Qualys this week launched a new Ransomware Risk Assessment Service that’s designed to help enterprises understand their potential exposure to ransomware and automate the process of patching any associated vulnerabilities or misconfigurations. The service is being offered with a 60-day free trial, after which pricing is based on volume and assets.
With ransomware attacks reaching levels that have required government intervention, security and data backup vendors have responded with products designed to protect data from the crippling attacks.
Qualys senior vice president of product management Shailesh Athalye told eSecurity Planet that the company’s new tool was designed to meet that urgent need. “Every metric and report suggests that organizations around the globe are struggling to defend against today’s more frequent and more sophisticated ransomware attacks,” he said.
While detection and response capabilities can help mitigate the damage caused by such attacks, Athalye said, they don’t help block the attacks in the first place. “This is why authorities like CISA, MS-ISAC and NIST are pleading with organizations to adopt better prevention and ransomware risk assessment strategies,” he said.
Five Years of Ransomware Data
To develop the Ransomware Risk Assessment Service, Qualys examined more than five years of ransomware attacks across more than 30 ransomware families leveraging hundreds of thousands of CVEs in order to determine the most commonly used CVEs and the most commonly targeted software and misconfigurations.
Doing so, Athalye said, can make a huge difference in vulnerability prioritization. “For example, one of the top five CVEs most prevalent across our anonymized client data set has a medium severity and is a privilege escalation vulnerability in JRE,” he said. “This vulnerability is easily overlooked in a normal severity-based prioritization mechanism.”
According to the company, these are the top five CVEs leveraged by leading ransomware families to target organizations worldwide, and several of them more than eight years old:
| CVE | Used by Ransomware Family | Patch Available from Vendor | Patch Available Since | Patchable From Qualys |
| CVE-2013-1493 | Exxroute | Yes | March 2013 | Yes |
| CVE-2013-0431 | Reveton | Yes | February 2013 | Yes |
| CVE-2012-1723 | Urausy | Yes | June 2012 | Yes |
| CVE-2019-1458 | NetWalker | Yes | December 2019 | Yes |
| CVE-2018-12808 | Ryuk/Conti | Yes | August 2018 | Yes |
The service leverages the conclusions of Qualys’ research to provide users with a single consolidated view of their ransomware risks, along with an automated remediation plan – though Athalye noted that they can’t cover every risk, such as phishing and zero-day flaws. “Thus, we recommend organizations adopt defense-in-depth strategies to detect and respond to these attacks via anti-malware, EDR and deception technologies,” he said.
Automated Vulnerability Management
The tool’s dashboard shows all internet-facing assets that are exposed to ransomware-related vulnerabilities or misconfiguration; the number of assets affected by each vulnerability or misconfiguration; the number of unpatched ransomware-related vulnerabilities; the highest-priority ransomware-related vulnerabilities to focus on; one-click and zero-touch workflows to enable vulnerability patching; progress in addressing relevant vulnerabilities and misconfigurations; and CISA best practice guidance for preventing ransomware attacks mapped into configuration controls.
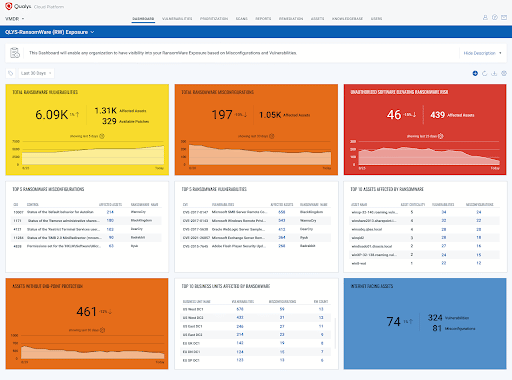
The service leverages data from Qualys sensors deployed in the enterprise environment, which automatically report vulnerabilities and misconfigurations to the Qualys Cloud Platform. “Once identified, these assets are mapped to available patches the team can set for automatic remediation, reducing the company’s ransomware exposure,” Athalye said.
Qualys Zero-Touch Patching can correlate and deploy patch and configuration changes automatically whenever a ransomware-related vulnerability is detected. “Organizations can configure rules to patch software based on application name or a pre-defined criterion,” Athalye said. “Because this patching is cloud-based, it helps free up resources to focus on other priorities and reduces the costs and complexities of traditional patching processes.”
While some competitors offer tools that assess asset risk or vulnerability posture or provide patching workflows, Athalye said Qualys’ offering stands alone in its breadth of functionality and its singular focus on ransomware. “The Qualys platform provides security teams with a comprehensive and real-time view of critical ransomware risks in a unified manner to drive a prioritized remediation plan instead of needing to use multiple point solutions for myopic visibility and remediation,” he said.
Further reading on ransomware protection and recovery:




