As part of our testing and review of Rapid7 InsightIDR, we looked at the SIEM product’s functionality and ease of use in our lab environment.
InsightIDR has SIEM at its foundation and scales out to essentially be an XDR solution covering endpoints, network traffic analysis, UEBA, incident response and more.
We found InsightIDR to be relatively easy to install. Rapid7’s online documentation is very thorough, and their knowledge base articles helped us navigate a few configuration hiccups we ran into along the way. We had the InsightIDR core services and endpoint monitoring set up in our lab in just a few hours, and started receiving notifications about security events immediately. In the following sections, we walk through the high-level steps involved in getting InsightIDR up and running.
Also read: Testing & Evaluating SIEM Systems: A Review of Rapid7 InsightIDR
Downloading, Installing & Configuring InsightIDR
- Downloading InsightIDR
- Installing the InsightIDR collector
- Configuring InsightIDR event sources
- Installing InsightIDR agents
- InsightIDR pricing
Downloading InsightIDR
The process for getting a 30-day trial of InsightIDR is pretty straightforward. From the trial signup page, you will be asked for your name, company name and email address: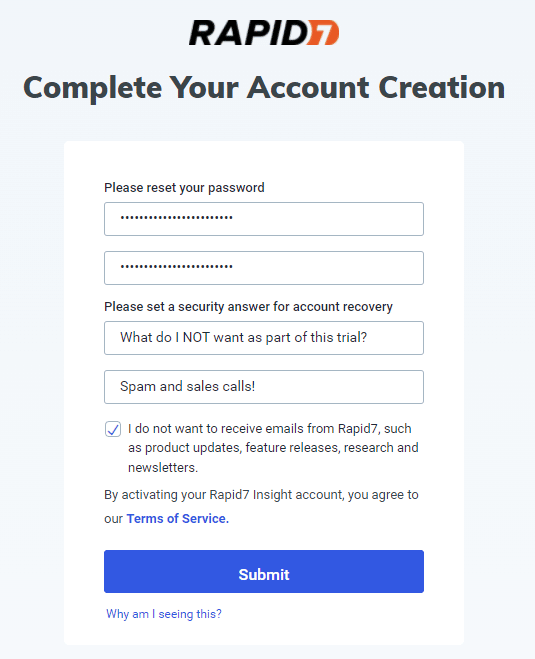
Don’t feel like sacrificing your work email address to the marketing gods? Services like 10 Minute Mail give you access (for 10 minutes) to a throwaway email address for trials like this. However, be careful in that if you ever need to do a password reset with that temporary email address, or access the account for any reason in the future, you may not be able to.
Once your signup is complete, Rapid7’s site offers a nice getting started checklist you can start following to get up and running with InsightIDR:
Installing the InsightIDR collector
InsightIDR has two primary roles that need to be configured: a collector system to ingest logs, and one or more agents that send logs to the collector for analysis. As you might imagine, the collector system needs plenty of disk and RAM horsepower, so be sure to review the collector requirements page on Rapid7’s site to ensure you allocate the proper resources.
Once you are ready to install the collector role, first log into the InsightIDR portal:
From the menu on the left side of the screen, click Data Collection. Then from the menu near the upper right of the screen, click Setup Collector > Download Collector: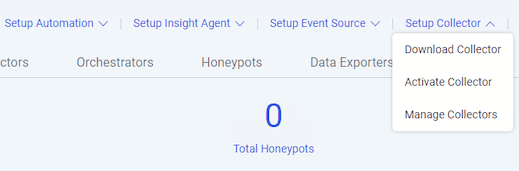
Once you download the appropriate collector (Rapid7 offers both Windows and Linux flavors), run the install executable, which offers a nice installation wizard to walk you through the next steps: 
Near the end of the collector installation, you will be shown an agent key: 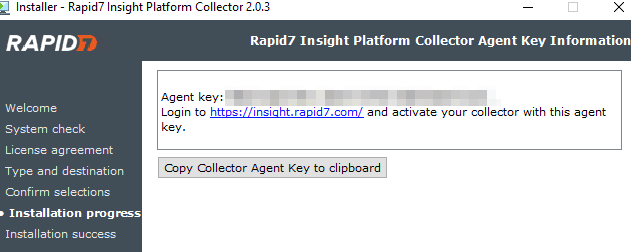
Ensure you click Copy Collector Agent Key to clipboard or take a screenshot of it, as you will need it to set up your agents.
Once the collector installation is complete, head back to the InsightIDR portal, and from the menu on the left side of the screen, click Data Collection again. Then, from the menu near the upper right of the screen, click Setup Collector > Activate Collector. You will be prompted to give the collector a name and also paste in the Activation Token you received during the collector install:
After a few minutes, the new collector should show up in the InsightIDR portal: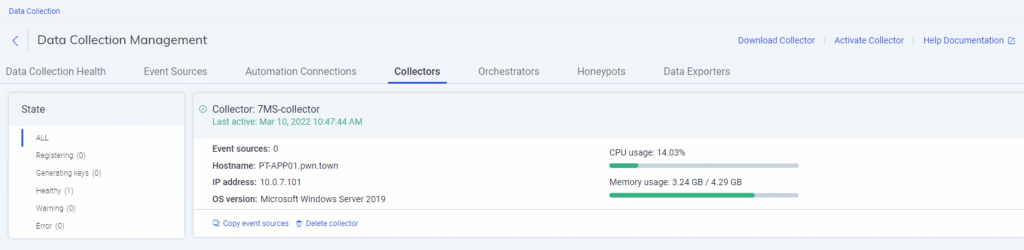
Now you are ready to tell the collector what type of events you want it to collect.
