Industrial control systems (ICS) are the backbone of critical infrastructure, powering essential operations in the energy, manufacturing, water treatment, and transportation sectors. These systems ensure the seamless functioning of processes that keep industries running smoothly and efficiently. However, as ICSs become more integrated with digital networks, their vulnerability to cyberthreats grows, making robust security measures essential to safeguarding these vital operations.
Are your industrial control systems secure enough? As hackers grow more sophisticated, understanding the risks and how to mitigate them is more important than ever. Let’s dive into what ICS cybersecurity entails, why it’s vital, and the best practices to secure your systems against increasingly prevalent cyberthreats.
Featured PartnersFeatured Partners: Cyber Security
eSecurity Planet may receive a commission from merchants for referrals from this website
What is an Industrial Control System (ICS)?
An industrial control system (ICS) refers to a broad set of control systems and associated instrumentation used for industrial process control. These systems are integral to the smooth operation of industries such as manufacturing, power generation, oil and gas, water management, and more. An ICS consists of hardware and software systems that monitor and control industrial equipment and processes.
ICS ranges from fully automated systems to manual operations with varying degrees of control and complexity. These systems can be simple, like managing a single machine, or complex, like overseeing the operation of an entire manufacturing plant. ICS integrates multiple technologies to ensure continuous and efficient industrial operations.
What are the Key Components of ICS?
Industrial control systems (ICS) are essential for automating and controlling industrial processes. These systems ensure that industrial operations are efficient, safe, and reliable. Key components of ICS include:
Supervisory Control and Data Acquisition (SCADA) Systems
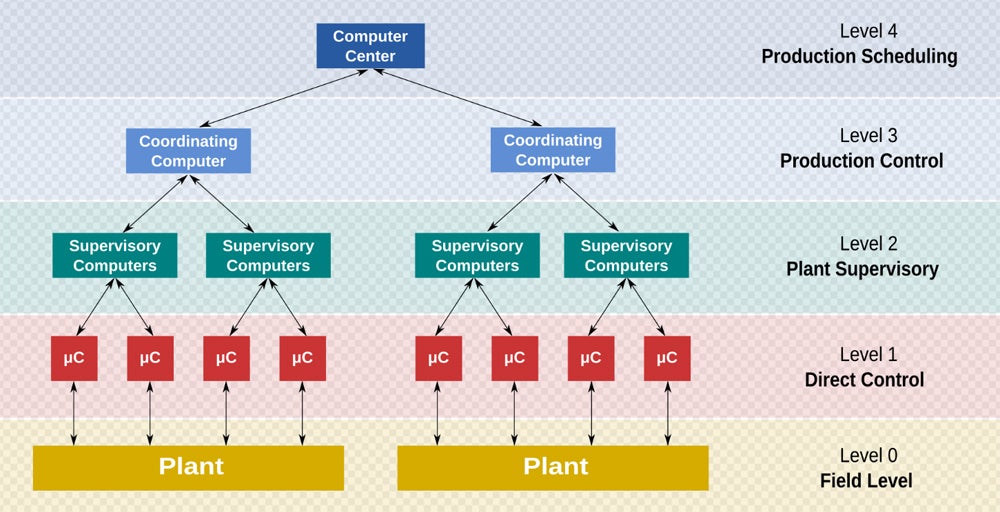
SCADA systems collect data from sensors and control systems in real-time. They provide an interface for operators to monitor and control processes remotely. SCADA systems also allow for data logging and trend analysis to enhance decision-making.
Programmable Logic Controllers (PLCs)
PLCs are specialized industrial computers used to automate machinery and processes. They interpret sensor input signals and make decisions based on programmed logic, controlling actuators and other devices to achieve desired outcomes.
