Bad actors are increasingly using a technique called HTML smuggling to deliver ransomware and other malicious code in email campaigns aimed at financial services firms and other organizations, according to Microsoft researchers.
In a blog post, the company’s Microsoft 365 Defender Threat Intelligence Team wrote that the highly evasive technique, which is used to deploy banking malware, remote access Trojans (RATs) and other malicious payloads, was being used by such cybercriminal groups as Nobelium, the notorious Russia-based gang behind the high-profile attack on software maker SolarWinds last year.
The researchers said they had seen Nobelium using HTML smuggling in a spear-phishing campaign in May, and more recently, observed it being used to deliver the banking Trojan Mekotio and the AsyncRAT/MJRAT and Trickbot malware used by attackers to get control of targeted devices and deliver such malware as ransomware.
See also: How to Prevent Ransomware Attacks
What Is HTML Smuggling?
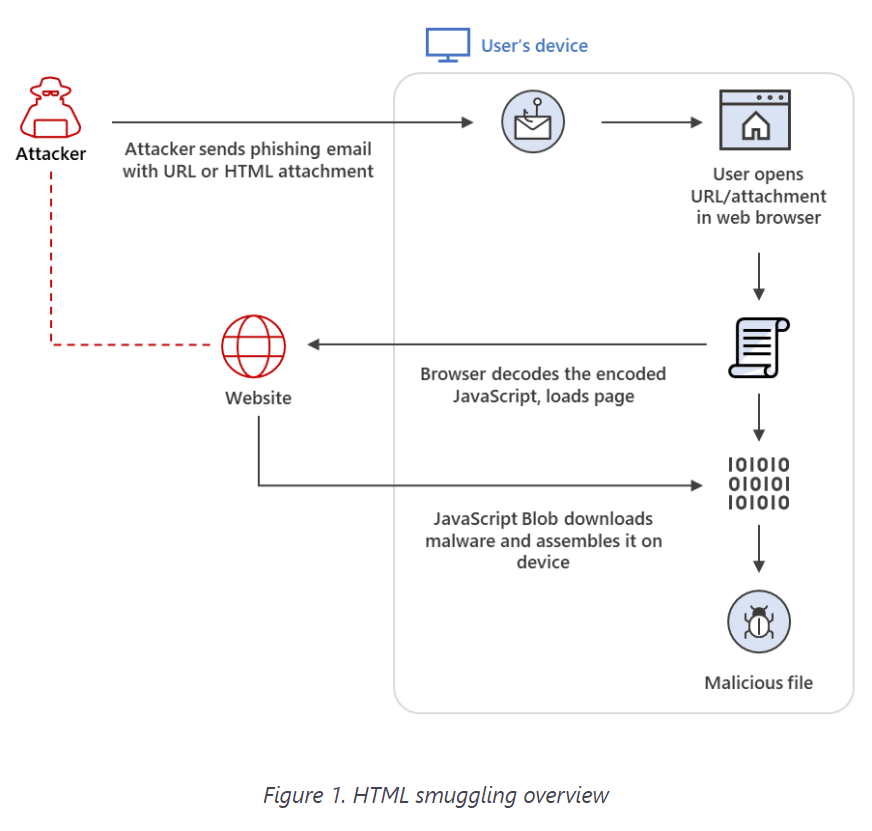
HTML smuggling is an evasive technique that uses legitimate HTML5 or JavaScript features to make its way past firewalls and other security technologies. Essentially, attackers hide an encoded malicious script within a specially crafted HTML attachment or web page. When the victim opens the HTML in a browser, the browser decodes the malicious script, which then assembles the payload on the host device, the researchers wrote.
In this way, rather than having to directly maneuver malicious code through a network, the malware instead is built locally, already behind a firewall.
“This technique is highly evasive because it could bypass standard perimeter security controls, such as web proxies and email gateways, that often only check for suspicious attachments (for example, EXE, ZIP, or DOCX) or traffic based on signatures and patterns,” they wrote. “Because the malicious files are created only after the HTML file is loaded on the endpoint through the browser, what some protection solutions only see at the onset are benign HTML and JavaScript traffic, which can also be obfuscated to further hide their true purpose.”
Also see: Top Endpoint Detection & Response (EDR) Solutions
Hijacking Legitimate Paths
Cybercriminals that use HTML smuggling are betting that the routine use of HTML and JavaScript in everyday operations by businesses will enable them to stay hidden and protected from the businesses’ conventional threat mitigation procedures.