Configuring InsightIDR event sources
Now that you have a collector setup, you need to decide what type of event sources to capture. Rapid7 provides handy auto configure instructions to make this process as smooth as possible. From the InsightIDR portal, click Data Collection again from the menu on the left side of the screen, then click Setup Event Source > Add Event Source. From the next screen that pops up, click Auto Configure:
In our environment, InsightIDR picked up on Active Directory, LDAP and DNS services being present. The Active Directory and LDAP detection was automatic, and ready to go in just a few minutes: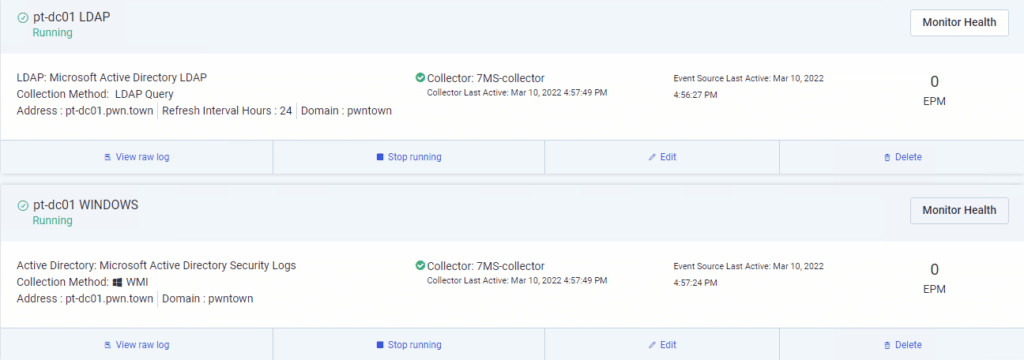
The DNS collection failed during the first installation attempt, but after reviewing the specific instructions for successful DNS collection, we got things working. Follow Rapid7’s instructions carefully, as they walk you through turning up the verbosity of DNS logs and then saving them to a UNC share path that can be accessed by the collector. Once you make the necessary changes, it may take a few moments for the DNS collector to try and reconnect again, but once it does you should be good to go: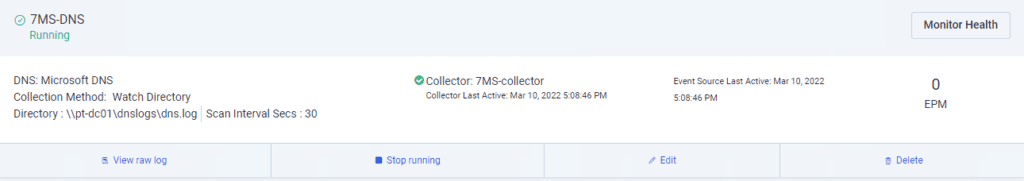
At this point you should be ready to start installing agents on systems you want to collect logs from.
Installing InsightIDR agents
Back at the InsightIDR portal, Rapid7 offers agent installs for Windows, Linux and Mac systems: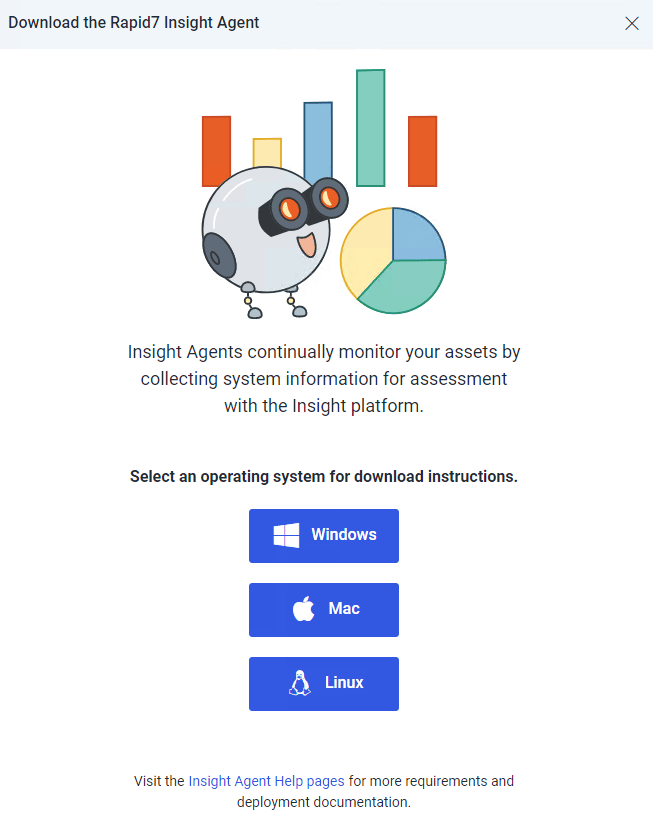
