-

Top 6 Rootkit Threats and How to Protect Yourself
In the ever-evolving world of malware, rootkits are some of the most dangerous threats out there. A fusion of the words “root” and “kit,” rootkits are essentially software toolboxes. Though not initially developed for malicious purposes, these toolboxes have become potent pieces of malware in the hands of technically-savvy cybercriminals. Common types of rootkits include […]
-

How You Get Malware: 8 Ways Malware Creeps Onto Your Device
Malware can unleash devastating attacks on devices and IT systems, resulting in the theft of sensitive data and money, destruction of hardware and files, the complete collapse of networks and databases, and more. Understanding the attack paths malware uses to invade your systems is important for setting up defenses to stop it. Email and the […]
-
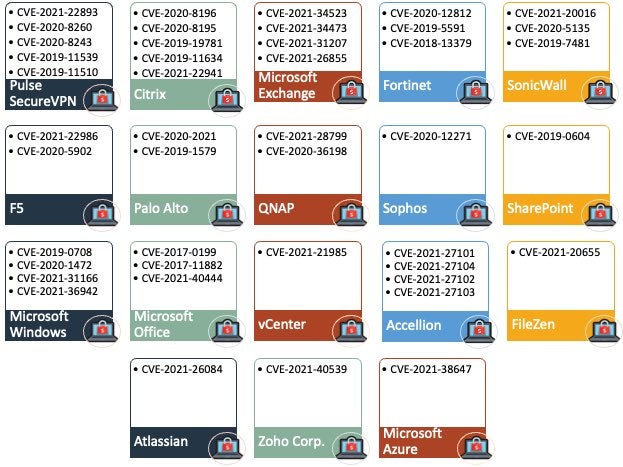
Main Targets of Ransomware Attacks & What They Look For
Ransomware has become a potent tool for cybercriminals looking to exploit companies’ sensitive data for profit. Ransomware attacks have affected businesses across all sizes, locations, and industries, from banking and financial services to utilities to education. When trying to keep your business safe from potential attacks, just as important as any kind of ransomware protection […]
-

What is Malware? Definition, Purpose & Common Protections
Anyone who has used a computer for any significant length of time has probably at least heard of malware. Short for “malicious software,” malware is any piece of computer software designed to disrupt the regular function of a network or device, to gain unauthorized access to certain hardware or systems, or to send user data […]
-
The History of Computer Viruses & Malware
If you’ve used a computer for more than 5 minutes, you probably know a thing or two about computer viruses and malware. On the modern Internet, malware is a near-constant presence. Whether it’s infected emails stealing employee access credentials or the plague of ransomware that has menaced the business world in recent years, there are […]
-

What is Employee Monitoring? Full Guide to Getting It Right
Businesses have long wondered if employees are staying focused and doing their jobs. To answer this question, many in the modern age have turned to employee monitoring software. From facial recognition to surveillance cameras to time trackers to just having a couple guys standing over employees’ shoulders, there are a multitude of ways to make […]
-

Behavioral Analytics in Cybersecurity: Does It Work as Advertised?
In the ever-evolving fight against data loss, data breaches, and data theft in the 21st century, organizations worldwide have turned to a number of cybersecurity solutions, services, and software in an attempt to keep their data safe and secure from threats. One such solution is behavioral analytics, more specifically User and Entity Behavior Analytics (UEBA). […]
-

Best Fraud Management Systems & Detection Tools
Fraud is one of the most prevalent vulnerabilities in the modern world. According to the FTC, over 28 million fraud reports were filed by consumers, resulting in more than $5.8 billion in reported fraud in 2021 alone. This is more than a 70% increase over 2020. Businesses are also at risk of fraud attempts. PwC’s […]
-

The Scammers’ Playbook: How Cybercriminals Get Ahold of Your Data
Cybercrime is a growth industry like no other. According to statistics from the FBI’s 2021 Internet Crime Report, complaints to the Internet Crime Complaint Center (IC3) have been rising since 2017. In 2021 alone, IC3 received 847,376 complaints which amounted to $6.9 billion in reported losses, up from 2020’s 791,790 complaints and $4.2 billion in […]
IT Security Resources
Top Cybersecurity Companies
Top 10 Cybersecurity Companies
Get the Free Newsletter!
Subscribe to Cybersecurity Insider for top news, trends & analysis





