Ransomware just keeps getting worse, it seems. Cybersecurity researchers last week revealed that a new ransomware gang called Onyx is simply destroying larger files rather than encrypting them.
As the MalwareHunterTeam noted in a Twitter thread, “as the ransomware they are using is a trash skidware, it’s destroying a part of the victims’ files.”
The team would recommend that “no company should pay to these idiots … but they are stealing files too.”
Most threat actors have been focused on locking data, sometimes with innovative techniques to evade detection tools. The idea is to force the victims to pay the ransom in return for the stolen data.
The Onyx ransomware group doesn’t bother with encryption. Any file larger than 2MB, which is pretty common in enterprises, is simply destroyed. Unlike with other ransomware strains, you can’t recover documents with a decryption key.
Such a low size limit will include most files on the victims’ computers. Besides, if the motive is money, as you would expect from a ransomware group, then the approach seems questionable. Why would companies pay a ransom if they know they won’t be able to recover most files?
Coming the same week that the REvil ransomware group apparently returned, these are tough times for cybersecurity pros.
Also read: Best Backup Solutions for Ransomware Protection
Analyst: Don’t Pay Onyx Ransom
MalwareHunterTeam posted a code sample on Twitter:
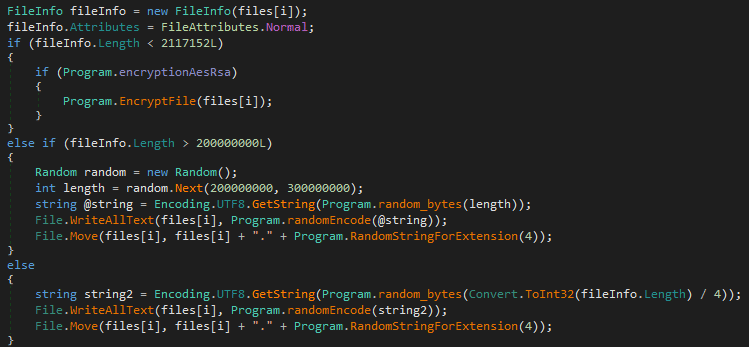
The hackers use the above .NET code to overwrite any file bigger than 2MB with junk data. Only small files lower than 2MB are encrypted. The rest of the files are overwritten with random trashed data, so there’s no way to decrypt them after.
It was a bit unclear whether this behavior was the initial plan or the result of a bug in the implementation, but Jiří Vinopal, Forensic and Malware Analyst, Reverse Engineer at CERT, tweeted that the Onyx ransomware is likely based on the Chaos ransomware builder that systematically overwrites big files:
“One note added by @malwrhunterteam and already confirmed that it works like this:
1 – for small files.
2 – for big files.
3 – for between the two. In encrypt mode, small files encrypted, others overwritten. In overwrite mode, small files not touched-skipped, others overwritten.”
Therefore, it’s safe to assume it was intentional and the victims should not pay the ransom, as it won’t solve the problem and the extortion might even continue after payment.
Also read: Best Ransomware Removal Tools
Similar to Conti Ransom Note
Two years ago, the Conti ransomware group disclosed stolen data even if the victims paid the ransom.
