Key Takeaways
- VLANs enable logical partitioning of networks, improving security and performance by isolating traffic into separate broadcast domains. (Jump to Section)
- Advantages include enhanced network performance, reduced latency, improved security, and simplified device management, making them essential for efficient network operations. (Jump to Section)
- Types include port-based, protocol-based, and MAC-based VLANs, each serving specific purposes like managing device functions or isolating traffic based on protocol. (Jump to Section)
A VLAN (Virtual Local Area Network) is a logical grouping of devices that are all connected to the same network regardless of physical location. VLANs are an essential component of contemporary networking, allowing network traffic to be segmented and managed.
VLANs enable logical partitioning inside a single switch, resulting in multiple virtual local area networks where physical switch segmentation is not a possibility. These partitions enable the division of a large network into smaller, more manageable broadcast domains, thereby improving network security, efficiency, and flexibility. In this comprehensive guide, we will look at how VLANs function, when to use them, the benefits and drawbacks they provide, and the types of VLANs.
- How Do VLANs Work?
- When to Use a VLAN
- Advantages of VLANs
- Disadvantages of VLANs
- Common Types of VLANs
- Bottom Line: VLANs
How Do VLANs Work?
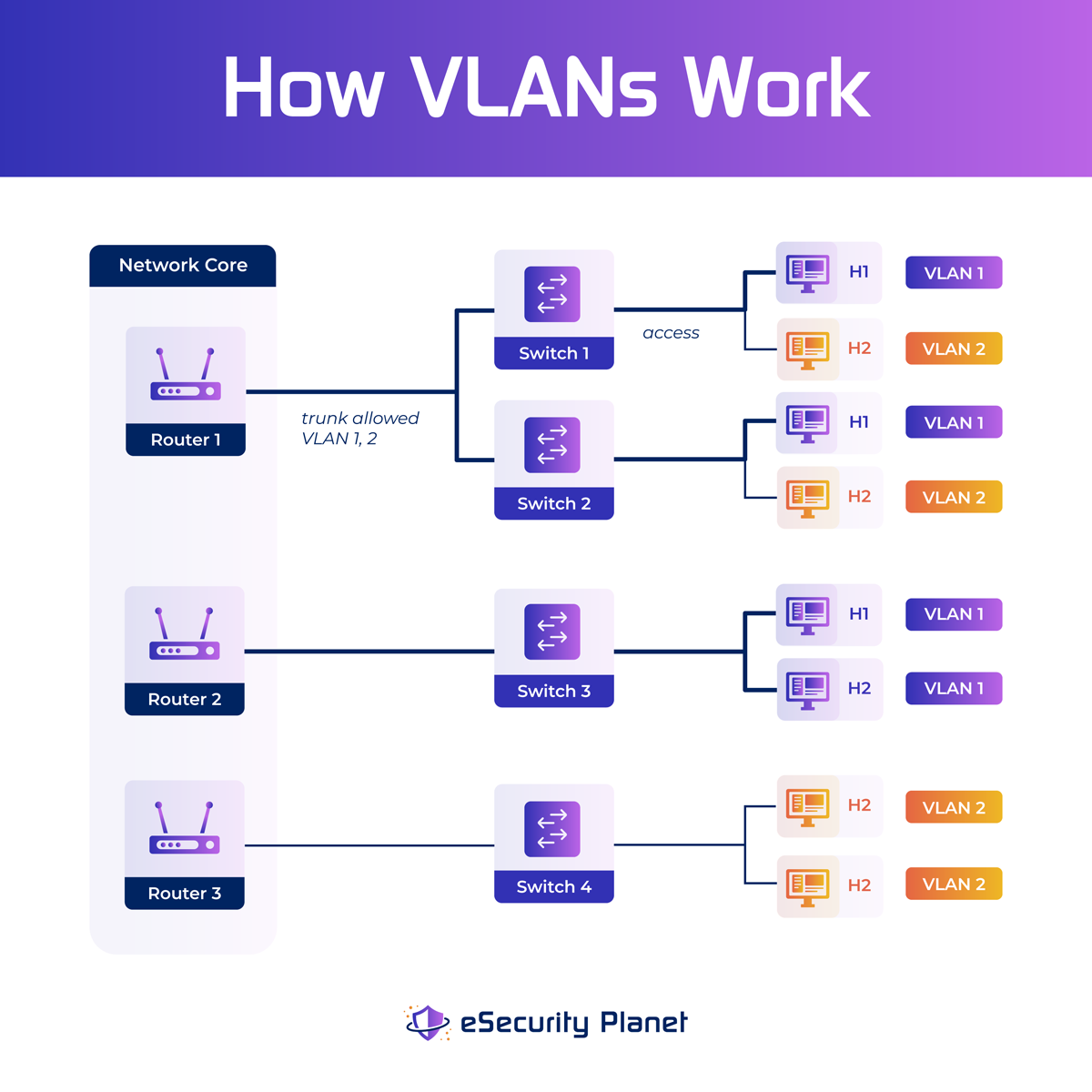
VLANs are assigned unique numbers, which enable network administrators to arrange and separate network traffic. A VLAN number is a label or tag that is applied to certain packets in order to determine their VLAN classification. The valid VLAN number range is typically 1 to 4094, providing adequate flexibility to build many VLANs within a network configuration.
VLAN numbers are assigned to switch ports to associate VLAN membership with network devices. The switch then permits data to be transmitted across ports that are part of the same VLAN. Network administrators can regulate the flow of traffic within the network by establishing VLAN membership for particular ports. By giving the right VLAN number to each port on a VLAN switch, ports may be identified as belonging to a certain VLAN. VLAN tagging, which adds a tiny header to Ethernet frames, is used by switches to identify the VLAN to which the frame belongs. This tagging guarantees that traffic is channeled correctly inside the VLAN and does not leak to other VLANs.
Since practically all networks include more than one switch, VLANs provide a means to transport traffic between them. After assigning VLAN numbers to switch ports, the switch ensures that data destined for devices in the same VLAN is transferred correctly. When two or more ports on the same switch are assigned the same VLAN number, the switch permits communication between those ports while isolating traffic from other ports. This segmentation improves network security, performance, and administration capabilities.
Because most networks are bigger than a single switch, it is necessary to facilitate communication across VLANs on various switches. A simple way to accomplish this is to configure particular ports on each switch to be part of a common VLAN and to make physical connections (usually through cables) between these designated ports. Switches enable inter-VLAN traffic to flow by connecting these ports, allowing communication between devices in different VLANs.
Also read: How to Implement Microsegmentation
When to Use a VLAN
VLANs provide several advantages in network management, performance enhancement, and security. They offer the flexibility and control required in enterprise network settings, whether it is the logical separation of devices based on function, the creation of isolated guest networks, the prioritization of critical traffic, or the optimization of large-scale networks. VLANs are particularly useful in situations such as:
- High-traffic environments and networks with over 200 devices: VLANs provide efficient traffic flow and easier administration by effectively controlling and arranging a large number of devices.
- Optimizing network performance in high-traffic LANs: Congestion may be decreased by splitting traffic into distinct VLANs, resulting in smoother data transfer and lower latency. This improvement enables more effective network resource utilization and increases overall network efficiency.
- Creating multiple switches from a single switch: Network managers can create independent broadcast domains by segmenting ports into various VLANs, thus splitting a single switch into many logical switches. This separation increases network performance, security, and administration.
- Adding security measures and controlling excessive broadcast traffic: Separating groups into separate VLANs increases security while reducing performance difficulties caused by excessive broadcast traffic.
- Prioritizing voice and video traffic: For real-time communication applications, this segmentation assures quality of service (QoS). VLANs reduce latency and packet loss by prioritizing this sort of traffic, improving the overall user experience and ensuring seamless communication.
- Creating isolated guest networks: VLANs prevent unauthorized access and associated security issues by isolating guest devices from the internal network. This isolation guarantees that visitors have access to the resources they require while safeguarding the internal network’s integrity and security.
