-
ChatGPT’s Dark Side: An Endless Supply of Polymorphic Malware
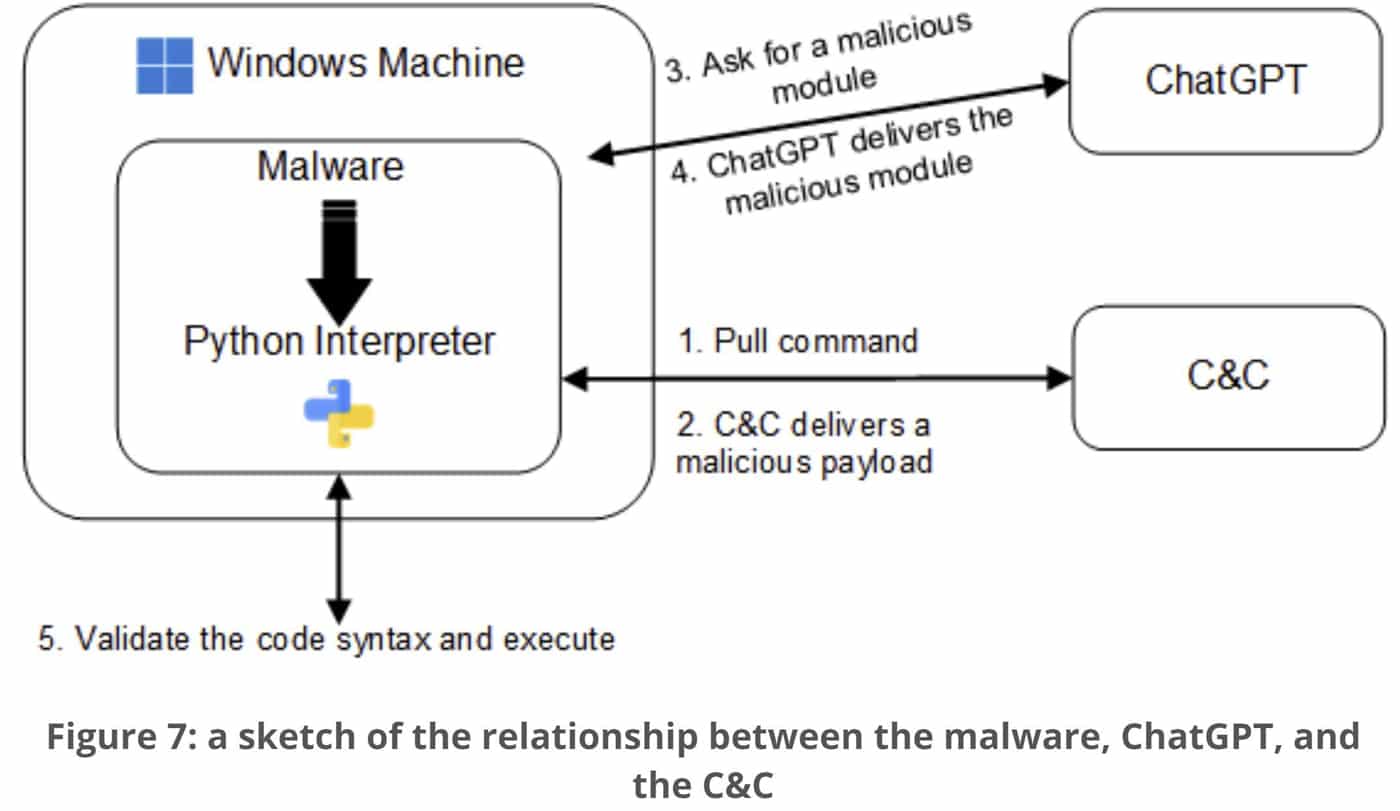
CyberArk researchers are warning that OpenAI’s popular new AI tool ChatGPT can be used to create polymorphic malware. “[ChatGPT]’s impressive features offer fast and intuitive code examples, which are incredibly beneficial for anyone in the software business,” CyberArk researchers Eran Shimony and Omer Tsarfati wrote this week in a blog post that was itself apparently […]
-
Microsoft Patch Tuesday Fixes 11 Critical Vulnerabilities, One Zero-Day
Microsoft’s first Patch Tuesday of 2023 addresses 98 vulnerabilities, more than twice as many as last month – including one zero-day flaw that’s being actively exploited, as well as 11 critical flaws. The zero-day, CVE-2023-21674, is a Windows Advanced Local Procedure Call (ALPC) elevation of privilege vulnerability with a CVSS score of 8.8. The flaw, […]
-
Researchers’ Quantum Threat Debunked, RSA Safe for Now
In a paper published late last month, 24 Chinese researchers suggested that RSA-2048 encryption could be broken using a quantum computer with 372 physical quantum bits. Cryptographer Bruce Schneier drew attention to the paper [PDF] last week in a blog post, noting that IBM recently announced a 433-qubit quantum computer, far exceeding the researchers’ stated […]
-
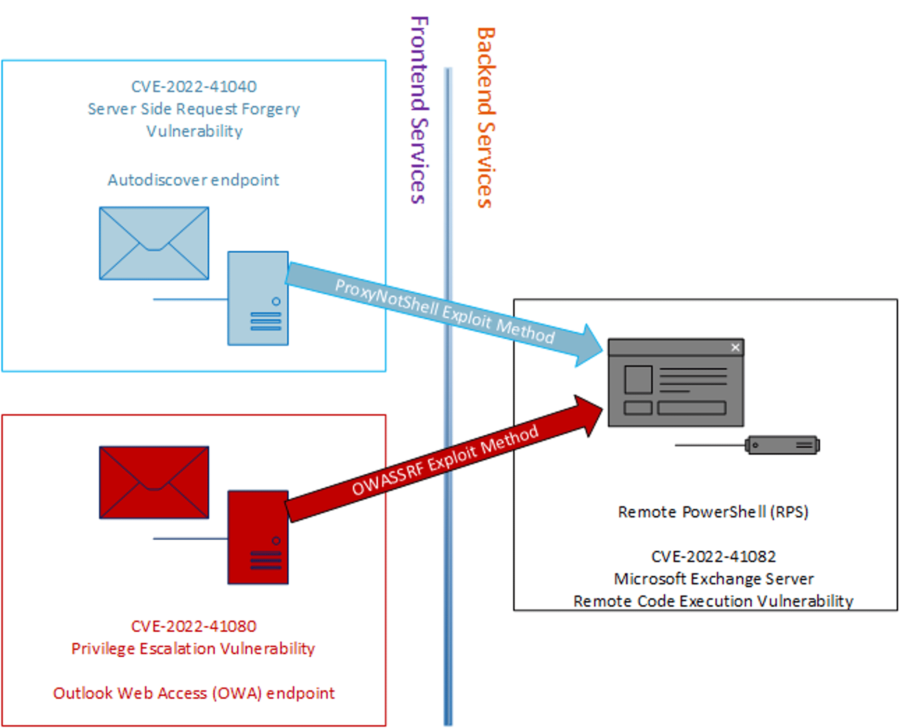
Rackspace Breach Linked to New OWASSRF Vulnerability
Rackspace has acknowledged that it was hit by the Play ransomware a month ago in an attack that compromised customers’ Microsoft Exchange accounts. The attackers apparently leveraged a zero-day vulnerability called OWASSRF that was recently analyzed by CrowdStrike. In an interview with the San Antonio Express-News, Rackspace chief product officer John Prewitt said the company […]
-
Patch Tuesday Fixes Actively Exploited MOTW Vulnerability
Microsoft’s December 2022 Patch Tuesday includes fixes for over four dozen vulnerabilities, six of them critical – including a zero-day flaw in the SmartScreen security tool, CVE-2022-44698, that’s being actively exploited. Regarding that flaw, Microsoft observed, “An attacker can craft a malicious file that would evade Mark of the Web (MOTW) defenses, resulting in a […]
-
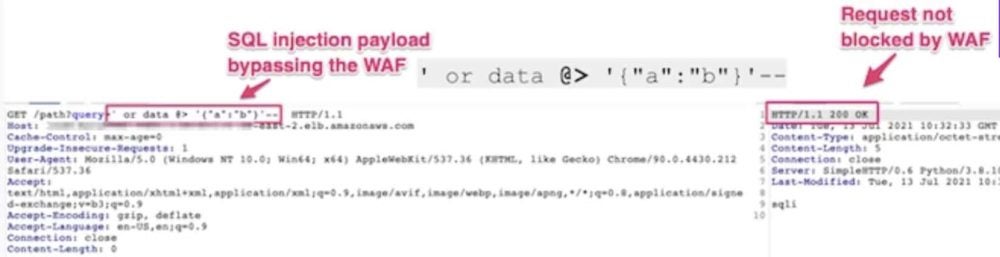
