If you carry corporate information on a standard USB flash drive and it gets lost or stolen, the resulting data breach can be catastrophic. That’s why you should carry your data on an encrypted flash drive.
In fact, in many cases the use of an encrypted flash drive is required for regulatory compliance or data protection law.
The easiest way to ensure that data on flash drives is protected by encryption is to buy an encrypted flash drive such as the IronKey or Aegis Secure Key, both of which encrypt data automatically in hardware and can be used on computers running Windows, Linux and Mac OS X.
If you’re in the market for an encryption solution for your enterprise, see our list of top enterprise encryption products
The Ironkey requires a password to be typed into a window that pops up on screen before files on the drive can be accessed, while the Aegis Secure Key requires a PIN or password to be entered using tiny keys on the flash drive itself before its contents can be accessed.
The drawback of these types of encrypted flash drives is that they are expensive – an 8GB Aegis Secure Key costs around $100 – and may not always be available. The good news, though, is that it is relatively straightforward to encrypt the contents of any flash drive using free software.
How to Encrypt a Flash Drive Using Microsoft’s BitLocker
A typical business user works from a Windows PC in their office and a Windows laptop while on the move or when working from home. If that use case is similar to your own, the easiest way to encrypt the contents of your flash drives is to use BitLocker, the drive encryption system built into the Ultimate, Enterprise and Pro versions of Microsoft’s Windows Vista and later.
BitLocker Pros: Free; available in many business versions of Windows; very easy to use; requires no extra software downloads
Bitlocker Cons: Only designed for Windows computers (although software is available for purchase that allows the use of BitLocker on other operating systems, e.g. M3 Mac BitLocker Loader)
To encrypt a flash drive with BitLocker:
Right click on the drive you want to turn into an encrypted flash drive in Computer, and select Turn on BitLocker.
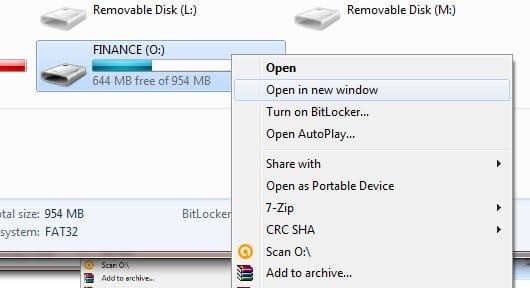
Wait while BitLocker initializes the drive.
Select “Use a password to unlock the drive” and enter and re-enter a password that will be used to unlock the drive.

Save a recovery key or print the recovery key and keep it in a safe place. You will need this to access the drive if you ever forget the password.
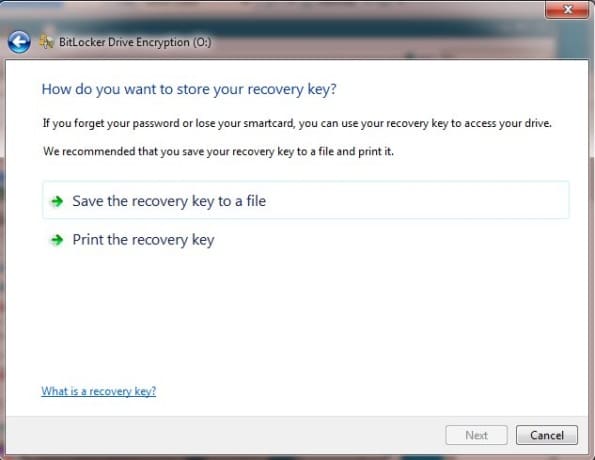
Click “Start Encrypting” to encrypt the drive and its current contents. Depending on the size of the drive, this may take between 5 minutes and an hour.
Once the process is complete, your drive is an encrypted flash drive and you can only decrypt and access the contents after you supply the password.
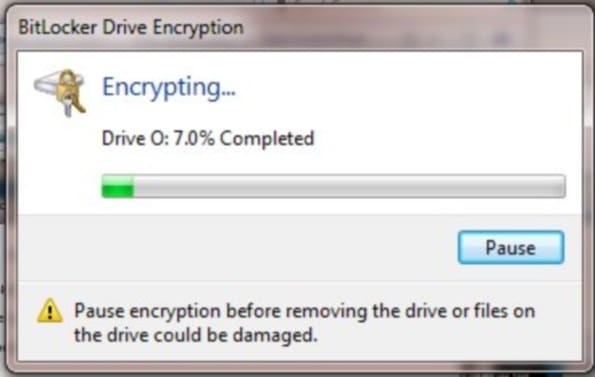
To access files from an encrypted flash drive that was encrypted with BitLocker:
Insert the encrypted flash drive in another Windows computer. A password entry window will pop up:
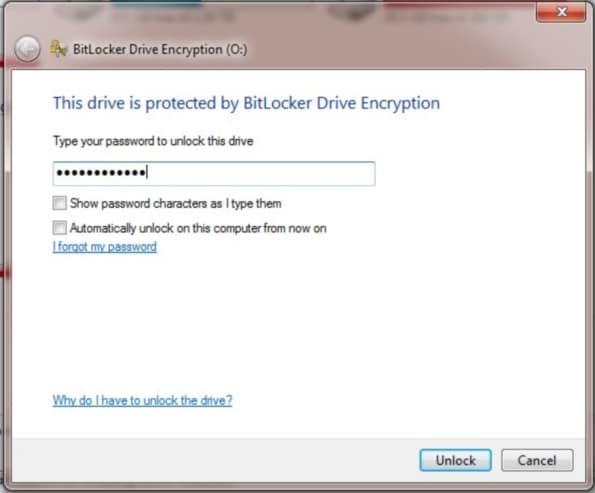
After entering the correct password the drive will be unlocked and you can access the files normally.
BitLocker options
Right clicking on the flash drive in Computer when it is unlocked brings up an option screen:
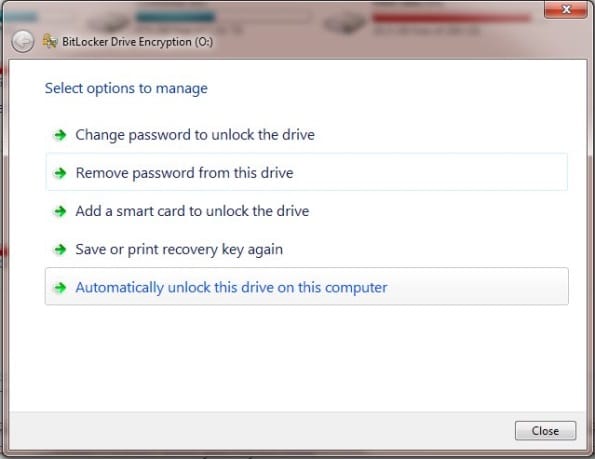
The most important option here is the ability to change the password, which you should do if you suspect that the existing password for your encrypted flash drive may have been compromised.
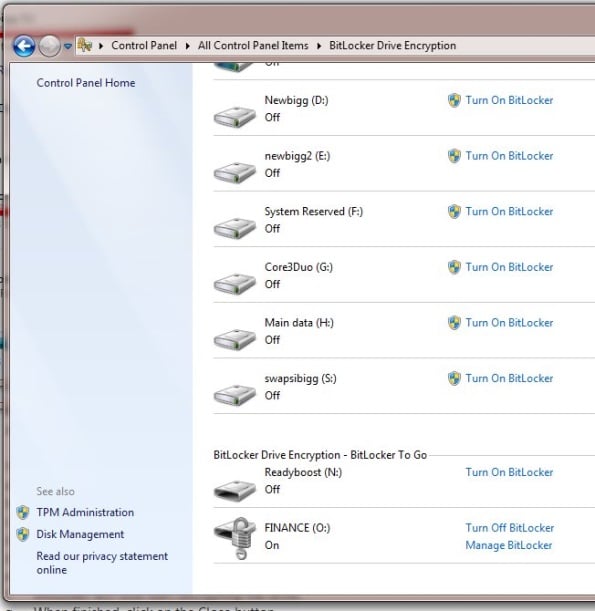
To turn off BitLocker encryption and return the encrypted flash drive to its previous unencrypted state, go to BitLocker Drive Encryption in Control Panel, and turn off encryption for your USB flash drive.
Risks of Using an Encrypted Flash Drive
Passwords
Since all that is needed to decrypt an encrypted flash drive is the password, it follows that the security of the drive is only as strong as the security of the password. The contents of the drive may be compromised if your password is obvious or easily guessable, if you write down the password, or if you are tricked in to revealing your password by social engineering.
Your password can also be compromised if you enter it on a computer that has been compromised and is running key logging software. (It may also immediately make copies of files as soon as they are encrypted, and for that reason you should never decrypt confidential files on any public computer.)
There’s also a risk that the data stored on your encrypted flash drive could be permanently lost if you forget your password and do not have a way or recovering it (such as using the BitLocker recovery key, or simply writing it – or a clue – down somewhere and storing it securely).
Encryption Backdoors
An encryption system is only secure if it has been implemented correctly and the authors of the software have not introduced an intentional weakness or “backdoor” such as a master password.
Since the source code to BitLocker is not open to inspection, it is not possible to independently check the code for backdoors. (Even if the code was open for inspection there is no guarantee that any backdoor would be spotted.)
But even if the code was open, BitLocker is used on computers running Windows. That means that anyone capable of introducing a backdoor into BitLocker could probably introduce a something similar into the Windows operating system to provide access to your files anyway.
Paul Rubens has been covering enterprise technology for over 20 years. In that time he has written for leading UK and international publications including The Economist, The Times, Financial Times, the BBC, Computing and ServerWatch.