- Separating logical devices: VLANs allow devices to be logically separated based on their purpose, department, or security needs. Network administrators can enhance network performance and security by grouping devices with similar tasks or security requirements into VLANs. This segmentation decreases broadcast traffic, safeguards against potential security breaches, and enables focused administration and control.
- When simplifying network management: VLANs are critical in constructing virtual networks that transcend physical servers in virtualized and cloud computing environments. This adaptability simplifies network administration, increases scalability, and allows for more effective resource consumption. VLANs in these contexts provide smooth connectivity between virtual computers and assist enterprises in managing their infrastructure more efficiently.
See how one managed service provider used VLANs to protect backups from ransomware: Building a Ransomware Resilient Architecture
8 Advantages of VLANs
VLANs enable enterprises to improve network efficiency, scalability, and security while also simplifying network administration, increasing security, and boosting overall performance. Here are some of the advantages of using VLANs.
- Logically segment networks: VLANs allow for the logical segmentation of networks and the administration of geographically scattered sites. Administrators may efficiently manage network resources, apply specific security measures, and guarantee seamless communication across locations by building distinct VLANs for various sites or departments.
- Improve network security: By logically grouping devices and separating network traffic, VLANs create an extra layer of network security. Network administrators may manage access and ensure that sensitive information remains segregated by defining different VLANs depending on departments, project teams, or roles. VLANs keep unauthorized users out of restricted regions and provide a strong security foundation for safeguarding valuable data, similar to zero trust concepts.
- Increase operational efficiency: VLANs provide operational benefits by allowing administrators to modify users’ IP subnets using software rather than physically changing network equipment. This flexibility simplifies network maintenance, minimizes downtime, and improves the network infrastructure’s overall agility.
- Enhance performance and decrease latency: VLANs improve network performance by lowering latency and increasing total data transmission rates. VLANs prioritize traffic flow inside each VLAN by segmenting networks depending on functional needs, guaranteeing effective network resource usage, quicker data transfer and a better user experience.
- Reduce costs and hardware requirements: By maximizing the existing network infrastructure, VLANs remove the need for extra physical hardware and wiring. This reduction in hardware needs saves money while also simplifying network management and maintenance.
- Simplify device management: VLANs make device administration easier and more efficient by letting administrators organize devices based on their function or purpose rather than their physical location. This logical grouping simplifies device configuration, monitoring, and troubleshooting.
- Solve broadcast problems and reduce broadcast domains: When a network is partitioned into many VLANs, broadcast traffic is confined within each VLAN, preventing it from congesting the whole network. This separation decreases broadcast storms while also increasing network efficiency and overall performance.
- Streamline network topology: Typical network structures may need complex setups that include several switches, routers, and connections. By implementing VLANs, network topology can be simplified, resulting in a reduced number of devices. VLANs organize network devices conceptually, decreasing the complexity of physical connections and increasing network scalability.
Also read: Network Protection: How to Secure a Network
7 Disadvantages of VLANs
While VLANs provide substantial benefits in network management and security, it is critical to understand their potential downsides. Understanding these drawbacks allows network managers to handle them proactively and guarantee a successful VLAN implementation that meets their unique organizational needs.
- Additional network complexity. The additional network complexity caused by VLANs is one of the key problems of adopting them. VLAN management in bigger networks may be a difficult operation that involves precise design, configuration, and constant monitoring. Misconfigurations can lead to network instability or even outages if correct knowledge and documentation are not used.
- Cybersecurity risks. If an injected packet succeeds in breaching a VLAN’s borders, it could jeopardize the network’s integrity and security. Furthermore, a threat emanating from a single machine within a VLAN has the ability to propagate viruses or malware throughout the whole logical network, demanding strong security measures. Further segmentation and zero trust controls could limit any damage.
- Interoperability concerns. Different network devices, particularly those from different suppliers, may have inconsistent compatibility with VLAN technologies, making smooth integration and consistent functioning problematic. Before establishing VLANs in such situations, it is critical to guarantee compatibility and undertake extensive testing.
- Limited VLAN traffic relay. Each VLAN runs as its own logical network, and VLANs cannot forward network traffic to other VLANs by default. While this isolation provides security benefits, it might cause problems when communicating between VLANs. To enable traffic routing between VLANs, further setup and the usage of Layer 3 devices are necessary, adding complexity to network architecture and operation.