Researchers Warn of Exploit that Bypasses Web Application Firewalls
Team82 researchers have disclosed an attack technique that bypasses industry-leading web application firewalls (WAFs) by appending JSON syntax to SQL injection payloads. “An attacker able to bypass the traffic scanning and blocking capabilities of WAFs often has a direct line to sensitive business and customer information,” vulnerability researcher Noam Moshe wrote in a blog post […]
-
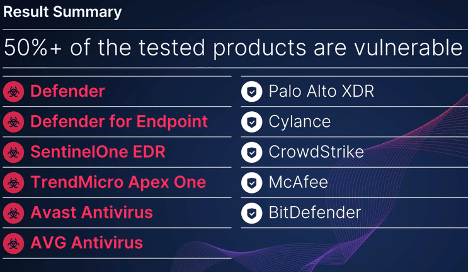
Zero-Day Flaws Found in Several Leading EDR, AV Solutions
SafeBreach Labs researcher Or Yair has uncovered zero-day vulnerabilities in several leading endpoint detection and response (EDR) and antivirus (AV) solutions that enabled him to turn the tools into potentially devastating next-generation wipers. “This wiper runs with the permissions of an unprivileged user yet has the ability to wipe almost any file on a system, […]
-
Average Fortune 500 Company Has 476 Critical Vulnerabilities
In a recent analysis of the public and Internet-facing assets of 471 of the Fortune 500 companies, Cyberpion uncovered more than 148,000 critical vulnerabilities (exploits that are publicly available and actively targeted), with an average of 476 per company. Fully 98 percent of Fortune 500 companies have critically vulnerable internal assets, 95 percent have expired […]
-
HP Wolf Warns of Surge in Malware Hidden in ZIP, RAR Files
Archive files are now the most common file type used to deliver malware – eclipsing Microsoft Office files for the first time – according to HP Wolf Security’s Q3 2022 Quarterly Threat Insights Report. Forty-four percent of malware was delivered via archive files in the third quarter of 2022, 11 percent more than the previous […]
-
Researchers Find Supply Chain Vulnerability in IBM Cloud
The Wiz Research Team recently discovered a supply chain vulnerability in IBM Cloud that they say is the first to impact a cloud provider’s infrastructure. In a dramatic flair, they named the flaw Hell’s Keychain. The security issues were reported to IBM Cloud in late August, and were patched in early September. Before it was […]
IT Security Resources
Top Cybersecurity Companies
Top 10 Cybersecurity Companies
Get the Free Newsletter!
Subscribe to Cybersecurity Insider for top news, trends & analysis