-
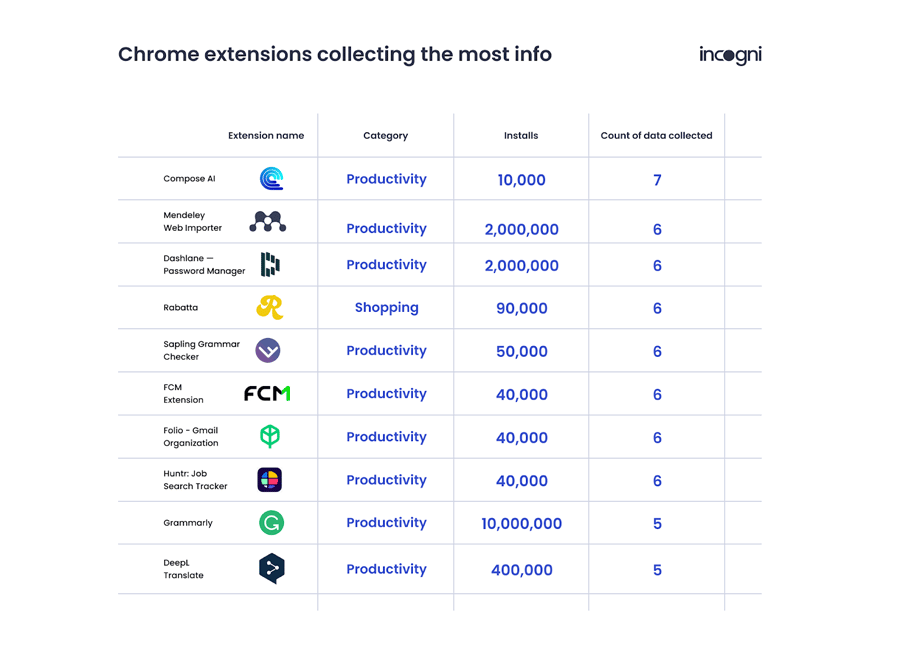
Almost Half of All Chrome Extensions Are Potentially High-Risk
In a recent study of 1,237 Chrome extensions with a minimum of 1,000 downloads, Incogni researchers found that nearly half ask for permissions that could potentially expose personally identifiable information (PII), distribute adware and malware, or even log everything users do online, including accessing passwords and financial data. Almost half (48.66 percent) of all Chrome […]
-
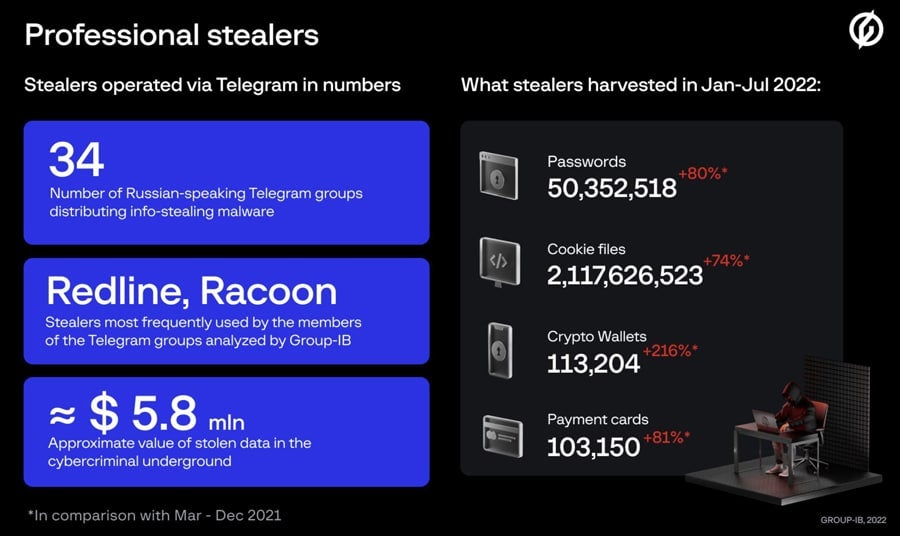
Russian Infostealer Gangs Steal 50 Million Passwords
Group-IB cybersecurity researchers recently identified several Russian-speaking cybercrime groups offering infostealing malware-as-a-service (MaaS), resulting in the theft of more than 50 million passwords thus far. The cybercrime groups are using Raccoon and Redline malware to steal login credentials for Steam, Roblox, Amazon and PayPal, as well as payment records and crypto wallet information. In the […]
-
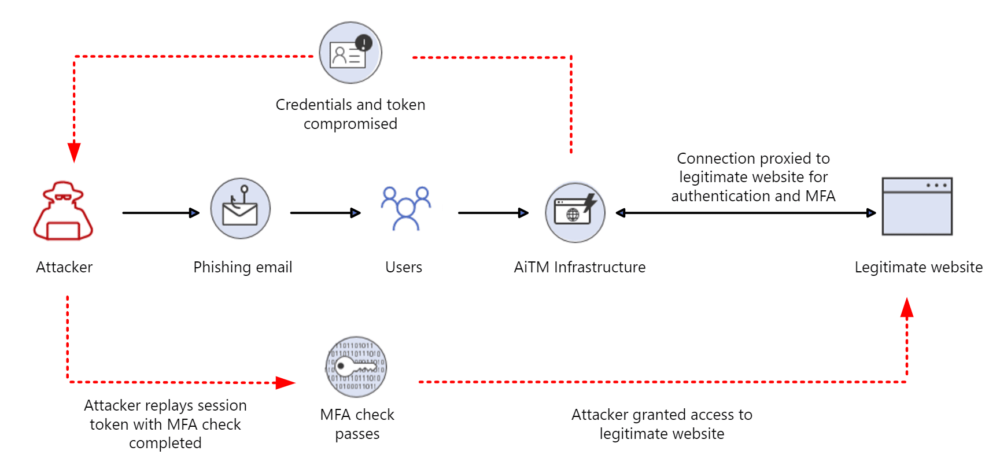
Microsoft Warns of Surge in Token Theft, Bypassing MFA