- Possible risk of broadcast storms. Improper VLAN configuration can lead to broadcast storms, which happen when too much broadcast traffic overwhelms the network infrastructure. To avoid these disruptive incidents, VLAN design and setup must be carefully considered.
- Reliance on Layer 3 devices. When Layer 3 devices have problems or become overloaded, it can have a major impact on VLAN connectivity. Layer 3 equipment, such as routers or Layer 3 switches, are widely used in inter-VLAN connections. These devices are in charge of routing traffic between VLANs, and their availability and correct setup are critical for VLAN operation.
- Unintentional packet leakage. Packets can mistakenly leak from one VLAN to another in rare instances. This leakage might arise as a result of incorrect setups, poor access control, or insufficient network segmentation. Packet leakage jeopardizes VLAN security and isolation, exposing critical data to unauthorized users.
See the Top Microsegmentation Software
3 Common Types of VLANs
There are several types of VLANs commonly used in networking.
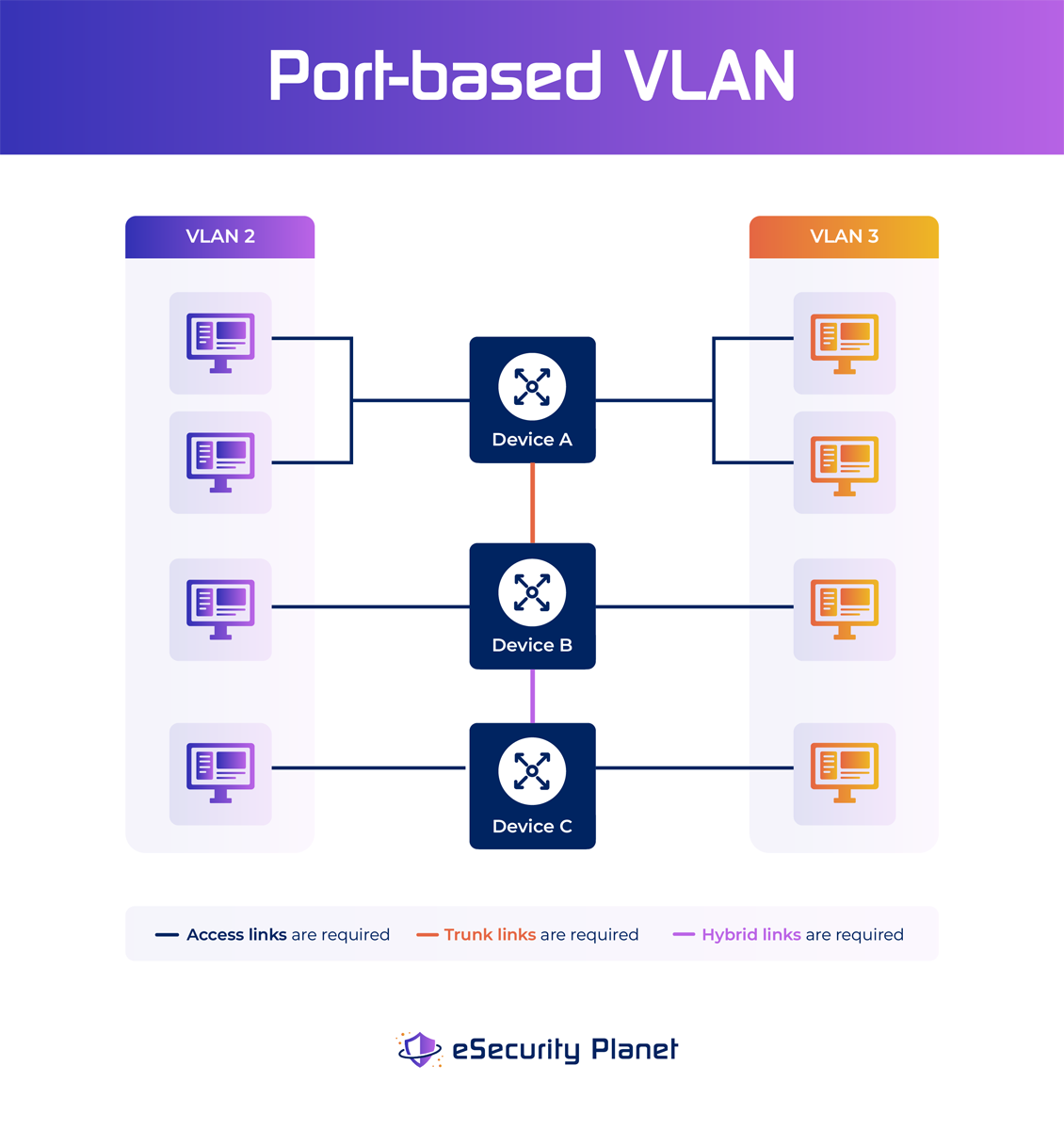
- Port-based VLAN: In this type of virtual LAN, a switch port can be manually assigned to a VLAN member. Specific VLANs are assigned to switch ports, and devices connecting to those ports become part of the corresponding VLAN. Because all other ports are configured with an identical VLAN number, devices connecting to this port will belong to the same broadcast domain. The difficulty with this form of network is determining which ports are acceptable for each VLAN. The VLAN membership cannot be determined simply by inspecting a switch’s physical port but by looking at the setup information.
- Data VLAN: This type is often known as a user VLAN, and is dedicated solely to user-generated data. Data VLANs are designed to isolate and organize network traffic based on device function, department, or security requirements. The organizational structure of data virtual LANs is used to classify them. It is strongly encouraged to properly evaluate how users could be appropriately classified while taking into account all configuration choices. These clusters might be departmental or work-related. Administrators can boost network efficiency and security by grouping devices with similar tasks or security needs into Data VLANs to reduce broadcast traffic, isolate security vulnerabilities, and facilitate network monitoring and control.
