the firewall policy draft.
Explicit Rules
Administrators take a hands-on approach in this configuration type, establishing rules that explicitly allow or deny specific network activity. These rules cover important elements including protocols, source/destination addresses, and ports. While this type of system provides a great level of control, it requires demanding manual setup and regular maintenance.
Settings-Based Configuration
In settings-based configuration, administrators configure generic settings that generate internal rules automatically. Overall security levels, intrusion detection and prevention thresholds, and other global factors may be included in these settings. This technique reduces configuration but may cost control granularity.
Automatic Policy Creation
Some firewalls can generate policies and rules automatically based on observed network behavior or predetermined templates. Machine learning algorithms or behavioral analysis may play a role in dynamically developing these rules. Based on observed traffic patterns, the firewall adapts its ruleset autonomously. This approach is often more adaptable to changing network conditions, but it necessitates extensive testing to ensure accuracy and effectiveness.
Real Firewall Policy Examples We Like
A well-structured template clarifies key components, ensuring that policies are comprehensive and in accordance with industry best practices. Individual firewall policy templates may vary depending on organizational needs. To serve as a starting point for creating your own, we’ve identified four quality examples of firewall policies from Northwestern University, DWP, SANS, and NIST.
Northwestern University
Northwestern University’s firewall policy highlights effective firewall use and administration within the university’s network. The policy, classified into Network and Host, establishes responsibilities, scope, and deployment scenarios. It has a clear purpose and audience-focused application. It shows PCI-DSS compliance, explains ruleset update methods, and specifies incident reporting instructions, all of which contribute to their overall network security process.
Department for Work and Pensions (DWP)
UK’s DWP firewall policy has structured sections on change and approval history, compliance, and an exceptions procedure. It addresses security procedures such as change management, rule testing, security audits, user access, and maintenance. Given that it’s designed for a broader audience, its appendix section improves readability and clarity.

SANS Institute
Because of its methodical and modular approach, the SANS firewall policy template stands out as a model guide. It ensures comprehensive coverage by focusing on issue-specific aspects and smoothly integrating with the larger security policy. The emphasis on reaching consensus encourages a collaborative security culture, alleviating concerns about policy execution. The clarity and practicality of the template make it a solid framework resource for enterprises.

National Institute of Standards and Technology (NIST)
NIST’s firewall policy guidelines provides a thorough introduction, in-depth explanation of firewall technologies, network architectures, and a comprehensive firewall policy procedures section. It contains detailed instructions for planning, configuring, testing, deploying, and managing firewalls. Overall, its structured and detailed approach make it a valuable resource for enterprises looking for a well-organized framework to improve their cybersecurity measures.

Bottom Line: Every Enterprise Needs a Firewall Policy
Implementing a well-crafted firewall policy tailored to your specific needs is a nonnegotiable for any organization. The fundamental capability of a firewall policy to protect your network security against potential threats lays the foundation towards a holistic cybersecurity development. Mutually reinforcing it with the knowledge of firewall and its best practices sets your organization’s digital infrastructure to the highest security standards.




