By Stanislav Breslavskyi and Nazar Tymoshyk, SoftServe
Sooner or later, any expert involved in software or computer systems development and maintenance processes will face security questions. To find solutions, they’ll need security tools.
Let’s define the types of security tools and their roles in different kind of projects and development stages. Picking the right tool may be the key to your security.
Security and Software Development Lifecycle (SDLC)
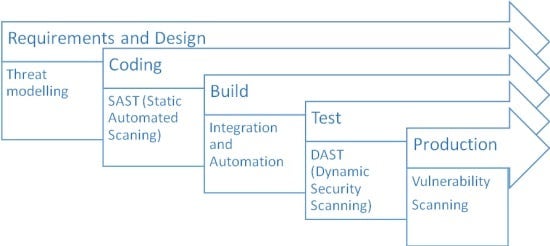
According to the Microsoft Secure SDLC approach, the best way to ensure your system security and significantly reduce your risks of being hacked is to establish security processes from scratch, right at the dawn of the project. Often underestimated, security tools play the core role here. Let’s see what techniques are used at different development stages, according to the Secure SDLC approach:
We can analyze every activity in detail and explain what is actually done at every development stage:
- Threat modeling. Identifying targets and vulnerabilities, defining countermeasures to prevent or mitigate consequences
- SAST. Identifying vulnerabilities in the source code, byte codes or binaries (without running the code)
- Integration and automation. Automation of scanning to perform on a regular basis
- DAST. Examining application on the run (identifying vulnerabilities while running the code and feeding it unexpected values, etc.)
- Vulnerability scanning. Scanning applications for known vulnerabilities such as XSS, SQL injections.
Having defined the main security activities, we can see that activities are rather different at specific development stages, so let’s have a look at the most popular tools to use during security tests. Every tool has its advantages and disadvantages for different projects. If your goal is to select the right tool wisely — and it should be — you should do a little investigation before picking up a scanner.
Even More Security Tools
As you can see from the wide range of tools available, it is not that hard to find one. You might say, “With this set of tools, I will find every single bug in my app and I will be 100 percent secure,” but I have to disappoint you; this assumption is far from truth and it is not the right approach.
Testing and scanning tools have strict limitations. For example, they are useless against REST API applications, they cannot identify sensitive info (personal identifiable information, PII), and they cannot perform chained attacks.
This means that you should seek a specific tool or a set of tools to help you test your app successfully. Try giving a go with sqlmap on your URLs that are processed with the server to access the database, to find out if they are vulnerable to SQL-injection. Use XSS Me to try out cross-site scripting on your input fields and so on.
Here, the range of tools is even bigger. Just look for a tool for specific attacks. (“XML External Entity attack tool,” for example.) To get familiar with the types of attacks and relevant security tools, we recommend getting a distribution of Kali Linux, an OS for penetration testers, with a great set of tools preinstalled.
A great trend is to interweave these “specific” tools into framework. Just try out BDD Security, mittn or gauntlt. Most of them are open source and under active development. They let you build powerful attack frameworks to unite a set of hacking tools which are best suited for you and your project under one roof. You can find more about CI and Security DevOps here.
Tool vs. Hacker
Now having defined all the different kinds of tools and approaches, you can say that you are secure enough. Still, it is not as clear as it may seem, and as it was mentioned before – security scanners, in some cases, are useless and cannot perform complex attacks. The right approach is to use the second group of tools, “specific attack” tools.
And here comes another “but”: The successful use of them requires a security specialist — a so-called “ethical hacker.” Having such a person in your development ecosystem can significantly reduce your risks of being hacked. Also, the Secure SDLC described above requires one to be on the project, as performing penetration tests and scanners configuration requires some experience in the security field to make your scans as efficient as possible.
Choosing Security Tool: Final Thoughts
Choosing the right tool is not so easy. A lot of questions should be posed and many fields are to be researched:
- What technologies and architecture are used?
- What is the current development stage?
- What do you want to actually do, a simple automated scan or a complex penetration test using distinguished tools?
Based on solid experience conducting penetration tests and establishing Secure Development Lifecycles, the right thing to do is to have a dedicated security specialist in you project’s eco-system from the very start of your project to handle all of the possible questions.
Stanislav Breslavskyi and Nazar Tymoshyk are both security engineers at SoftServe Inc. Stanislav’s focus is on network solutions development, specifically security-related development. He is a graduate of the State University, Lviv Polytechnics with a BA in information security. Nazar is an expert in multiple security disciplines including computer forensics, malware analysis and intrusion detection. He holds a Ph.D. in information security from the State University, Lviv Polytechnics. You can read more of their posts on the SoftServe United blog. where they are both regular contributors.