We went with Windows since our environment has all Microsoft endpoints and runs on Active Directory. Rapid7 also offers either a certificate-based or token-based installer. The token-based installer is Rapid7’s preferred method, and we used it to create the base install token: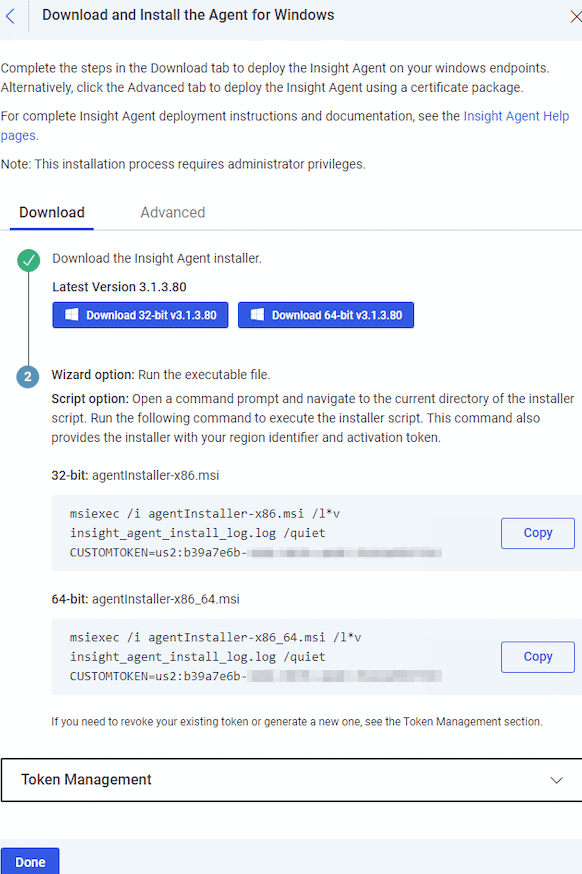
As you can see in the screenshot, this token-based install approach allows you to quickly deploy the agent to multiple systems via a Group Policy Object (GPO). We took the msiexec command from the 64-bit installer, tucked it in a file called install-insight-agent.bat, and then pushed it out via GPO to our endpoints:![]()
If there are any issues with the agent install, reference the system’s insight_agent_install_log.log file. In our environment, the install went smoothly: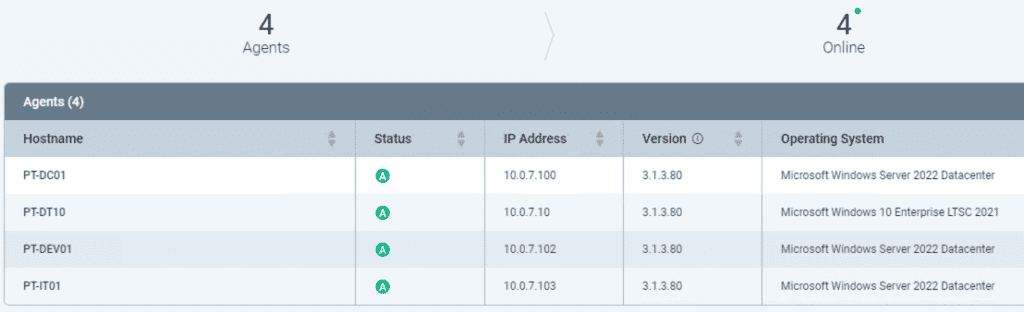
You can also open services.msc on the target endpoint to do a quick sanity check that the InsightIDR service was properly installed: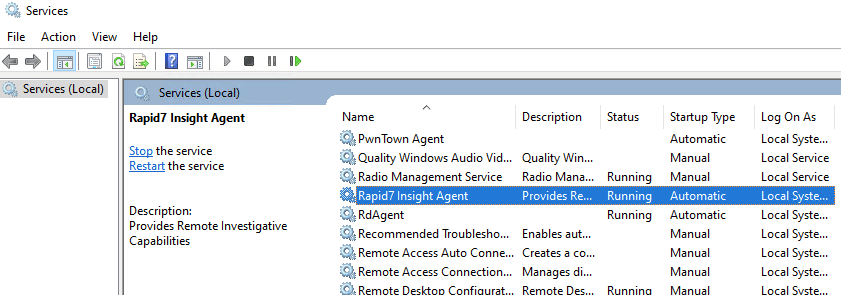
Repeat the agent install process for all endpoints you want to monitor in your environment, and ensure InsightIDR reports them as ready for action:
InsightIDR pricing
InsightIDR pricing starts at $5.61 per asset for 500 assets, with volume discounts for larger environments. For that price users get UEBA, EDR, deception technology, centralized log search and correlation, and automated containment and case management. With revenue growing at about 30% a year, security buyers clearly see value in this feature set.
Other Leading SIEM Tools
Read next:




