Table of Contents
Finding potential targets
First, a hacker will want to see what wireless networks are out there. One way to find them is called war driving, which is easier than it sounds. All that’s needed is a free program called inSSIDer. This scans the airwaves and displays a list of nearby wireless access points (APs). As Figure 1 shows (below), some APs are displayed with an SSID (the network name) and some without.
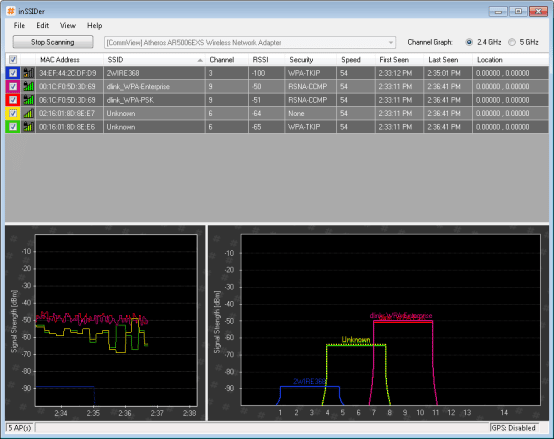
Defining and discovering hidden networks
The APs missing their SSIDs have been intentionally set via their Web-based control panels to not broadcast their network name in the beacons. The home user or network administrator who manages these networks might believe that not broadcasting the SSID hides his or her WLAN and therefore considers this the first layer of defense against Wi-Fi hackers. However, you (or anyone with the desire) can usually find the concealed SSID quickly. This calls for another program, easily attained–a wireless network analyzer, such as CommView for Wi-Fi. Though it’s a commercial product, its free evaluation version will suffice.
Once a hacker opens CommView for Wi-Fi, she starts capturing on the channel of the “hidden network” she’s targeting. She may see only a blank SSID. However, as soon as someone on the network attempts to connect, the supposedly hidden network name will appear. The SSID is also in probe packets, which will likely be continuously broadcasted from the computers and APs on the target network, so the hacker won’t have to wait long for the big reveal.
See Figure 2 (below) for an example, which shows the same two hidden networks from Figure 1.
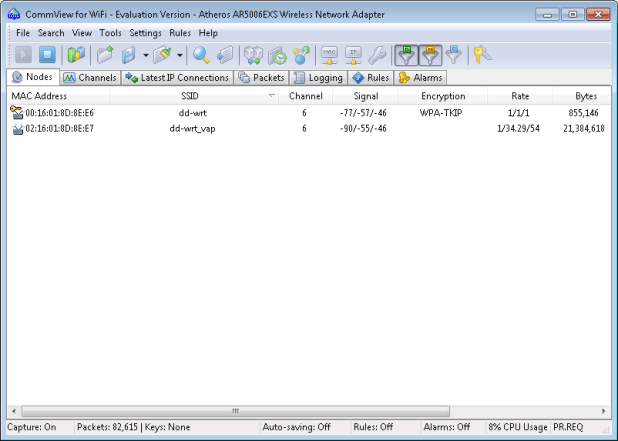
Both residential and business networks are equally vulnerable. A hacker can typically detect the names of “hidden networks” very quickly and easily, even if wireless encryption is used. While the name alone isn’t much of a prize, it brings the hacker one step closer to her goal.
Cracking the wireless encryption
The next layer of protection a hacker must often defeat is wireless encryption, such as WEP, WPA, or WPA2. When searching for targets, a hacker will see networks both with and without encryption. Those networks without encryption are very vulnerable. Almost anyone could probably connect in a few seconds. These are usually home connections broadcast by users who either don’t know about encryption or don’t care, but sometimes even businesses leave themselves wide open. Hackers can use these connections for free Internet access, either for casual browsing or as a means of launching Internet-based hacking attacks.
For those networks with WEP encryption, a good hacker can usually crack them within a reasonable amount of time, some within minutes. The ability and amount of time it takes to crack depends upon the WEP key length and complexity, how much the network is being used, and the cracking techniques employed. The newer PTW hacking technique is much faster than most older techniques.
A hacker might also take a stab at cracking networks protected with the simpler or personal form of WPA or WPA2 encryption using pre-shared keys (PSK). The success of these attacks is all up to the simplicity (or complexity) of the passphrase used.
To get started cracking WPA/WPA2-PSK, a hacker only has to capture one client association (someone successfully connecting to the network). Then she can use dictionary-based attacks, trying to guess the passphrase. If the passphrase is simple and is contained in her dictionary, she’ll eventually crack the encryption. Hackers use dictionaries with hundreds of millions of words. Though this would take forever on your own PC, hackers have the ability to use outsourced super computers, such as WPA Cracker.