Distributed Control Systems (DCS)
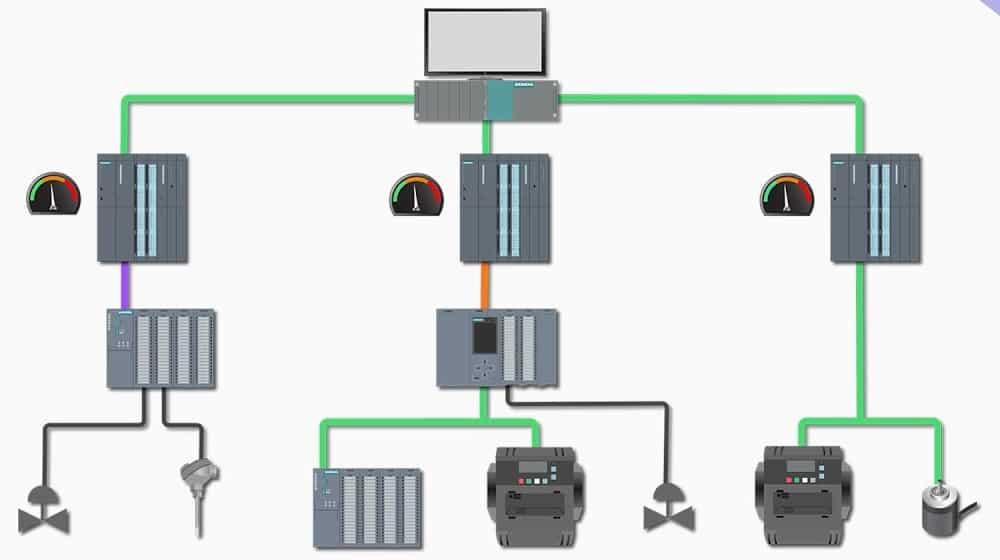
A DCS is used for large, complex industrial operations like power plants and refineries. It distributes control functions across multiple controllers, reducing the risk of a single point of failure. DCS integrates both hardware and software for process control and monitoring.
Human-Machine Interface (HMI)
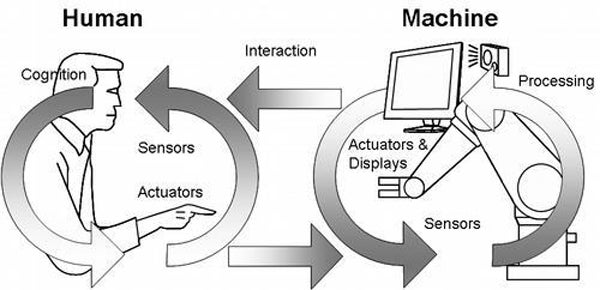
The HMI is the interface through which operators interact with the control system. It provides graphical representations of processes and equipment, allowing operators to control machinery, view system status, and monitor alarms in real time.
Sensors and Actuators
- Sensors: These devices collect data from the physical environment, such as temperature, pressure, and flow rate. Sensors feed this data to the PLCs or DCS, allowing the system to make control decisions.
- Actuators: Actuators convert control signals into physical actions, such as opening a valve or adjusting a motor speed. They are responsible for executing the commands issued by the control system.
Remote Terminal Units (RTUs)
RTUs are field devices that interface with sensors and actuators in remote locations. They communicate with the central control system, allowing data collection and remote control over long distances.
Industrial Networks
Communication networks are crucial for connecting all components of an ICS. These networks enable data exchange between PLCs, RTUs, SCADA systems, and HMIs. Industrial networks include wired and wireless technologies such as Ethernet, Modbus, and Profibus.
Security Solutions
ICS systems are vulnerable to cyberattacks, so security solutions, including firewalls, intrusion detection systems, and encryption protocols, are vital to protect these critical infrastructures from unauthorized access and malicious activities.
Control Room and Operator Workstations
These are physical spaces where operators monitor and control industrial processes. The workstations provide access to the HMI, SCADA, and other system components, offering a central point for managing the entire industrial operation.
These key components work together to provide reliable, automated control of industrial processes, ensuring safety, efficiency, and productivity.
Industrial Control System (ICS) Standards
Ensuring the security and reliability of industrial control systems involves adherence to industry standards designed to maintain safety and functionality. Several key ICS standards focus on protecting these critical systems from cyberthreats:
- IEC 62443: Developed by the International Electrotechnical Commission (IEC), this standard outlines security measures for automation and control systems.
- NIST SP 800-82: The National Institute of Standards and Technology (NIST) guidelines focused on securing ICS environments.
- ISO/IEC 27001: An international standard on managing information security, including within industrial contexts.
These standards provide frameworks for ensuring security throughout the lifecycle of an ICS, from design to operation, maintenance, and decommissioning.
What is the Importance of Cybersecurity in an Industrial Control System (ICS)?
The potential for cyberattacks increases with industrial control systems becoming more interconnected through the Internet of Things (IoT) and cloud-based systems. Cybersecurity for industrial control systems is vital to prevent unauthorized access, data manipulation, and system disruption.
One recent example that underscores this importance is the 2021 Colonial Pipeline ransomware attack. This ICS attack disrupted fuel flow across the eastern United States, leading to shortages and financial losses. The breach occurred due to a cyber vulnerability within the ICS network, which hackers exploited to hold the system hostage for ransom.