The Microsoft Detection and Response Team (DART) recently warned that attackers are increasingly using token theft to circumvent multi-factor authentication (MFA). “By compromising and replaying a token issued to an identity that has already completed multifactor authentication, the threat actor satisfies the validation of MFA and access is granted to organizational resources accordingly,” the team […]
-

One in Five Public-Facing Cloud Storage Buckets Expose Sensitive Data
Public-facing cloud storage buckets are a data privacy nightmare, according to a study released today. Members of Laminar Labs’ research team recently found that one in five public-facing cloud storage buckets contains personally identifiable information (PII) – and the majority of that data isn’t even supposed to be online in the first place. The information […]
-
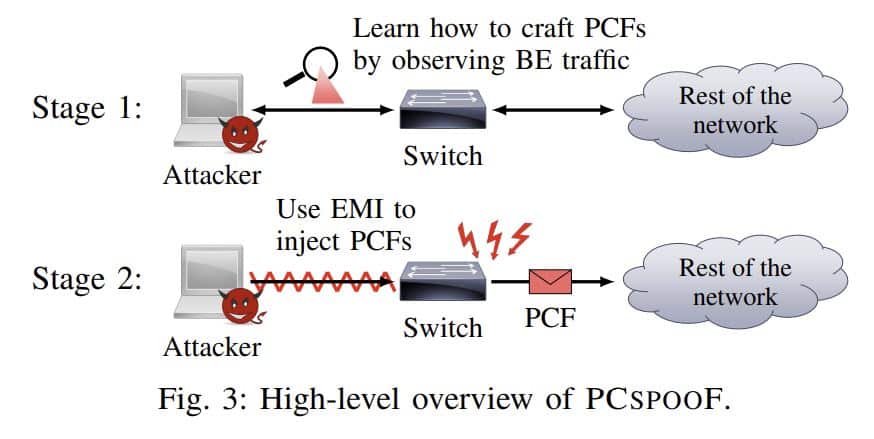
Major TTE Flaw Could Threaten Critical Infrastructure, Including Aircraft
Researchers at the University of Michigan and NASA are warning of a major flaw in the TTE (Time-Triggered Ethernet) protocol, which is used in a wide range of critical infrastructure, including spacecraft, aircraft, energy generation systems, and industrial control systems. TTE reduces cost and improves efficiency by allowing mission-critical devices (like flight controls) to leverage […]
