-
7 Steps of the Vulnerability Assessment Process Explained
A vulnerability assessment is one of the most important pieces of an enterprise’s vulnerability management lifecycle because you can’t fix security vulnerabilities you know nothing about. Through the vulnerability assessment process, networks and assets are scanned and newly discovered vulnerabilities are analyzed and scored based on risk. With completed vulnerability assessments, cybersecurity and vulnerability specialists […]
-
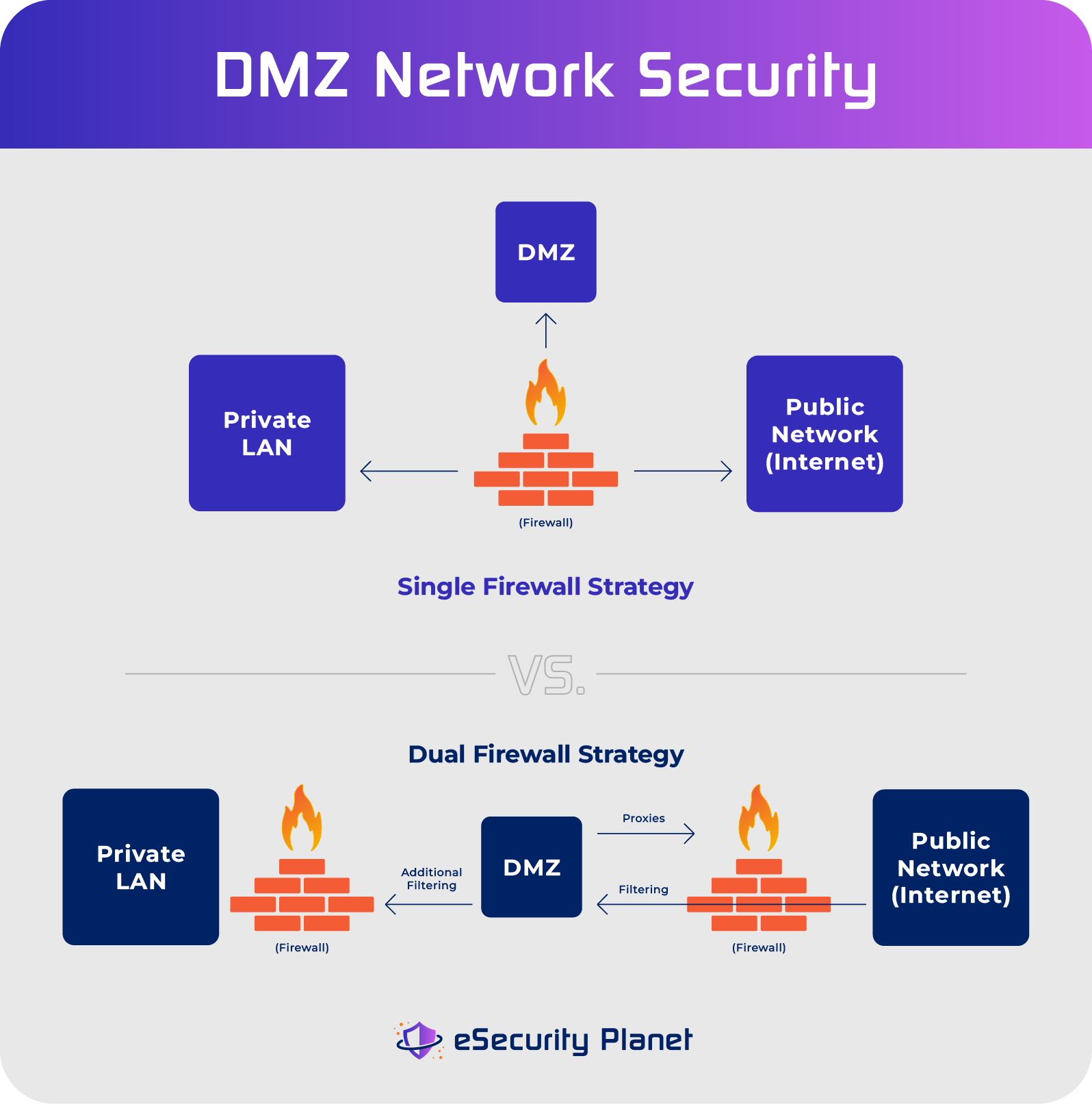
What Is a DMZ Network? Definition, Architecture & Benefits
A DMZ network, or a demilitarized zone, is a subnetwork in an enterprise networking environment that contains public-facing resources — such as web servers for company websites — in order to isolate them from an enterprise’s private local area network (LAN). Also referred to as a perimeter network or screened subnet, a DMZ network acts […]
-
34 Most Common Types of Network Security Solutions
Whether you’re operating a global enterprise network or a small family business, your network’s security needs to be optimized with tools, teams, and processes to protect customer data and valuable business assets. Network security is an umbrella term for all facets of your network’s cybersecurity posture, with an emphasis on developing and using policies, procedures, […]
-
Vulnerability Management: Definition, Process & Tools
As enterprise networks continue to grow in size and complexity, so have the misconfigurations and vulnerabilities that could expose those networks to devastating cyber attacks and breaches. Vulnerability management is the process of prioritizing and minimizing those risks. When you consider that the average Fortune 500 company has nearly 500 critical vulnerabilities, the importance of […]
IT Security Resources
Top Cybersecurity Companies
Top 10 Cybersecurity Companies
Get the Free Newsletter!
Subscribe to Cybersecurity Insider for top news, trends & analysis