MalwareHunterTeam noticed the instructions left by Onyx for their victims are “mostly a copy-paste of Conti’s note,” sharing the following example:
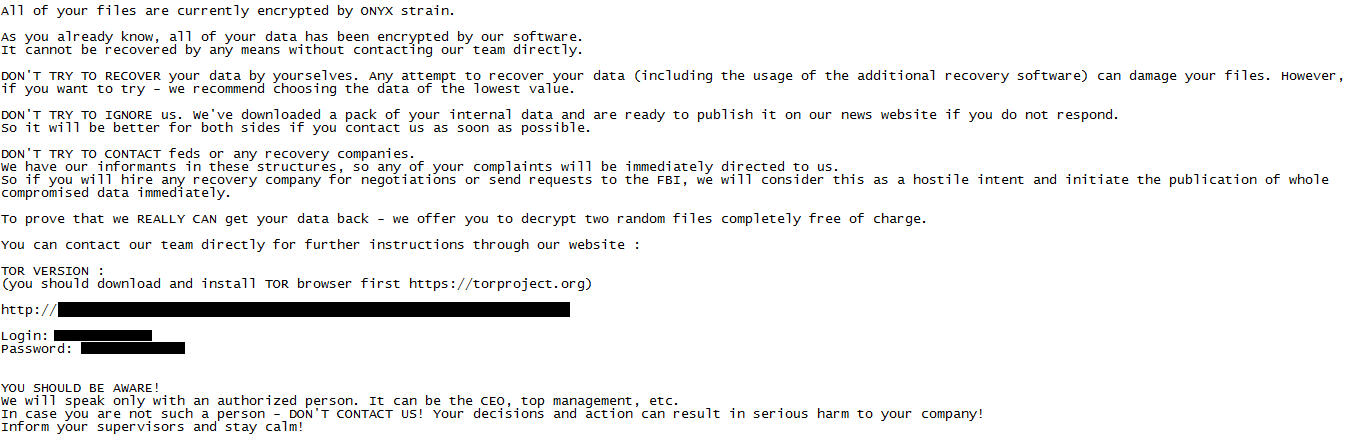
The hackers offer to decrypt “two random files completely free of charge” to prove they “really can get the data back.” But unless you’re doing some hunting and know what you’re doing, don’t visit their website with Tor and don’t connect with the credentials they provide in the note. Otherwise, you might wind up with additional problems.
The hackers describe their new strain as a “military-grade algorithm” to impress their victims, but that’s clearly not the case.
However, MalwareHunterTeam found six other organizations pwned by Onyx on their onion website (section “Onyx news”), so despite the impossibility of data recovery, you should take the threat seriously.
So far, the Onyx strategy remains unclear, and it’s possible that this destructive program is the only weapon the ransomware group has for now.
The MalwareHunterTeam found that the hackers not only encrypt and destroy files, but they also steal data to threaten their victims with potential public disclosure. This tactic is not really surprising, as such “double threats” are now pretty common in ransomware attacks.
Indeed, in case the ransomware fails to encrypt and lock data (or, in this case, destroy it) the attackers nonetheless can still threaten their target to get paid. The victims should expect some data leaks.
Also read: How to Recover From a Ransomware Attack
How to Protect Against Destructive Ransomware
While it’s pretty hard to determine all of the group’s motives, their destructive approach could disrupt the threat landscape in 2022.
While most victims of ransomware attacks never recover their data even when there’s a so-called “decryptor” in exchange for money, this attack could be the beginning of a new paradigm where using decryption keys as leverage does not make sense anymore for threat actors.
Ransomware removals and security tools make ransomware attacks ever more difficult to achieve, which might explain, at least partly, why they prefer destroying files. Besides, it can be used to threaten companies with further attacks, so if they don’t pay the ransom, they’ll certainly lose more data – and have it publicly exposed.
The only way to mitigate such devastating attacks is to prepare for post-exploitation techniques and lateral movements. This would require classic security hygiene and awareness, endpoint monitoring, network segmentation, patch management and regular backups, but only as a start.
Companies should prepare for ransomware attacks with efficient backup routines that will protect the data from ransomware attacks.
Backups can be corrupted or deleted by the hackers, so you need penetration tests to emulate real attacks and fix any flawed procedure. Versioning and rollbacks are also strongly recommended.
In addition, you might use specific software to distribute backups or use separate cloud accounts for each desktop to contain the destructive malware.
Remember that ransomware is not just for big companies. Many small businesses have filed for bankruptcy after a ransomware attack. Even if the hacker knew the victims could neither pay the ransom nor lose the data, they still attacked without mercy.
CISA has a website devoted to fighting ransomware attacks. That’s a good place to start to assess your situation and prepare your organization for ransomware events.





