At the time it was acquired by Palo Alto Networks in late 2018, Twistlock was in use by 25% of the Fortune 100. Its automated and scalable container cybersecurity platform has now been incorporated into Palo Alto’s Prisma Cloud.
Since the acquisition, Palo Alto Prisma has added Twistlock’s functions to a larger suite of cloud-based functions known as Prisma Cloud. It is a cloud-native security platform with security and compliance coverage for users, applications, data, and the cloud technology stack.
Twistlock was featured on our list of the top container and Kubernetes security vendors, where Prisma Cloud now takes its place.
What Is Twistlock Container Security?
The Twistlock Cloud Native Cybersecurity Platform provided full lifecycle security for containerized environments. From pipeline to perimeter, Twistlock helped customers deploy containers at scale and secure the entire cloud native stack, from the host OS to serverless functions.
As part of the Prisma Cloud, it helps organizations manage rules governing Docker configurations, containers, images, nodes, plugins, and services. They can take advantage of integration with secrets management tools like CyberArk and HashiCorp. They can also ingest Kubernetes audit data and surface rules to identify events to alert on.
Palo Alto integration efforts have resulted in a platform that provides full visibility into all dependencies from containers during the build, deploy, and run phases. Prisma Cloud aggregates and prioritizes vulnerabilities continuously in CI/CD pipelines and containers running on hosts or on containers as a service, in public and private clouds.
Featured PartnersFeatured Partners: Vulnerability Management Software
eSecurity Planet may receive a commission from merchants for referrals from this website
What Are Twistlock’s Key Features?
The Twistlock Platform began as a vulnerability management and compliance tool across the container lifecycle, scanning images and serverless functions to prevent security and compliance issues from progressing through the development pipeline. It also offered continuous monitoring of all registries and environments, defense in depth, cloud-native firewalls, and access control for containers, as well as automated, machine-learning driven runtime defense.
Palo Alto’s Prisma Cloud includes all these features but goes well beyond them to provide protection for critical applications, whether they are in containers, in multi-cloud, or hybrid environments. Prisma Cloud’s capabilities include:
- Securing deployments with Open Policy Agent and craft rules in Rego policy language
- Surfacing all audit alerts and activities in a single pane of glass for analysis
- Scanning container images and enforces policies as part of CI/CD workflows
- Continuously monitoring code in repositories and registries
- Securing managed and unmanaged runtime environments
- Combining risk prioritization with runtime protection at scale
- Full life cycle security for repositories, images, and containers
- Establishing risk prioritization across all known CVEs, remediation guidance, and per-layer image analysis with vulnerability Top 10 lists
- Controlling the alert and blocking severity level for individual and groups of services during build time and runtime
- Minimizing false positives
- Integrating vulnerability management to scan repositories, registries, CI/CD pipelines and runtime environments
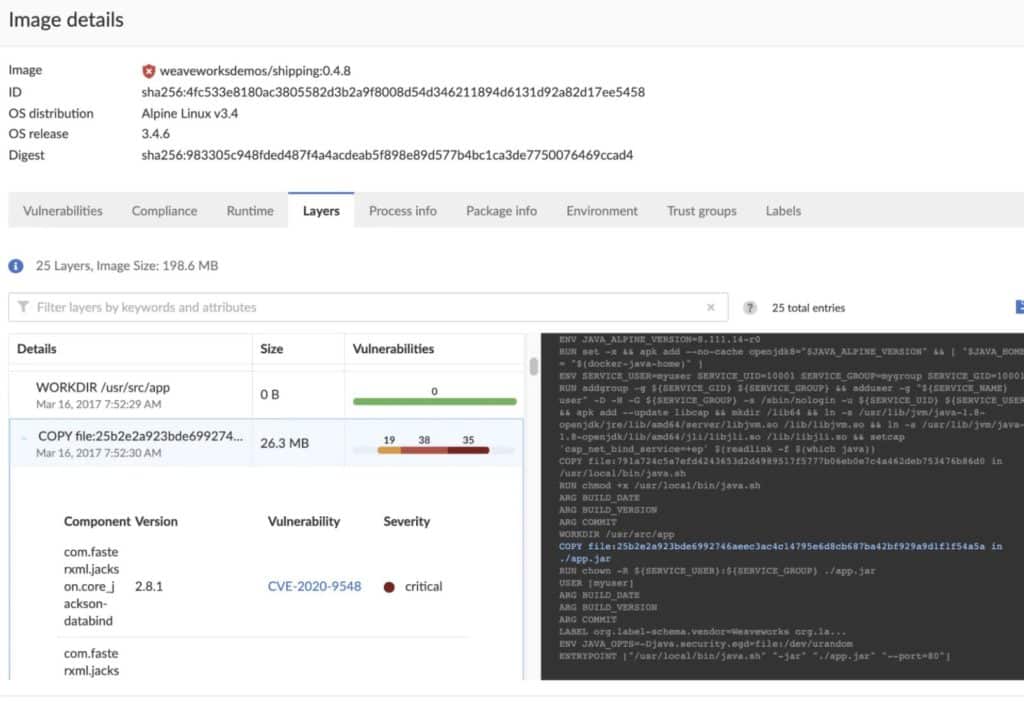
How Well Does It Perform?
Container scans by Prisma Cloud consume 10-15% of memory and 1% of CPU and take about one to five seconds per container. Prisma Cloud tested performance in a scaled-out environment that replicates a real-world workload and configuration. The test environment built on Kubernetes clusters consisted of 20,000 hosts, a console with 16 vCPUs and 50 GB memory, defenders with 2 vCPUs and 8 GB memory running in a container-optimized OS.
A total of 323 images and 192,087 containers were involved – with a density of 9.6 containers per host. The measured resource consumption came out at 1,474 MiB of RAM and 8% of the CPU for the console, and 83 MiB RAM and 1% CPU for the defender. According to Forrester Consulting’s 2021 study, Prisma Cloud helped organizations improve SecOps efficiency, improve DevOps productivity to enable DevSecOps, reduce material data breaches, and improve compliance productivity.
How Is It Delivered?
Prisma Cloud can serve the Kubernetes, Docker, VMware Tanzu, and Red Hat OpenShift container platforms. As the name implies, it is SaaS-delivered via the cloud.
How Much Does Prisma Cloud (formerly Twistlock) Cost?
No pricing data is available on Prisma Cloud.
This article was originally written by Sean Michael Kerner on Dec. 26, 2018 and revised by Drew Robb on Feb. 10, 2023.




