In the realm of cybersecurity, incident response has taken on new importance, especially with the rise in attacks and the sophisticated methods being used by cybercriminals.
The conundrum is that incident response (IR) happens only after an incident is detected, which brings up some major concerns. Most of the IR platforms on the market are reactive, doing little to prevent breaches in the first place. They rely on human operators to determine situations where incidents have occurred and only then put responses into action.
While the IR platforms of yesteryear may have been adequate at mitigating slowly progressing attacks, today’s reality is that slowly progressing attacks are a rarity; damage now happens in the blink of an eye, powered by hostile artificial intelligence (AI) using machine learning to spread rapidly throughout even the largest of enterprises. Add to that the stealthy nature of today’s attacks, and it becomes readily evident that new ideologies are needed to battle effectively against the intelligently automated attacks that are wreaking havoc today.
That is exactly where Ra’anana, Israel-based Secdo comes into play. The company offers an incident response platform which incorporates AI-powered automation that leverages behavioral modeling to detect and respond to security incidents in real-time, effectively closing the window on attackers before any major damage can occur. The company is able to accomplish that lofty goal by integrating endpoint visibility into a platform that can analyze behavior and traffic. The solution also looks for abnormal behavior and then automatically responds. What’s more, it incorporates an active threat-hunting system, which is continually updated to prevent incidents from occurring in the first place. Secdo demonstrates that cybersecurity has now moved into the arena of AI vs. AI, and humans will only become aware of the battle after it has commenced.
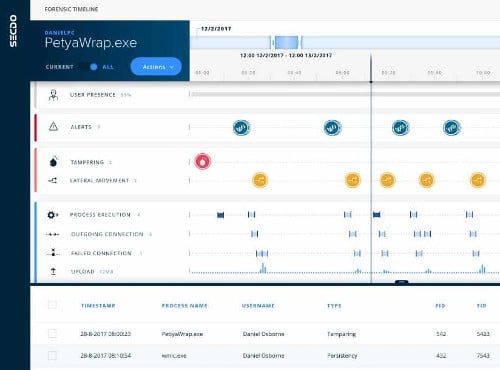
A Closer Look at Secdo Incident Response Version 5.0
To fully appreciate what Secdo’s IR platform is all about, one has to look at all of the components involved, the capabilities instituted and the powerful integration that takes place behind the scenes. Simply put, Secdo IRv5 is much more than the sum of its parts, and those parts are numerous indeed. The technology offered is impressive; however, the integration of all that technology into a single-pane-of-glass view is even more impressive.
Installation
Secdo comes in two flavors: a cloud-based platform or an on-premises platform. The on-premises platform uses Linux-based appliances, which handle all the advanced machine learning analytics. The company offers guidelines on sizing the on-premises hardware, which uses a client-server ideology. The clients are the agents installed on the endpoints, and the servers act as data servers, run the causality analysis engine and support the browser-based management console. Server hardware requirements are significant, with support for 1,000 agents requiring the appliance to have at least 20 CPUs, 64 GB memory, 1.6 TB of RAID 5 storage and a pair of 10G NICs.
Given those requirements, most customers should consider using the cloud-based option, where Secdo provides physical servers in data centers and is responsible for all hardware and communications. What’s more, the cloud-based platform offers unlimited scale and leverages crowd intelligence. In other words, its cloud-based causality analysis learns from all users in real time, as opposed to just the local activity of a single installation.
eSecurityPlanet tested Secdo using the cloud based model. Secdo has data centers all over the world, so latency was not an issue for testing at a NYC-based environment. The cloud offering proved to be incredibly easy to setup, requiring a “no-touch” approach.
The second required component of installation comes in the form of an agent, which is pushed down to every endpoint on the network. Currently, Secdo offers agents for Windows and Linux systems, which covers the majority of business endpoints in use today. Agents can be pushed down to endpoints and managed using the Secdo management console.
Secdo Agents
As mentioned before, Secdo uses a client-server topology, where agents interact with a management/analysis/data server. Agents on each endpoint in the enterprise collect activities and events and send that information to the server for additional analytics. This in turn drives the Secdo causality engine, feeds machine learning algorithms and gives the AI the foundation to identify patterns and trends and make decisions.
Agents can be made invisible to end users, and they require very few resources to function. Agents also take on the role of acting on intelligence. In other words, the agent can take action to prevent an attack from spreading by shutting down processes, disrupting connections, filtering data and so forth. Administrators can define rules that determine which actions are taken and when. The agent uses those rules to execute actions automatically, thus bringing an instantaneous element to incident response. That proves to be one of the most critical advantages offered by Secdo — dealing with incidents automatically, while recording all the relevant activity for later forensic processing.
Hands on with the Secdo Platform
Secdo unifies threat detection with threat response to create what some may consider a fully automated threat identification and incident response system that eschews a human touch. However, as with any security product, human interaction is still an important component of effective security. Where Secdo takes the lead is with the company’s agent-based automated response system that can react to threats faster than any human possibly can. Secdo is able to accomplish that by having the agent monitor network activity, file activity, USB activity, user activity, registry activity, process activity and memory activity — all in real-time. The goal of that monitoring is to identify any anomalous behavior and then take action to prevent that behavior from impacting operations.