-
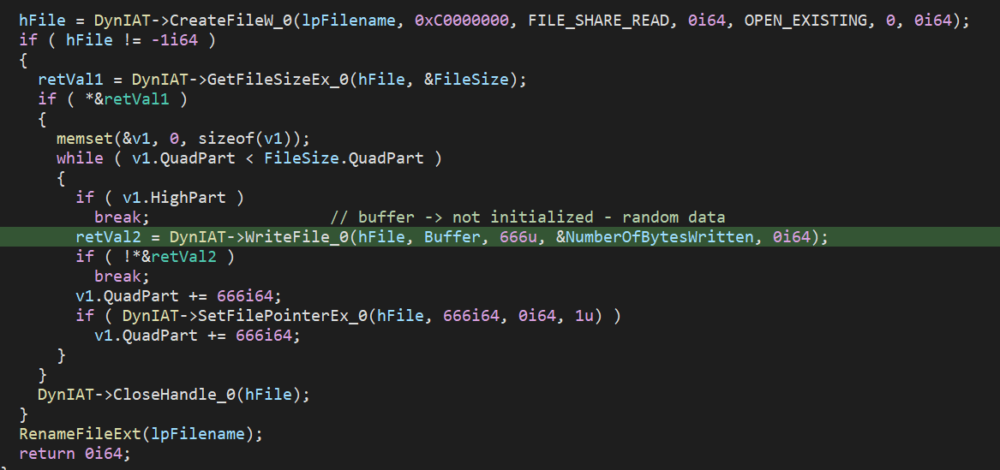
Azov ‘Ransomware’ Wipes Data, Blames Security Researchers
Check Point security researchers recently described the Azov ransomware as an “effective, fast, and unfortunately unrecoverable data wiper,” noting that the malware seems far more focused on destroying data than on any effort to demand a ransom. As Check Point’s Jiří Vinopal put it, “Be careful about this one… If you get infected -> System […]
-
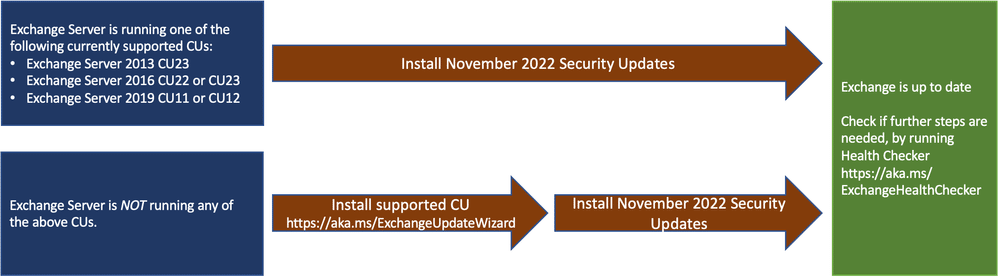
ProxyNotShell Finally Gets Patched by Microsoft
Microsoft’s November 2022 Patch Tuesday includes fixes for more than 60 vulnerabilities affecting almost 40 different products, features and roles – including patches for CVE-2022-41040 and CVE-2022-41082, the ProxyNotShell flaws disclosed last month. “It took Microsoft more than two months to provide the patch, even though the company admitted that ProxyNotShell actively exploited the vulnerabilities […]
-
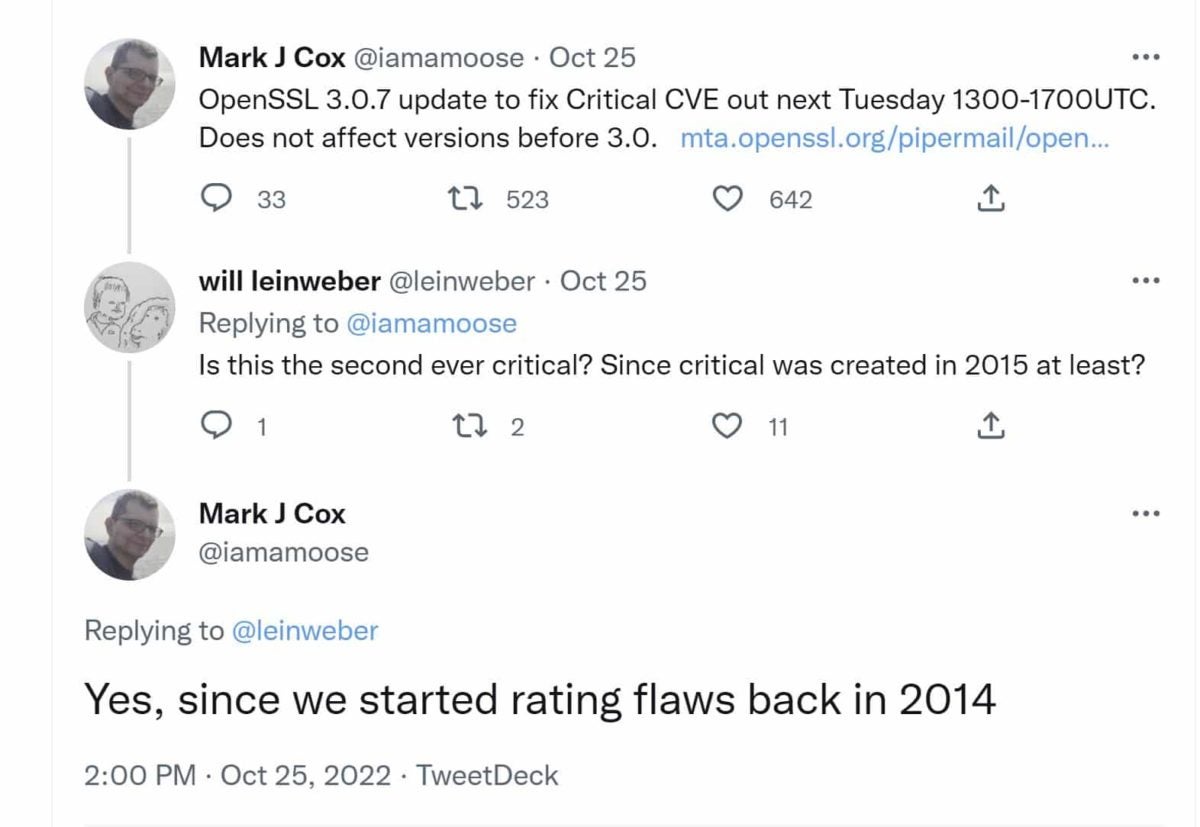
Heartbleed 2.0? OpenSSL Warns of Second-Ever Critical Security Flaw
