Are you a visual learner or a verbal one? Consider the last time you had to change a password from a short, dictionary word like dogs to a longer, multi-character one like Eq_7A6>6fc8c. How were the instructions given and which ones helped you understand the parameters for acceptable passwords? Did verbal instructions like:
- The password must be 12 characters in length;
- Not be found in a dictionary;
- And contain:
- Upper and lowercase symbols
- At least 2 numbers
- At least two symbols
Help you understand how to create an acceptable password? Or did examples like:
- Acceptable: Ip=
- Acceptable: AuO=?2Y{@TDl
- Unacceptable: GooglePhone
- Unacceptable: G00GL3F0N
Make more sense to you?
The answer probably depends on which kind of learner you are. For some of us, seeing a concept depicted graphically is the best way to comprehend and retain it. For others, it’s the words that matter. And for still others, it’s a combination of the two. Regardless of what kind of thinker and learner you are, keep in mind that when you or your team are presenting a complex security topic to an audience of business unit owners, executives, and other non-technical professionals that there’s a strong chance that your audience will be comprised of thinkers and learners from all camps. That’s why it’s critical to present complex security concepts in both styles to ensure maximum communication effectiveness with your audience. In the next two sections, we’ll use justifying a change in password policy as a baseline and supply some examples on how to ensure that the information connects with both kinds of thinkers.
Verbal Communication
The Orientation to College Teaching at San Francisco State University characterizes verbal learners as those that respond to words like “see, look, and observe” and prefer to read what an expert has to say. To justify changing a corporate password policy from short dictionary words changed every 15 days to longer multi-character words changed every 90 days, reach out to these constituents with data: words, numbers, and expert information. For this audience, bullet point lists of a process may be more useful than flow diagrams.
Example 1:
Rather than saying “longer passwords are more secure” justify this statement with supporting research like, “The NIST Electronic Authentication Guidelines and Guide to Enterprise Password Management (Draft) specify that longer, multi-character passwords are much harder to guess or brute force due to increased entropy.”
Example 2:
Instead of writing “Help desk calls with go down,” quantify the statement with data; “Currently, the help desk receives 10 password reset calls per month at a cost of $60 per call. Our research indicates the frequency of password reset calls to the helpdesk will be reduced to 2 calls per month under this new policy resulting in a $480/month savings to the company and an annual net savings of $5,760.”
Example 3:
To explain a proposed process, walk through the key action points in a bullet list. Rather than saying, “After the policy change has been accepted, it will be distributed to employees and implemented,” verbally describe each of the steps. The following list enumerates the high-level activities for implementing the new password policy.
Policy review team votes on policy change. If accepted, Revised policy is entered into PolicyWiki and policy section of SharePoint server All employees are notified of policy change and required to sign-off on new policy in policy section of SharePoint server and told about upcoming password change requests All admins are notified of new password requirements and instructed to send out password change notices to all employees SSO servers are configured with new rules to enforce new password policies
Visual/Non-Verbal Communication
Like verbal learners, non-verbal learners also respond to words like “see, look, and observe” but they also respond to “picture and imagine.” Verbal learners “retain information well by looking at pictures, diagrams . . . [and] charts,” and “learn how to do things through observation and modeling rather than verbal explanations” To reach this audience effectively, show the same concepts from the previous two examples in a more visual manner.
Example 1:
Longer passwords, in general, are harder to guess and brute force that shorter ones, but variables like case sensitivity and inclusion of all ASCII characters (letters, numbers, and symbols) impact the length versus strength comparison and overall entropy. In this particular example, we’re not including dictionary v. non-dictionary words in our entropy calculations. For the verbal learners, a chart with numbers will be of use. To make sure it resonates with non-verbal intelligence too, provide examples as we’ve done below. Reviewing the chart, the benefit of using ASCII characters to keep password length down – especially as entropy requirements go up – becomes clear quickly. So also does the difficulty of a typical human being remembering a password made of random characters.
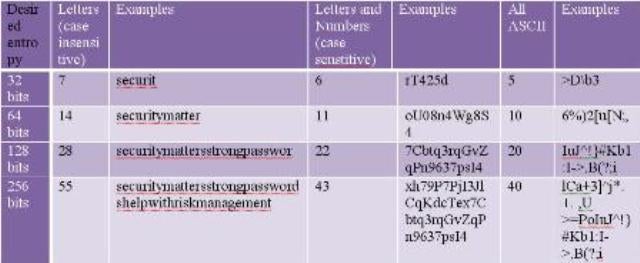
Figure 1Edited from original source at: WikiPedia, Password Strength
Example 2:
Turn the quantifiable data in the help desk call example into charts that visually represents the resource and cost savings. An advantage of including charts is that they present a hybridized verbal and non-verbal view of the information that should resonate with both types of thinkers.
Calls per Month
Annual Savings: $5,760Example 3:
Showing a process in a graphical manner is done using a process flow diagram or a use case model. In this example, we’ve re-structured the numbered steps in the previous example as a UML Sequence Diagram:
There is a third category of learners that we haven’t discussed yet, auditory learners. People who respond best when hearing the information rather than looking at it. In a business environment these learners are usually addressed during formal, oral presentations. But keep in mind that some documents have a life of their own and are distributed without the auditory part of the presentation. If your company has a key constituent that’s an auditory learner, consider attaching a short MP3 walkthrough with important documents.
Diana Kelley is a partner at IT research and consultancy firm SecurityCurve and a frequent contributor to eSecurityPlanet.com.
Keep up with security news; Follow eSecurityPlanet on Twitter: @eSecurityP.








