By Nazar Tymoshyk, SoftServe
Following Einstein’s wisdom, let me explain why cloud security is important, in terms that make sense to a six-year-old.
Imagine that you have antivirus software installed on your computer that tries to stop attacks directed against it. If that computer is connected to the cloud, it’s connected to other computers and servers all over the world. Some of these computers may be protected while others may not. When one of them gets infected, it puts the entire network in danger.
This weakness led to a brand new cloud security approach: virtual machine introspection (VMI).
In the cloud countless tangible servers launch a couple of virtual machines, which are then sold as a resource where you pay for processing time, memory and other resources. The new approach is based on the absence of a necessity to have an agent who will monitor what is going on inside of each computer, because there is a system that lets you see everything within all the virtual computers.
So if something suspicious is happening, the system itself works as an X-ray, covering the entire cloud and preventing undesirable consequences. It means that cloud providers ensure the safety of their clients’ data.
Here is why VMI security is the best option for cloud security.
Cloud: Environment on Demand
Cloud is like a true friend: always there for you. Its most commonly used type is infrastructure-as-a -service (IaaS), an operating system with certain computing resources provided on demand. Security for IaaS has the same set of issues as any other network and server infrastructure located in a data center. Benefits of using IaaS for security range from cost reduction, flexibility and scalability, to pay-per-use model, utilization, and — most importantly — isolation.
What does this environment on demand have to do with VMI? There are several levels of protection. At the beginning was the sandbox, an execution environment that can restrict access to resources. Then, there is a virtual machine (VM), a heavy-weight sandbox that supports execution of the entire operating systems.
Isolation prevents a guest code from reading and writing outside of a VM. Next, inspection presupposes that a virtual machine monitor (VMM), aka hypervisor, can examine the entire state of the guest system (memory, devices, etc.). Introspection means that VMM can interrupt guest code at any time — so it doesn’t only detect what is bad, but may make “heads roll” (deny access). Compared with antivirus software installed on every computer, VMI provides a higher-level functionality.
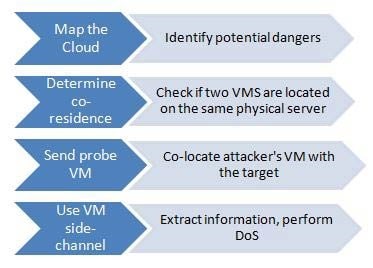 At left is an example of how VM may be used to repel an attacker from your cloud.
At left is an example of how VM may be used to repel an attacker from your cloud.
Here is a list of which kinds of hypervisors are used by well-known cloud providers (NB: all of them are forerunners of QEMU):
- Amazon, Linode, Rackspace and GoGrid use Xen/Citrix Xen hypervisor
- Google Compute Engine, Openstack (for private cloud), Rackspace and IBM use KVM
- Microsoft Azure uses Hyper-V
- Bluelock, CSC, VMWare Cloud, Cloud.com and Cloudstack use VMWare
Key Cloud Threats and VMI Power
The number of threats a cloud may face is limited only by an attacker’s imagination. If a hacker finds a hypervisor’s weak spot, they may invade a range of VMs through one server or defect VMs one by one to steal clients’ data. Another top threat is when an attacker hacks one VM, and then the entire server goes down.
Here is a list of the key threats VMI protects from:
- Unavailability of the cloud
- Compromised vulnerable and old software
- Isolation break out (Blue pill)
- Zero-day vulnerability (unknown exploit)
- Rootkits and Viruses
- Cloud Security Alliance Cloud Computing Top Threats
- OWASP 10 Cloud Risks
- Access keys leakage
Cloud providers need to be able to provide a solution against potential dangers. This is a question of transparency; i.e. if someone has access to your VMs or not, which includes: proof of security hygiene of provider infrastructure to third parties; auditability, certification process, risk analysis methodologies, compliance; and trusted cloud computing technologies that provide cryptographic evidence.
Shedding Light on VMI Security
VMI is an X-ray view of all VM states, including installed applications, operating systems and patch levels. It can be used for detection, protection and management, compliance and automated security enforcement, relying on hypervisor’s capabilities to monitor VM behavior.
VMI offers a full package of security features:
- Malware analysis
- Cloud SIEM
- VM antivirus control
- VM forcing policies
- Rootkit prevention
- VM IPS/IDS
- VM honeypot
- Cloud firewall
- VM patch management
- Invisible system logging
VMI for cloud management provides automated VM compliance assessment based on multiple VM attributes; quarantine of non-compliant VMs to eliminate administrative errors and reduce risk, as well as automated security classification and enforcement for new or cloned VMs.
Opting for VMI security has a number of benefits. First, central processing of security functions is more efficient than distributing security controls and related overhead to each VM. Second, the absence of host agents guarantees security for all VMs, regardless of operating system type and patch level, with no impact on applications running inside the VMs.
The final benefit is tamper-proof security. Host-agents are subject to getting compromised by the very malware they aim to thwart (e.g., Conficker turning off A/V). By contrast, hypervisor-based security resides outside of the guest-VM, and is thus tamper-proof to any malware.
Nazar Tymoshyk is a IT security and network infrastructure expert working for SoftServe, a software and application development company. He specializes in many security disciplines, including computer forensics, malware analysis, intrusion detection and mobile application security assessments. Nazar holds a Ph.D. in Information Security from the State University, Lviv Polytechnics and is the chapter leader of the OWASP in Lviv, Ukraine. He is a regular contributor to the SoftServe United blog.