The OpenSSL project this week announced plans to release version 3.0.7 on November 1 to patch a critical security flaw affecting versions 3.0 and later. Co-founder Mark J. Cox noted it’s only the second critical patch “since we started rating flaws back in 2014.” OpenSSL identifies critical issues as those affecting common configurations and likely […]
-
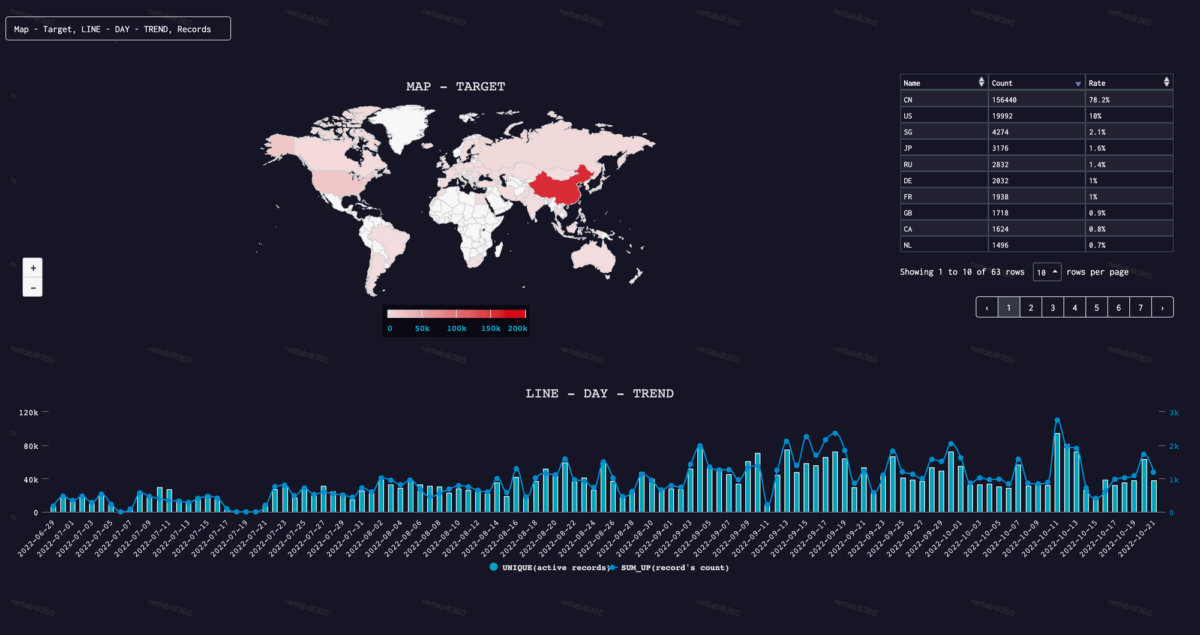
New Version of Fodcha DDoS Botnet Adds Extortion
Back in April of this year, 360 Netlab researchers reported on a new DDoS botnet with more than 10,000 daily active bots and over 100 DDoS victims per day, dubbed Fodcha due to its command and control (C2) domain name folded.in and its use of the ChaCha encryption algorithm. In response to 360 Netlab’s report, […]
-

Data Exfiltration: Symantec Warns of Exbyte Threat as Hive Group Leaks Tata Data
Symantec researchers are warning that a BlackByte ransomware affiliate has begun using a custom data exfiltration tool, Infostealer.Exbyte, to steal data from victims’ networks as part of their attacks. Still, as a recent breach of an Indian power company by a different ransomware group demonstrates, the extra effort of stealing data doesn’t always pay off […]
IT Security Resources
Top Cybersecurity Companies
Top 10 Cybersecurity Companies
Get the Free Newsletter!
Subscribe to Cybersecurity Insider for top news, trends & analysis