Behind the scenes, Secdo continually runs causality analysis across all of the endpoints and servers (at least those running the agent). In the past, causality analysis was usually done after the fact and was part of the security incident event monitoring (SIEM) process that was usually done by hand, leaving it to an IT staffer to determine the who, what, when, where and how of an incident.
Secdo not only answers those questions in real time, it also creates a causality chain that integrates real-time detection systems to better determine the impact of the detected processes. The algorithms behind those causality and detection processes drive automated responses to contain potential attacks, while at the same time creating the information needed to look at the full context of any alert. In other words, Secdo not only prevents malicious code from spreading, it also creates all of the forensics data needed to further investigate an event.
In many situations, Secdo can self-investigate an alert and then use a bevy of tools to respond automatically. That capability reduces the need for human intervention and allows cybersecurity experts to focus on more immediate issues and more complex incidents. Automated incident response does not stop there. Secdo incorporates other technologies as well to bring machine learning into the cybersecurity picture. The platform’s ability to monitor behaviors allows it to self-define new rules that drive automated responses. Over time, the platform learns which assets are critical and are most likely to be attacked, and it can provide that information to cybersecurity staffers so that they can harden systems.
While it might sound like Secdo’s goal is to replace the humans involved with cybersecurity with automation, in actuality Secdo makes humans more effective and allows cybersecurity pros to focus on preventing future attacks, instead of spending countless hours remediating attacks.
One of Secdo’s biggest strengths is the unprecedented visibility it gives cybersecurity professionals into events. The platform records and correlates all endpoint activity at the thread level, allowing investigators to delve deeper into incidents than previously possible. Secdo presents that information via a browser-based console (and dashboard) that supports full drill-down capabilities. That allows investigators to select a data element presented on the screen and, with just a click, dive down further into what constitutes that data element.
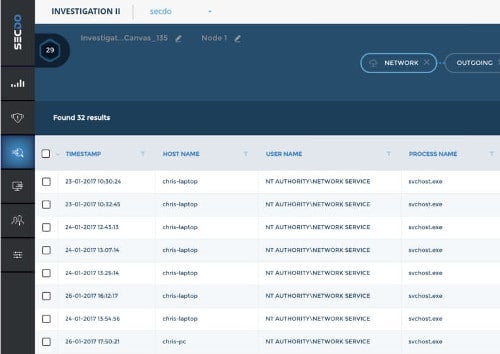
For example, a user could click on a thread displayed in the console and then determine where that thread was running, what other processes interacted with that thread, what hardware was in place, relevant TCP/IP information and so forth. That makes it much easier for an investigator to determine if unexpected behavior was malicious in nature or just an artifact of how code was being executed.
Many of the platform’s capabilities are encapsulated in the different components that make up the platform. Although Secdo is tightly integrated and operates as an advanced, automated service, it is important to note what the primary components are and what they mean to a cybersecurity team.
- Secdo Observer: Observer continuously records all events and behaviors on every system running the Secdo agent. The data is stored on a secure server, which provides the ability for investigators to look at incidents in the past or even in real time.
- Secdo Analyzer: Analyzer powers the automatic alert investigation engine using causality analysis and machine learning to reveal the full context of an alert, determine the behaviors around the alert and correlate activity with forensic data to determine severity and potential actions.
- Secdo Responder: Responder provides rapid response to detected threats and uses AI-driven actions to contain and remediate threats, all without human intervention, and in a matter of seconds so that interruptions are avoided and user productivity remains consistent.
- Secdo Defender: Defender proactively identifies and blocks threats using logic created by studying expected behavior and correlating changes in behavior with potential attack vectors to block any attack before it can spread. Defender uses an adaptive workflow that eases the tuning of rules based upon indicators of compromise, such as malicious code or behaviors. What’s more, Defender can proactively blacklist sites, applications and code to prevent future attacks.
Interaction with any of the platform’s modules is straightforward and uses the normal conventions of browser-based consoles and dashboards. That said, Secdo is almost completely capable of working in a set-it-and-forget-it environment, where cybersecurity professionals need only get involved when Secdo alerts them to behavioral changes or potentially previously unseen threats.
Dealing With The Latest Threats
Secdo’s ability to monitor and adapt proves useful as new threats are discovered. Take, for example, the recently identified Spectre and Meltdown threats that are geared towards compromising Intel CPUs. Normally, threats of that nature are difficult to detect and block, since those threats use flaws in the chip design to compromise data. Secdo’s ability to detect and isolate attack behaviors could potentially identify the abnormal code used to initiate those attacks and then look for issues such as privilege escalation, unexpected account use, unexpected connections or any other behaviors that fall out of normalized expectations. The detection of those events or behaviors would trigger Secdo to block the activity, create an alert, respond to the alert and blacklist the processes, users or sites involved. All forensic evidence would be preserved, allowing cybersecurity investigators to better understand the threat vectors and then implement more permanent solutions.