The consequences of cyberattacks on ICS are far-reaching, from environmental disasters to halting production lines. Given the potential impact, ICS cyber security is paramount for industrial sectors.
How Does ICS Security Work?
ICS cybersecurity involves safeguarding the communication and data flow between ICS components, preventing unauthorized access, and ensuring the integrity and availability of critical infrastructure. It comprises several layers of security measures, including:
- Network segmentation: Isolating critical control systems from business and external networks.
- Intrusion detection and prevention systems (IDPS): Monitoring network traffic for suspicious activity.
- Role-based access control (RBAC): Restricting system access based on user roles and responsibilities.
- Encryption and secure communication protocols: Protecting data in transit between ICS components.
- Patch management: Keeping software and firmware up to date to close security gaps.
Combined with ongoing monitoring and incident response planning, these mechanisms form the backbone of industrial control cybersecurity strategies.
Top 10 ICS Threats to Watch Out For
Industrial control systems (ICS) face a constantly evolving landscape of cyberthreats, many of which can have severe consequences for operational safety, reliability, and security. These threats exploit vulnerabilities in both technology and human factors, making it critical for organizations to stay vigilant and proactive. The following are some of the most significant threats ICS environments face today:
Malware & Ransomware
Malware and ransomware attacks specifically target ICS to disrupt industrial operations, encrypt critical data, or cause widespread damage to the system. Ransomware can cripple essential functions until a ransom is paid, while malware may lead to unauthorized control or surveillance of the system.
Impact: Disruption of critical processes, financial losses, and potential safety hazards in industries like energy, manufacturing, and transportation.
Phishing Attacks
Phishing campaigns exploit human error by tricking employees or contractors into clicking on malicious links or attachments. These attacks can grant attackers access to ICS networks through compromised credentials or infected devices.
Impact: Unauthorized network access, data theft, or the spread of malware within the ICS infrastructure.
Advanced Persistent Threats (APTs)
APTs are sophisticated, long-term attacks designed to infiltrate ICS networks and remain undetected for extended periods. These attackers often seek to gather sensitive information, manipulate system operations, or sabotage infrastructure by gaining deep access to critical systems.
Impact: Extensive data theft, espionage, or significant operational disruption when attackers eventually activate their malicious objectives.
Insider Threats
Employees, contractors, or vendors with legitimate access to ICS systems can pose a serious security risk if they intentionally or unintentionally misuse their access. Insider threats are especially dangerous because they already bypass many traditional security barriers.
Impact: Sabotage, theft of proprietary information, or unintentional errors leading to system vulnerabilities.
Denial-of-Service (DoS) Attacks
DoS attacks aim to overwhelm ICS networks or devices with excessive traffic, rendering the system inoperable. These attacks can halt industrial processes, disrupt communications, or take systems offline completely.
Impact: Downtime in critical infrastructure, loss of control over industrial processes, and potential damage to equipment.
Supply Chain Attacks
Supply chain attacks target third-party vendors and service providers interacting with ICS environments. By compromising these external entities, attackers can access ICS networks indirectly, bypassing traditional security controls.
Impact: Widespread exposure to vulnerabilities, potentially affecting multiple organizations relying on the same suppliers or vendors.
Remote Access Vulnerabilities
ICS systems often require remote access for monitoring and maintenance, but attackers can exploit weak authentication methods or insecure remote access points. These vulnerabilities may allow unauthorized individuals to control critical industrial processes from remote locations.
Impact: Unauthorized system manipulation leads to operational disruptions or safety hazards.
Firmware Manipulation
Attackers can manipulate firmware in ICS components, such as controllers and sensors, by inserting malicious code to compromise operations. Firmware manipulation is particularly dangerous because it often remains undetected until significant damage occurs.
Impact: Sabotage of system functionality, unauthorized control over devices, and potentially catastrophic failures in industrial operations.
Weak Encryption
Inadequate encryption or the complete absence of it in communication between ICS components can allow attackers to intercept sensitive information, such as control commands or operational data. This can lead to unauthorized actions within the system.
Impact: Intercepted data, manipulation of system commands, or unauthorized system control.
Zero-Day Vulnerabilities
Zero-day vulnerabilities refer to unknown or newly discovered flaws in ICS software or hardware that have not yet been patched. Attackers exploit these weaknesses before developers can release security updates, making them particularly dangerous.
Impact: Unpatched systems are left vulnerable to exploitation, which can lead to significant breaches or operational damage.