“For example, disabling JavaScript could mitigate HTML smuggling created using JavaScript Blobs,” the researchers wrote. “However, JavaScript is used to render business-related and other legitimate web pages. In addition, there are multiple ways to implement HTML smuggling through obfuscation and numerous ways of coding JavaScript, making the said technique highly evasive against content inspection. Therefore, organizations need a true ‘defense in depth’ strategy and a multi-layered security solution that inspects email delivery, network activity, endpoint behavior, and follow-on attacker activities.”
OJ Ngo, co-founder and CTO of network security solutions vendor DH2i, told eSecurity Planet that HTML smuggling is another example of the continuing evolution of attackers and their tactics.
“Bad doers are getting more and more sophisticated,” Ngo said. “HTML smuggling is just one of many techniques being used to bypass proxies and firewalls. The use of this technique is indeed on the rise. This is a major headache for security product vendors. Everyone is scrambling to update their tools to identify and eliminate the threats. It’s a never-ending cat-and-mouse race.”
Leveraging HTML5 and JavaScript
HTML smuggling uses both the HTML5 “download” attribute and a JavaScript Blog to pull together the payload after it is downloaded into the victim’s device.
“The use of JavaScript Blobs adds to the ‘smuggling’ aspect of the technique,” the Microsoft researchers wrote. “A JavaScript Blob stores the encoded data of a file, which is then decoded when passed to a JavaScript API that expects a URL. This means that instead of providing a link to an actual file that a user must manually click to download, the said file can be automatically downloaded and constructed locally on the device using JavaScript codes.”
Like most email campaigns, what’s necessary to start it off is for a user to click on the malicious attachment or web page. Ensuring that employees – both those in the office and those working from home (a more common scenario since the COVID-19 pandemic) – are educated about how such attacks work and the mitigation procedures available, as well keeping security devices up-to-date or upgrading them, are key to protecting a company, Ngo said.
“Network home routers are so widespread and most of them are outdated or behind on the latest firmware,” he said. “Thus, they’re greatly vulnerable to the attacks. Home users are not the most sophisticated users, so router maintenance is often lacking. Also, cryptocurrencies allow these attackers to collect their ransoms with almost anonymity. Therefore, HTML smuggling is quite effective here.”
At the same time, those workers in the office “can also be less sophisticated” with networking proxies and firewalls, Ngo said.
Also read: The Best Wi-Fi 6 Routers Secure and Fast Enough for Business
Technique Used in Multiple Campaigns
Microsoft researchers have seen HTML smuggling used in a growing number of campaigns. That includes banking malware attacks attributed to Mekotio (DEV-0238) and Ousaban (DEV-0253), which targeted victims in Brazil, Mexico, Spain, Portugal and Peru.
Beyond such banking malware campaigns, other cyberattacks, including ones that they said are more sophisticated and targeted, are using the technique.
‘TTPs get commoditized when deemed effective’
“Such adoption shows how tactics, techniques, and procedures (TTPs) trickle down from cybercrime gangs to malicious threat actors and vice versa,” the researchers wrote. “It also reinforces the current state of the underground economy, where such TTPs get commoditized when deemed effective.”
In May, Microsoft outlined a spear-phishing campaign by Nobelium in which the emails contained an HTML file attachment that, when opened, used HTML smuggling to download the payload into the victim’s device.
Since then, the use of HTML smuggling has cropped up in other campaigns. There was a rise in the use of the technique between July and August in campaigns that delivered RATs, such as AsyncRAT/NJRAT. In September there was another campaign that used emails to deliver Trickbot, an effort that Microsoft linked to an emerging and financially motivated cybercriminal gang that the software giant has tagged as DEV-0193.
Trickbot Attacks
In the Trickbot campaign, the bad actors use a specially created HTML page as an attachment to an email message made to look like a business report.
“When the target recipient opens the HTML attachment in a web browser, it constructs a JavaScript file and saves the said file in the device’s default Downloads folder,” the researchers wrote. “As an added detection-evasion technique against endpoint security controls, the created JavaScript file is password-protected. Therefore, the user must type the password indicated in the original HTML attachment to open it. Once the user executes the JavaScript, it initiates a Base64-encoded PowerShell command, which then calls back to the attacker’s servers to download Trickbot.”
DEV-0193 targets organizations in the healthcare and education industries and works closely with ransomware gangs, including those behind the high-profile Ryuk ransomware.
“After compromising an organization, this group acts as a fundamental pivot point and enabler for follow-on ransomware attacks,” they wrote. “They also often sell unauthorized access to the said operators. Thus, once this group compromises an environment, it is highly likely that a ransomware attack will follow.”
Further reading: Microsegmentation Is Catching On as Key to Zero Trust




