Email has long been described as the “killer app” that attracted masses to the Internet starting in the mid-90’s. By one estimate, as of May 2009 some 247 billion emails are sent per day. Despite its massive and widespread use, the vast majority of these emails are relatively insecure.
A conventional email message is vulnerable to several kinds of compromise. For example, because message senders can be easily forged, you cannot be sure that the sender is who they claim to be; or that the message text has not been tampered with. Plus, email text itself is not generally encrypted, meaning that if someone hacks access to your inbox, they can view your messages.
Security baked right in
In fact, it is possible to secure email against both of these vulnerabilities. There are several technologies available, but the one we’re going to look at today is called S/MIME and support for it is already built into most desktop email clients, including Outlook, Apple Mail, and Thunderbird.
The S/MIME standard is based on public-key cryptography. In this specification, an individual user owns a digital certificate which contains a public key and a private key. The private key is held only by its owner; the public key is shared with contacts. With the keys in place, you can use your email client to attach a digital signature to outgoing emails, or to encrypt the content of an email, or both.
Signed and encrypted
When a user receives an email with a digital signature, a mail client that supports S/MIME will display an icon showing that the message has been signed. Often you can click this icon for more information, which usually boils down to verification that the message has not been altered. In truth, the digital signature ensures that the message was sent by someone with that sender’s digital certificate installed. Presumably this is the person you think it is, although technically it could be someone who had access to that sender’s computer, or stole his or her digital certificate.

The Apple Mail message composer includes icons for S/MIME encryption and signing if you have a digital certificate installed.
A message that also includes encryption will display normally in an email client that contains the recipient’s private key. If you view the message from a client without the recipient’s private key (say, a hacker has broken into your inbox from their own personal computer), they will only see an attachment containing gibberish instead of the real message content.
With a few simple steps, you can begin signing and encrypting emails yourself. Remember that to send encrypted messages, you will need your recipient’s public key, and for he or she to view them, he or she will need to be using a client with his or her private key–we’ll talk about how that happens below.
Step 1: Get your digital certificate
The first thing you need is a digital certificate that contains your keys. The easiest and most preferred method for obtaining a certificate is through a CA, or Certification Authority. You can get one for free from several vendors, although they will come with varying lengths of expiration periods. Typically, you can buy from same vendors a longer lasting certificate for a modest fee.
For this example, we will obtain a free digital certificate from Comodo, which is good for one year. To do so, visit the Comodo Free E-mail Certificate site. Once there, click through on the free certificate. You will be asked to fill out a form with a few basic details, such as your email address and name. Be sure to enter the same email address that you will be using in your email client!
Comodo will send you an email containing a link to your certificate. When you open this link, your browser will automatically install the certificate. Precisely where the certificate winds up installed depends on your software:
Firefox: The digital certificate will be installed in Firefox’s own key cache. You can access this cache via Tools/Options/Advanced/View Certificates/Your Certificates.
Internet Explorer: The certificates can be accessed through the Windows Control Panel/Internet Options/Content/Certificates/Personal.
Safari on OS X: Certificates can be access through the Keychain Access application/My Certificates.
When using Outlook or Apple Mail, these clients should see your digital certificate in the OS-installed location. If you are using a third-party mail app, such as Thunderbird, you’ll need to import your digital certificate. To do this, you’ll first need to export (sometimes called “backup”) your certificate into a so-called P12 file:
Using Firefox, you can export your certificate by navigating to the certificate cache as described above, selecting your certificate, and then clicking “Backup.”
Internet Explorer users navigate to the certificate as described above, then select the certificate and click “Export.” In the Certificate Export Wizard, select “Yes export the primary key” and then choose the PKCS 12 format.
Apple Keychain users can simply select the certificate and choose File/Export to output the certificate in P12 format.
To import your digital certificate into Thunderbird, open Thunderbird and click to Tools/Options/Advanced/Certificates/View Certificates/Your Certificates/Import.
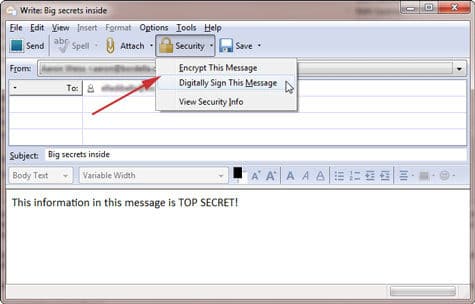
The Thunderbird 3 compose new message window includes a Security menu for S/MIME signing and encryption.
Step 2: Sending a signed email
Now that your email client can access your digital certificate, you can send an email with a digital signature. We’ve already talked about one reason to do so—to certify that you are the message sender. But there’s another reason, too—to provide your certificate to a recipient.
Below, we will look at sending encrypted mail. You can only send encrypted mail to a recipient whose digital certificate you already have; but you can send a digitally signed message to anyone. Therefore, when you send a digitally signed message to a recipient, that recipient receives your public key. After that, they can send you encrypted email. Likewise, when someone else sends you a digitally signed message, you will receive his or her public key, and can send them encrypted messages.
When your email client detects your digital certificate is installed, the window for composing a new message will typically include a menu item or icon for applying your digital signature. See the included screenshots (above and below) for examples from the three major email clients.
Step 3: Sending an encrypted email
In fact, sending an email with content encrypted is no more difficult than sending an email with a digital signature. Any email client that supports S/MIME will provide both signing and encryption as simple checkbox or icons you can toggle on or off as seen in the example screenshots.
Remember that, unlike a digital signature alone, you can only send an encrypted email to a recipient whose public key you already have received. Otherwise your email client will display a warning that the message cannot be encrypted. You can receive the recipient’s public key by asking them to first send you an email that they have digitally signed.

S/MIME encryption and signing buttons in the Options menu of Outlook 2010.
Limitations of S/MIME
Using S/MIME encryption is not without its drawbacks. For one, the major webmail clients, including Gmail and Hotmail do not have built-in support for sending or receiving messages with S/MIME security features. One workaround is to use a browser add-on, such as Gmail S/MIME for Firefox. Another is to configure your webmail service, such as Gmail, to deliver mail by POP or IMAP and use a desktop client with S/MIME support. (Not all webmail services offer this option.)
Also note that when you send or receive an encrypted message, that content is shielded not only from prying eyes, but from software, as well. Therefore, if an encrypted message contains malware, anti-malware scanners will not be able to detect it. Also, encrypted message content may not be properly indexed by your mail client or OS search.
On the other hand, these “limitations” of S/MIME security may actually be seen as desirable depending on why and how you use secure mail.
Aaron Weiss, Wi-Fi Planet’s Wi-Fi Guru, is a networking and Wi-Fi enthusiast based in Upstate New York.
For more email security tips, follow eSecurityPlanet on Twitter @eSecurityP.