- Default VLAN: Typically, default VLANs are allocated to switch ports that have not been expressly defined for any specific VLAN. They serve as a backup alternative for devices that lack VLAN designations. Administrators can guarantee that devices without explicit VLAN assignments remain operational and can interact inside the network by selecting a default VLAN.
- Native VLAN: An access port, also known as an untagged port, is a switch port that carries traffic for a single VLAN, whereas a trunk port, also known as a tagged port, carries data for several Virtual LANs. Native VLANs are linked to trunk lines, which connect switches. These VLANs are untagged on the trunk link, which means that frames sent across the link do not contain VLAN tags. When traffic arrives on a port without a VLAN tag, it is assigned to the Native VLAN; however, it is critical to set the Native VLAN consistently on both ends of the trunk connection to avoid connectivity difficulties and potential security risks.
- Management VLAN: Management VLANs are VLANs that are dedicated to network administration and management responsibilities. This particular type is recommended for the most sensitive management activities, such as monitoring, system logging, SNMP, and so on. This not only provides security benefits, but also provides capacity for these management duties even in high-traffic scenarios. Administrators may assure safe access to network devices, ease network monitoring and troubleshooting, and protect key network infrastructure from illegal access or interference by isolating management traffic onto a distinct VLAN.
- Voice VLAN: Voice VLANs are designed to prioritize and handle voice traffic in a network context, such as Voice over IP (VoIP) calls. Network administrators can assure Quality of Service (QoS) for real-time communication by allocating voice devices to a distinct VLAN, minimizing latency or packet loss issues that may affect the user experience during voice calls.
