By Jeremy Moskowitz, PolicyPak Software
In the case of your typical Windows domain network, it is “traditional wisdom” that only Microsoft DNS must be used with Active Directory for internal DNS resolution. Many times this is because:
- It’s convenient to use the in-box solution
- The myth that Active Directory requires Microsoft DNS to function properly
- Others are doing Active Directory-integrated DNS, and therefore that way must be the only way to do it
There are some advantages of utilizing Active Directory-integrated DNS for your DNS zone besides the mere convenience of the in-box wizard. The primary benefits are Active Directory replication will take care of DNS zone replication automatically, and all DNS servers are writable
This reduces the necessity to configure and allot for separate DNS zone transfer traffic. Other benefits include secure updates and DHCP integration, but these features are available in third-party solutions as well.
Do You Really Need Microsoft DNS
Active Directory-Integrated DNS is an option but not required.
It is simply a myth that Microsoft DNS is required for Active Directory. In fact, Microsoft even published a KB article dispelling this myth many years ago. The key point is iterated multiple times in multiple ways among Microsoft’s documentation surrounding Active Directory and DNS.
This can be found in the full Microsoft Technet article here: https://technet.microsoft.com/en-us/library/cc755717(v=ws.10).aspx
Note that this article refers to BIND (Berkeley Internet Domain Name) type servers. But to be clear and specific, as the quote states: You can use other DNS servers with Active Directory, and they don’t need to be specifically BIND. The third-party DNS server you choose simply needs to support Active Directory and some rudimentary RFC standards governing DNS communication that most non-Microsoft DNS servers support.
Other articles which clearly reference Active Directory interoperability with non-Microsoft DNS servers are:
Interoperability with Other DNS Servers: https://technet.microsoft.com/en-us/library/cc959268.aspx
Verifying your Basic DNS Configuration [With non-Microsoft DNS]: https://technet.microsoft.com/en-us/library/cc959303.aspx
Linux to Windows Migration (Configuring Berkeley Internet Name Domain (BIND) to Support Active Directory): https://technet.microsoft.com/en-us/library/dd316373.aspx
Another place you can see that Microsoft-specific DNS is optional is in the Domain Controller promotion process. If you are creating an AD Forest for the first time, the wizard does not require you to select DNS. Notice how the wizard will allow you to continue with the DC promotion process despite not choosing to install the Microsoft built-in DNS server component as is shown in the screenshot below.
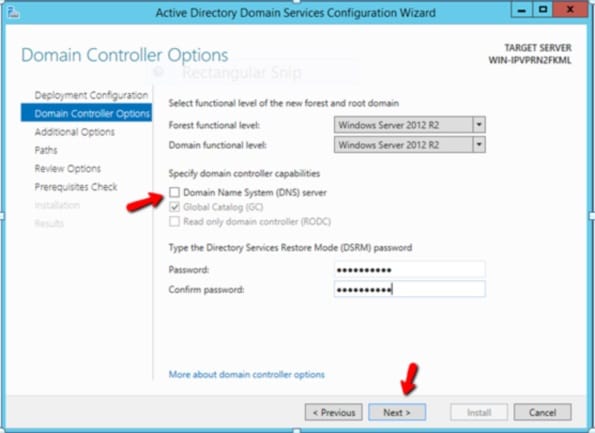
The Case for Non-Microsoft DNS
Active Directory administrators naturally want Active Directory to perform at its highest capabilities. The key activities that Active Directory and its domain controllers should be performing are:
- Authentication
- Authorization
- Accounting (logging)
Everything else that Active Directory and its DC are tasked with doing will take away from these critical aspects. By integrating DNS into your DCs, you are giving it a task which would necessarily take away from these critical activities.
Additionally, your DNS servers should be especially protected and especially secure. In the case of an attack on DNS, like a DDoS (distributed denial of service) attack (akin to SQL Slammer and attacks like those, but expressly for DNS), a Microsoft Active Directory-integrated DNS could have issues since it would be tasked with the DNS and the critical activities described above.
So what is the incentive to not utilize the convenience of exclusively utilizing Microsoft DNS servers?
Here is a list of some of the value-added features offered by third-party DNS solutions available today:
- Proactive automated adaptive behavior protection from DNS attacks, malware and data exfiltration through customized DNS firewall security
- Utilize DNS and DHCP features that are unavailable from Microsoft in-box solutions such as Identity Mapping (linking IP addresses to users)
- Intelligently resolve queries and direct traffic according to geographic location
- Increased logging to help determine where issues and attacks are originating
- Utilizing a single solution for external and internal DNS (aka “single view”)
- Operating system-agnostic way to manage DNS
- Increased security by reducing admin privilege usage
- Increased granularity for control of dynamic DNS updates via IP-based access-control, as opposed to the Microsoft’s three-level approach of “none,” “secure only” (i.e., AD-integrated clients (GSS-TSIG)) or “secure and insecure” (i.e., anyone, no TSIG or IP-based authentication required)
Conclusions on Non-Microsoft DNS
Microsoft has always conceded that any compliant DNS solution will work alongside Active Directory. In short, there is no imperative to use Microsoft DNS with Active Directory. And real Active Directory customers are working just fine with this configuration.
Getting started with non-Microsoft DNS doesn’t have to be hard. Like anything, it’s a process, but that process doesn’t have to be particularly difficult.
If you’re interested in non-Microsoft DNS because of some of the items you’ve read here today, then you should investigate the features and functions you need and start a trial with non-Microsoft DNS.
It’s my hope you have a new perspective on where non-Microsoft DNS can help you out.
Jeremy Moskowitz is one of less than a dozen Group Policy MVPs worldwide, is the most-published author on Group Policy and a prolific Group Policy speaker worldwide. He’s also the founder of GPanswers.com and PolicyPak software. Since becoming one of the world’s first MCSEs, he has performed Active Directory desktop implementations for some of the nation’s largest organizations.
Jeremy has spoken at just about every existing Windows conference about AD and Group Policy, including Microsoft TechEd, Microsoft Ignite, Microsoft Management Summit, WinConnections and TechMentor.