Industrial control systems’ growing complexity and interconnectivity have made them attractive targets for cybercriminals and nation-state actors. Addressing these threats requires a multi-layered security approach, including employee training, robust access controls, network segmentation, frequent patching, and ongoing monitoring to detect and respond to potential attacks. Staying vigilant and adopting industry standards can help mitigate these evolving cyberthreats and ensure ICS environments’ continued safety and functionality.
How to Secure an ICS from Cyberattacks?
Securing an ICS from cyberattacks requires a comprehensive strategy that addresses various vulnerabilities and strengthens defenses. Here are key strategies for improving ICS cybersecurity:
- Conduct a Risk Assessment: Regularly evaluate potential risks to your ICS to identify vulnerabilities and threats. Understanding your risk landscape helps prioritize security measures.
- Implement Network Segmentation: Ensure ICS networks are isolated from business IT networks. This separation reduces the risk of lateral movement by attackers and protects critical control systems from broader network threats. For insights into network security threats and strategies to mitigate them, you can refer to this network security threats guide.
- Use Multi-Factor Authentication (MFA): Enhance login security across ICS platforms by requiring multiple verification forms. MFA adds an extra layer of protection against unauthorized access.
- Establish Access Controls: Limit access to ICS systems to only those personnel whose roles require it. Implement role-based access controls to ensure users can only access the data and systems necessary for their duties.
- Keep Systems Up to Date: Apply security patches and updates as soon as they become available. Keeping systems current helps to close vulnerabilities that attackers could exploit.
- Develop an Incident Response Plan: Prepare for quick response and recovery in case of a cyberattack. An effective incident response plan ensures that your team can efficiently manage and mitigate the impact of security breaches.
ICS Security Best Practices
To safeguard your industrial control systems (ICS) from cyberthreats, follow these key best practices:
- Regular audits and vulnerability assessments: Conduct routine reviews to identify system weaknesses and potential attack vectors.
- Continuous network monitoring: Implement real-time monitoring tools to detect and alert any suspicious activity within the network.
- Cybersecurity awareness training: Educate employees about cybersecurity risks and teach them how to spot potential threats.
- Enforce strong password policies: Use complex, unique passwords and update them regularly to strengthen system security.
- Deploy endpoint protection: Install antivirus, anti-malware, and firewall solutions on all ICS devices to block malicious access.
- Backup critical data: Frequently back up essential system data to ensure quick recovery during an attack.
By adhering to these practices, you can effectively enhance the security of your ICS environment and reduce potential risks.
Emerging Trends in ICS Security
As industrial control systems (ICS) continue to evolve, so do the methods for protecting them. With the rise of more sophisticated cyberthreats, new trends are emerging to strengthen ICS security. Key developments include:
AI & Machine Learning
Automated threat detection and response are becoming increasingly prevalent, allowing ICS networks to identify and neutralize potential security risks without human intervention quickly.
Behavioral Analytics
By analyzing typical user behavior, this technology detects deviations that may signal insider threats or malicious activity, providing an early warning system for potential breaches.
Zero-Trust Architecture
This approach ensures strict access controls, where no user or device is trusted by default—even within the network. Every access request is verified, reducing the risk of internal vulnerabilities.
Cloud-Based ICS Security
As more industrial systems leverage cloud infrastructure for remote monitoring and control, securing these cloud environments becomes critical, requiring advanced encryption and access controls.
Blockchain Technology
Blockchain is gaining traction for securing data exchanges between ICS devices by offering tamper-proof, decentralized records that prevent unauthorized alterations or hacks.
Quantum Cryptography
Future-proofing ICS security, quantum encryption techniques offer unprecedented levels of data protection, ensuring that even the most advanced hacking methods cannot breach secure communications.
These emerging cybersecurity trends underscore the ongoing evolution of ICS security, helping industries adapt to technological advancements while safeguarding their critical infrastructure from modern cyber threats.
Bottom Line: Securing Industrial Control Systems
Securing industrial control systems is a critical task that demands continuous vigilance, the latest technologies, and strict adherence to industry standards. As cyberthreats evolve and become more sophisticated, businesses must prioritize ICS cyber security to safeguard their critical infrastructure. Understanding the components of ICS, implementing best practices, and staying abreast of emerging trends are essential steps in this process.
Staying informed and proactive in your security approach will help defend against cyberattacks and ensure the resilience of your industrial control systems. Explore this network security guide for comprehensive strategies and insights into maintaining robust network security, including protecting your ICS.