Some networks, usually in larger businesses or organizations, use the enterprise mode of WPA or WPA2 encryption using the Extensible Authentication Protocol (EAP) and 802.1X. These won’t have passphrases or PSKs to crack, but these are susceptible to man-in-the-middle attacks.
To get started hacking WPA/WPA2-Enterprise, a hacker would set up a fake AP matching the SSID and security settings of the target network and would then run a modified RADIUS authentication server. She’d try to get users to connect to her fake setup and attempt authentication, which requires that the client EAP settings have been set insecurely and that the bogus network is cleverly disguised enough to convince users to connect to it.
If everything does go according to plan, our hacker will capture usernames right away. For the passwords, she’ll have to run a dictionary attack. If the password is relatively simple, she’ll have everything she needs to connect to the target network.
Spoofing your MAC address
Another security technique some people use is MAC address filtering. Each computer and device contains a unique MAC address, thus the network administrator can create a black and white list of addresses he or she wants to block or to allow onto the network. This can be used with or without wireless encryption or the hidden network technique.
If a hacker suspects a target network is using MAC address filtering, she’d just have to bring up a wireless surveying or analyzer program on her laptop; she could use CommView for Wi-Fi again. She would simply check out the list of stations (such as Figure 3 shows) or monitor the raw data packets to find a “good” MAC address that she could use.
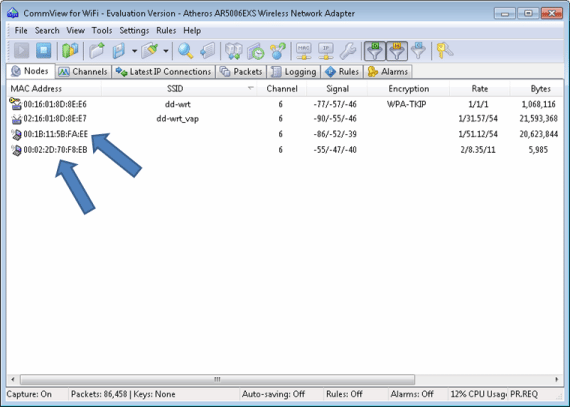
Once a hacker has a MAC address she can emulate, in Windows, she would just bring up the network adapter’s properties dialog and type in the address, such as Figure 4 shows (below). In this way, the hacker won’t be stopped by the MAC address filter.
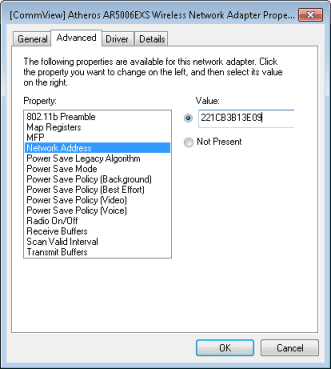
Let the fun begin
Once a hacker has found an open network or has successfully hacked one, she can try to access files and/or snoop on the network traffic, for example, to capture passwords used by users.
If she’s lucky, the users have placed files in the public shares. If she’s really hit pay dirt, she might find some sensitive documents containing goodies like banking info or other top secret stuff.
To capture e-mail, Website, and other passwords, a hacker can run a special sniffer. EffeTech HTTP Sniffer and Ace Password Sniffer are two commercial products that offer a free trial.
Lessons learned
Now that we’ve examined exactly what a hacker needs to get what she wants, it’s easier to see what every network administrator should know. Here are seven tips summarizing what you’ve learned and how it can help you better secure your Wi-Fi network:
-
Disabling SSID broadcasting doesn’t deter hackers, plus it can give you a big headache when configuring your network and causes an increase in network traffic (probes request and responses).
-
Don’t use WEP encryption, it’s useless.
-
WPA/WPA2-PSK encryption is still secure when using long complex mixed character passphrases.
-
WPA/WPA2-Enterprise encryption is even more secure if you properly set the client settings (validate the server, specify server address, don’t prompt for new servers, etc.) and assign complex passwords.
-
Try to use WPA2 (with AES/CCMP) encryption only.
-
MAC address filtering may help control the computers or devices brought in by users, but is not a realistic deterrent against hackers.
-
For additional control over end-user connectivity, consider implementing a Network Access Control (NAC) or Network Access Protection (NAP) solution.
Eric Geier is the Founder and CEO of NoWiresSecurity, which helps businesses easily protect their Wi-Fi with enterprise-level encryption by offering an outsourced RADIUS/802.1X authentication service. He is also the author of many networking and computing books for brands like For Dummies and Cisco Press.