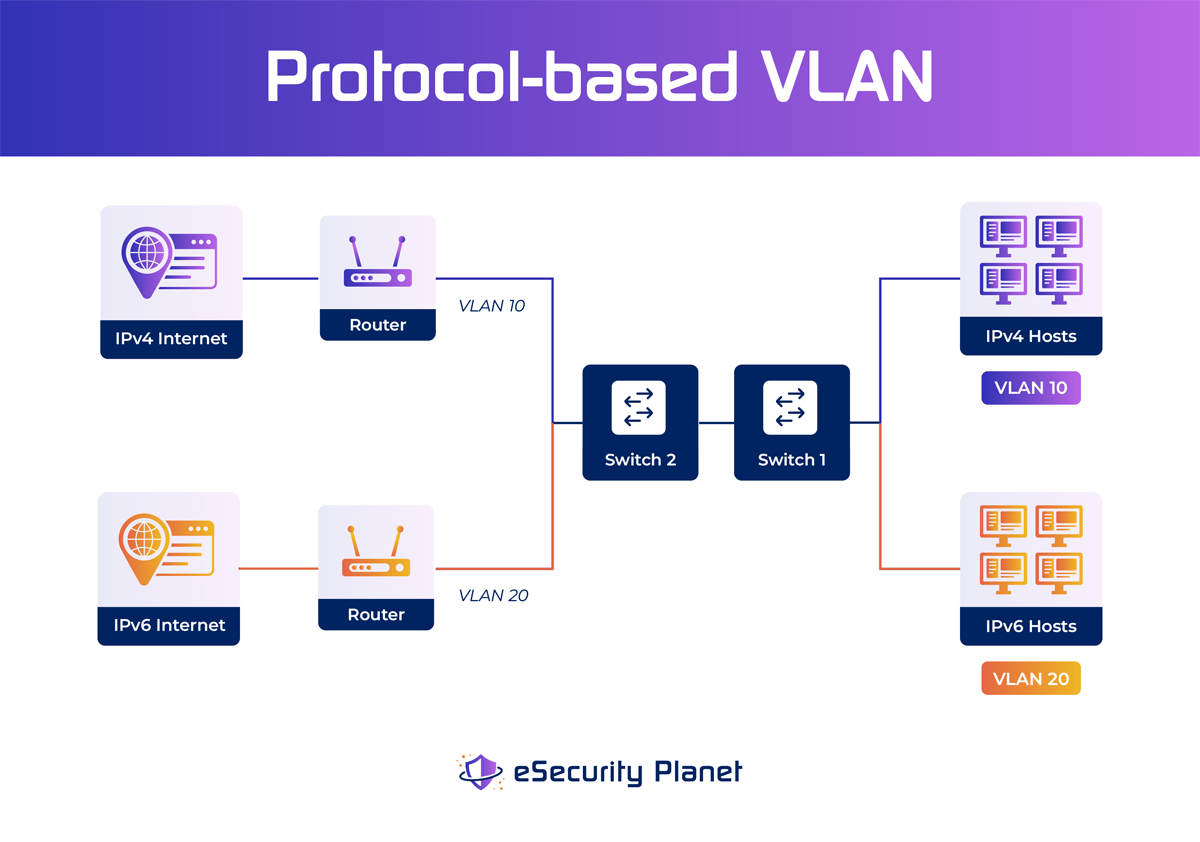
- Protocol-based VLAN: Protocol-based VLANs classify VLAN membership according to the traffic protocol in use. In a Protocol-based VLAN, the frame contains the layer-3 protocol information that specifies VLAN membership. While this method is effective in multi-protocol environments, it may not be feasible in IP-only networks. Other protocols’ traffic, such as IP, IPX, or AppleTalk, can be routed to their respective VLANs. This form of VLAN filters traffic based on protocol and offers untagged packet criteria.
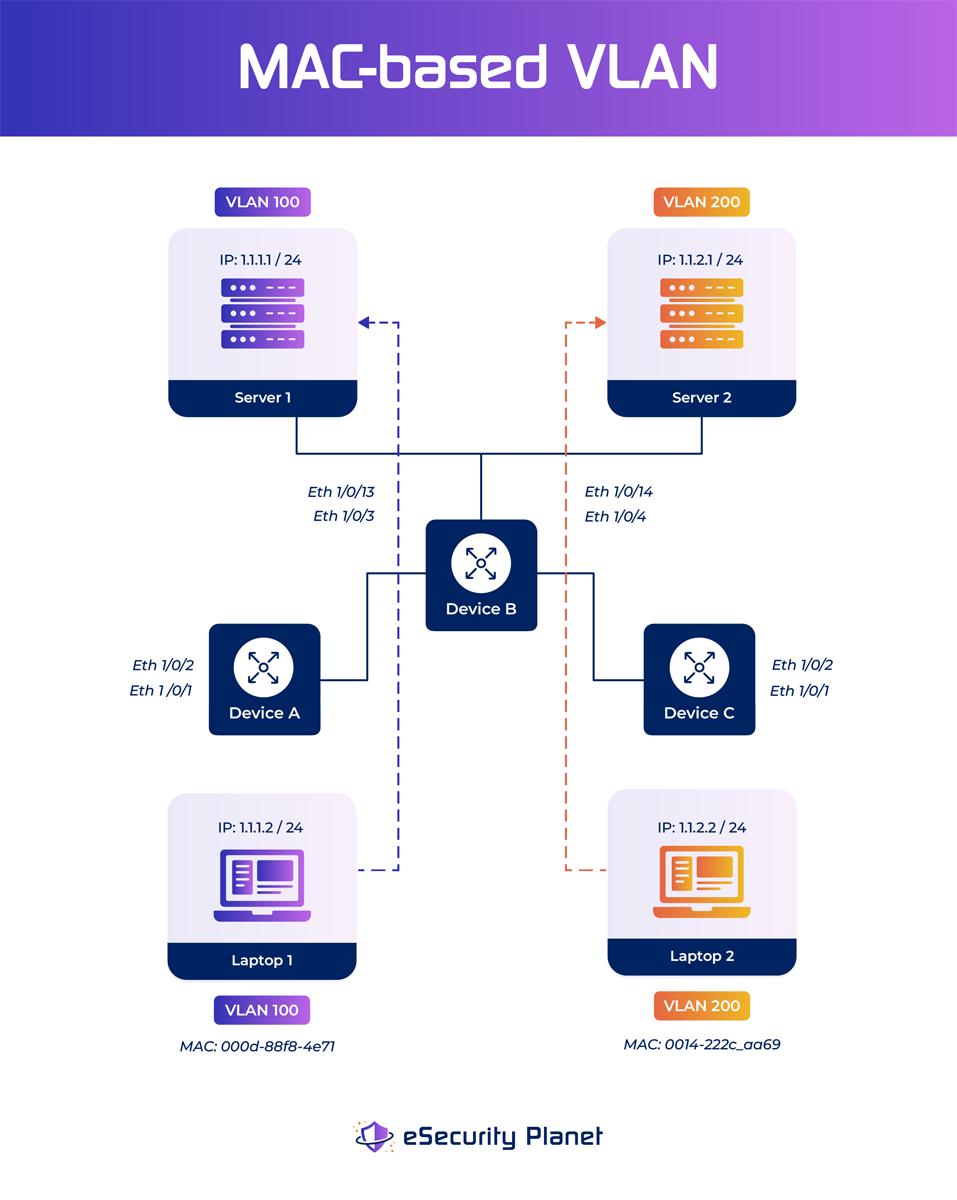
- MAC-based VLAN: This type of VLAN is ideal when network administrators require granular control over device placement. A MAC-based VLAN uses the MAC address of a device to identify it as a member of that VLAN. Each VLAN on the switch has its own MAC address. This type of VLAN is typically used when device segmentation by MAC address is necessary. Untagged inbound packets are allocated virtual LANs through the use of MAC-based VLANs, allowing traffic to be categorized depending on the source address.
See the Best Next-Generation Firewalls (NGFWs)
Bottom Line: VLANs
VLANs are a powerful network strategy that enables efficient traffic control, better security, and optimal network performance. These are critical functions in modern network environments, allowing network traffic to be segregated and controlled. By assigning VLAN numbers to switch ports, network administrators may create logical network segments and regulate data flow inside and between VLANs.
VLANs provide the flexibility and control required in contemporary network settings, whether it is the logical separation of devices based on function, the creation of isolated guest networks, the prioritization of critical traffic, or the optimization of large-scale networks. Understanding the functions and advantages of VLAN types helps administrators to create efficient network configurations tailored to their organization’s needs.
Read next:




